Payday loan company Wonga breached – what you need to know
Short-term loan company Wonga has just announced a data breach.
According to reports, personal information of approximately 250,000 customers in the UK and 25,000 in Poland was plundered.
Companies like Wonga are generally referred to as “payday loan providers” because customers typically borrow small amounts at high interest rates for short periods, for example to cover an unexpected expense until payday.
Despite the short-term nature of payday loans, you still need to hand over plenty of personally identifiable information, as with any account you open, including your name, address, phone number, bank account number and credit card details.
And, as with any company that operates online these days, you need to create an online account, too, which means coming up with a strong and unique password for that account.
Wonga has creditably put a very visible notice on the main page of its website, linking through to an FAQ page:
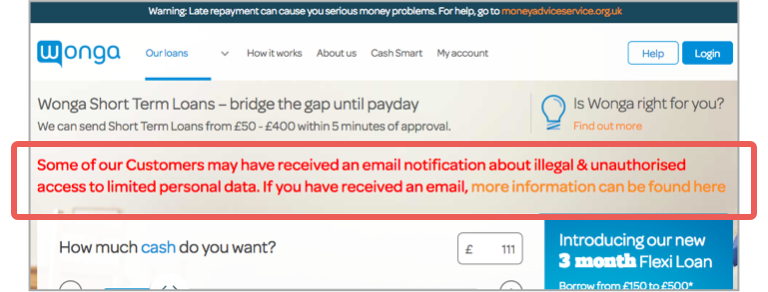
If you’ve ever used Wonga, we recommend reading the FAQ even if you didn’t receive an email from the company, just so you’re aware of what is known so far.
If you were one of the unlucky customers whose data was stolen, the silver lining is that the crooks only seem to have got at a subset of all the data Wonga knows about you:
- Name.
- Email address.
- Residential address.
- Phone number.
- Bank account number and sort code.
- Last four digits of card number.
As galling as it is to have this data disclosed by someone else, none of the items above are quite enough on their own for a crook to defraud you directly.
For example, in the UK, your address is effectively a matter of public record thanks to the electoral register, and many companies and sole traders openly publish their bank account numbers on every invoice to make it easy to get paid.
But stolen databases like this one are nevertheless valuable to cybercrooks, because having all those data points conveniently collected together is gold dust for scammers and social engineers.
It makes it easier for someone with the gift of the gab to convince your bank, your employer or your friends that they know you really well, or that they are acting on your behalf, or even that they are you.
It also gives those self-same scammers a way to persuade you to divulge more about yourself, for example by contacting you and pretending to be someone investigating the breach.
LEARN MORE ABOUT SCAMMERS: The scam that knows your name and home address ►
Worse still, if you chose your password unwisely, for example by basing it on information associated with the account so that the password was easier to remember, it’s now easier for cybercrooks to guess.
(Wonga seems pretty certain that no password-specific data was stolen outright, whether encrypted or not.)
What to do?
- If you have an easy-to-guess password on your Wonga account, go and change it, because it’s now even weaker than before.
While you’re about it, change your other online passwords too, after watching our video on How to Pick a Proper Password.
(No video? Watch on YouTube. No audio? Click on the [CC] icon for subtitles.)
- Keep an eye on your Wonga account and any transactions in and out of any bank accounts that you shared with Wonga.
In Wonga’s words, “We will be alerting financial institutions about this issue and any individuals impacted as soon as possible, but we recommend that you also contact your bank and ask them to look out for any suspicious activity.”
- If someone contacts you by phone or email to discuss the Wonga breach, don’t act on any information they give you.
Hang up the phone, as you would with a technical support scammer (or delete the email, as you would with unsolicited attachments) and contact Wonga directly using contact details you figured out for yourself.
In Wonga’s words, “Beware of scammers or unusual online activity. Be cautious of anyone who calls you and asks you to disclose any personal information regardless of where they say they are from. If this happens, we recommend that you hang up.”
As we like to say here on Naked Security, if in doubt, don’t give it out.
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/_eg6j5a3zbc/