Cryptocurrency as the lure, an ISO as the attachment – why not open it?
You can’t move these days without bumping into words such as cryptocurrency, Bitcoin, coinminer and blockchain.
With Bitcoin’s value up more than 1000% in the past year, and with companies multiplying their share price simply by adding “Blockchain” to their names, you can see why these words are everywhere.
As you’ll have seen in many Naked Security articles, cryptocurrency is popular with cybercrooks, too.
Usually, cryptocurrency is the end, rather than the means of the crime, for example when crooks infect your computer with coinmining software to hijack your CPU to earn them money, or scramble your data with ransomware and demand that you pay them in cryptocoins to get it back.
But here’s something a bit different that ‘we’ve seen recently: cryptocurrency as the means to a malware infection, not the end of that infection.
These phishing campaigns are also slightly unusual in that they include attachments that are ISO files.
You probably associate ISO files with ripped music CDs or movie DVDs, and with bootable Linux (or Windows) distros – ISOs are just byte-for-byte copies of the raw content of an optical disk.
You usually use them as CD backups, or as a source to burn new CDs.
However, many Windows users have utilities that can open ISO files as though they really were CDs; in fact, Windows 10 will open up ISOs simply by double clicking on them, which allocates them a regular drive letter in the system.
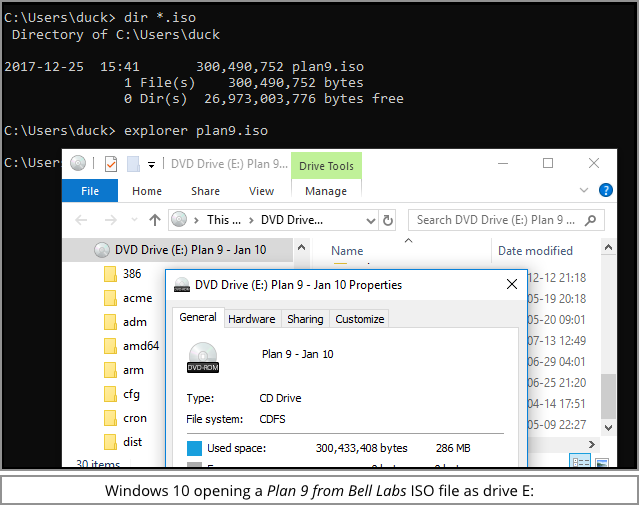
We’re assuming that the crooks have chosen this mix because cryptocurrencies are a red-hot lure, while ISO attachments, though unfamiliar, are nevertheless an undramatic and largely unsuspicious type.
Sure, ISOs are unusual, and they’ve been associated with Linux malware attacks before, but for Windows users, they simply don’t have the malware-related associations of attachments such as EXEs or ZIPs.
Yet they’re as straightforward as ZIPs to open and use.
Here are two examples of the ISO-laden, cryptocoin-themed phishes we’re talking about:
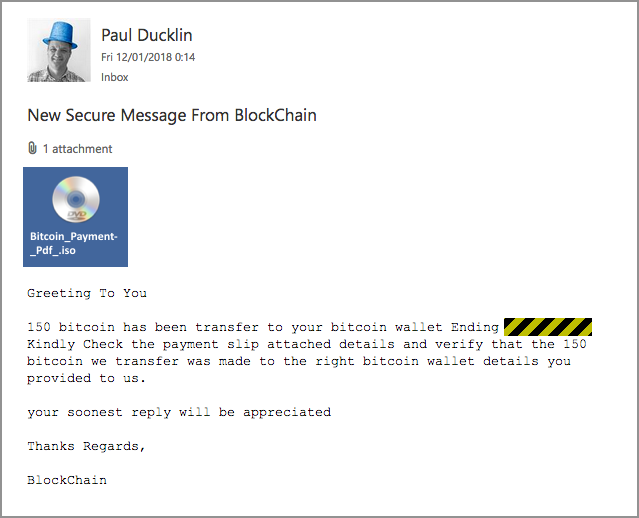
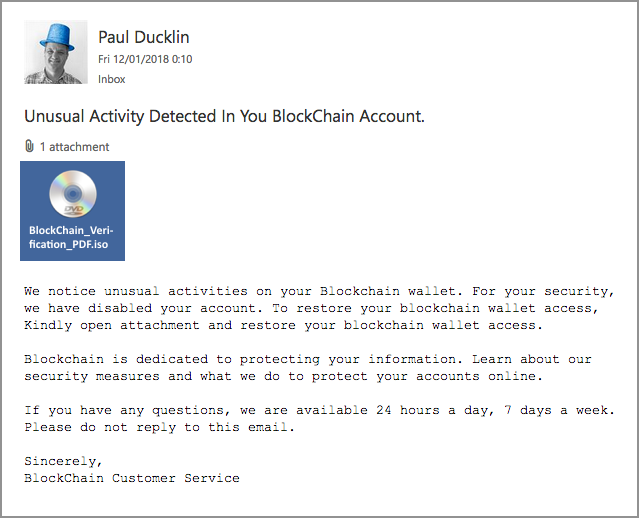
If you open the ISOs, they contain malicious EXE files (programs) with names of the form xxxxx.PDF.exe; by default, Windows doesn’t display the extension at the end of a filenames, so these show up as though they were documents with the much more innocent name xxxxx.PDF.
The most common malware we’ve seen in ISO files of this sort is known as Fareit, a threat family notorious for snopping around on your computer trying to steal login credentials.
What to do?
Even if you are dead keen on cryptocurrency, even if you watch the Bitcoin price like a hawk, and even if you actually have an account with the company Blockchain.com…
…you ought to spot these phishes if you keep alert, and don’t let yourself feel rushed.
- Legitimate emails don’t invite you to check your account via an attached file, or even a weblink. They expect you to find your own way to the site, precisely to avoid getting suckered into opening a bogus attachment or visiting an imposter site.
- ISOs aren’t typically used in email exchanges. If you’re not sure what it is, or why someone would choose to send it to you other than to make things look different, don’t trust it. If you’re a sysadmin, consider blocking ISOs at your email gateway unless your organisation has a genuine reason to swap them via email. (We can’t think of any reason, let alone a good one.)
- File extensions aren’t there to be hidden. Don’t stick with the Windows default – go to
File Explorer→Viewand turn onFile name extensionsso you can easily spot trickery such as double-extensions like PDF.exe or TXT.docx. If you’re a sysadmin, consider turning this on for all your users via group policy. - Spelling and grammar mistakes are a useful warning. These days, not all phishes are badly-written, and some legitimate corporate emails are at the borderline of illiteracy, so you can’t rely on grammar alone to spot a phish. Nevertheless, many phishes still smell fishy, so don’t ignore your nose.
If in doubt, leave it out!
Follow @NakedSecurity
Follow @duckblog
Picture of CD in featured image by Ubern00b – Own work, CC BY-SA 3.0.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/MwpBhoJXvCE/