Memories of the LOVE BUG
 Today is the fifteenth anniversary of the infamous LOVE BUG virus.
Today is the fifteenth anniversary of the infamous LOVE BUG virus.
It just about conquered the world’s email servers back in May 2000 because each infected computer would email everybody in its address book.
Actually, it didn’t just email every body, it emailed every address book entry, including mail groups with multiple members.
The silver lining in a malware attack that worked that way is that is became really obvious really soon, being the very antithesis of subtle.
But the bad news is that by the time it was obvious, the world’s email infrastructure had already suffered huge collateral damage, and the malware was everywhere.
The author, Onel de Guzman from the Philippines, was quickly identified and questioned by law enforcement.
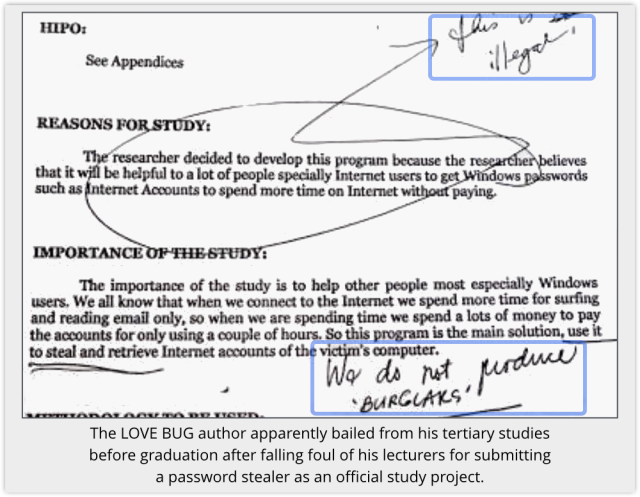
But even though the LOVE BUG not only created damage by spreading, but also tried to download and install a password stealing program, de Guzman evaded prosecution.
What he’d done wasn’t strictly illegal at the time (unless prosecutors had been able to show intent to break other, non-malware-related laws).
The Philippines legislature quickly moved to change that, presumably fearing that without more teeth in the legal code, malware disseminators could continue to shrug their shoulders and get off.
So de Guzman may have brought about a tightening of cybercrime regulations in The Philippines, but he himself slipped the knot and got off scot free.
If you weren’t around at the time, LOVE BUG looked like this:
- Subject line: ILOVEYOU
- Body text: kindly check the attached LOVELETTER coming from me
- Attachment: LOVE-LETTER-FOR-YOU.TXT
Many people opened the attachment out of innocent curiosity, presumably assuming that a .TXT file ought to be harmless, even if it later turned out to come from a crook.
But the filename was actually LOVE-LETTER-FOR-YOU.TXT.vbs, abusing what’s now known as the “double extension” trick.
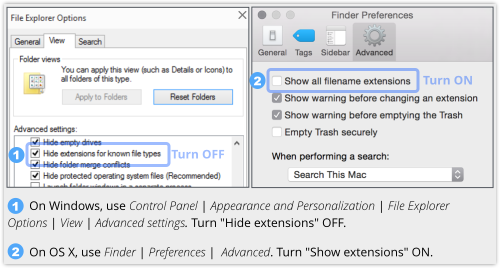
Many operating systems, including Windows and OS X, helpfully suppress the characters after the last dot in a filename, figuring that they just take up space on the screen to convey information that is already in other ways, such as the icon assigned to the file, or the application suggested to open it.
So the text file really was a text file, except that it was a special sort of file: a Visual Basic Script (VBS) program.
In those days, opening the file from Outlook would run the program instead of displaying it, and if your anti-virus didn’t kick in to protect you, the damage was done.
Modern cybercrooks still use this sort of trick, “hiding” the fact that attachments are really EXEs (programs) or various other sorts of file of which we have learned to be suspicious.
And cybercrooks still rely on the simple but effective trick of choosing plausible or intriguing attachments.
They don’t go for love letters so much any more, for which we probably have to thank Onel de Guzman in a backhand sort of way, but they get great mileage from files such as:
• Fake invoices. (You’d better look or else you may get stuck with a bill you don’t owe.)
• Bogus courier deliveries. (You’d better reply or you might miss a delivery.)
• News items in your field of interest. (Crooks can often work out what makes you tick simply from your job title or your Facebook page.)
What to do?
Don’t fall for the modern equivalent of the bogus love letter.
- Block suspicious attachment types (e.g. double extensions) at your mail gateway, just in case.
- Don’t open attachments out of fear or because you’re inquisitive.
- Scan outbound emails as well as incoming, to look for information that shouldn’t be leaving.
- Always show file extensions, because you can.
Outbound scanning for LOVE BUG back in 2000 could have helped you contain a virus outbreak from your own network, which is always a bad look.
In 2015, outbound email scanning can protect you from much worse, such as: spam sent by zombies or bots in your network (which might be stealing passwords and data as well); accidental data leakages through incorrectly chosen email recipients; and even deliberate attempts to bypass your security rules to embarrass your organisation.
Fifteen years ago, there was so much ILOVEYOU going around that to be publicly identified as one of the many victims wouldn’t have made you stand out, and would probably have ended up as an easily-forgiven mistake.
Today, data breaches and infected networks aren’t so readily excused, not least because of regulatory changes that are leaning on all of us to take security and privacy ever more seriously.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/EzQZPKhbwPM/