Sears Holdings, Delta and others leak credit cards in “multibreach”
Another day, another data breach.
More precisely: another day, another multibreach, caused by a common point of failure.
That’s a bit like what happened recently when hundreds of government websites ended up cryptojacked because a shared service provider – in that case, a web-based text-to-speech system – got hacked, and “passed on” the hack to all its customers.
This time, at least Sears Holdings, owners of brands such as Sears and Kmart, and Delta Airlines were affected by a breach at a chatbot company that both companies use.
The company that spilled the data is the curiously-named [24]7.ai, a company whose website leads with the question, “Ready to Join the Chatbot Revolution?” and follows up with a free white paper entitled, “Why Delighting Customers is a Waste of Time and Money.”
Unfortunately for both Sears Holdings and Delta, at the same time that [24]7.ai was saving them money by not delighting customers, the company was also costing them reputation points (and perhaps getting them into regulatory trouble) by leaking personal customer information.
According to Sears Holdings:
[24]7.ai, a company that provides online support services to Sears and Kmart, notified us, as well as a number of other companies, that they experienced a security incident last fall. We believe this incident involved unauthorized access to less than 100,000 of our customers’ credit card information. As soon as [24]7.ai informed us in mid-March 2018, we immediately notified the credit card companies to prevent potential fraud, and launched a thorough investigation with federal law enforcement authorities, our banking partners, and IT security firms.
According to Delta:
Last week, on March 28, Delta was notified by [24]7.ai, a company that provides online chat services for Delta and many other companies, that [24]7.ai had been involved in a cyber incident. It is our understanding that the incident occurred at [24]7.ai from Sept. 26 to Oct. 12, 2017, and that during this time certain customer payment information for [24]7.ai clients, including Delta, may have been accessed – but no other customer personal information, such as passport, government ID, security or SkyMiles information was impacted.
We have to imagine that the customers of [24]7.ai are surprised – if not incensed – that the company took so long to pass on news of the breach, given that the ultimate accountability for safeguarding the information lies with those customers, not with [24]7.ai itself.
Of course, we also have to assume that [24]7.ai may not even have realised they’d been hacked until well after the event.
It’s surprisingly common for credit card breaches to be picked up by the card issuers themselves, after the data has been sold on the underground and actively abused, because of what are called CPPs, or common points of purchase, amongst defrauded card holders.
(With apologies to Oscar Wilde, to lose one credit card number may be regarded as a misfortune; to lose two looks like carelessness; to lose hundreds of thousands is a large-scale compromise.)
The reaction
Well done to Sears Holdings and Delta for providing prompt public commentary on their websites, and for setting up dedicated web pages where customers can track the breach investigation as it goes on.
Even better is that both companies avoided “doing an Equifax” – after its 2017 megabreach, Equifax infamously set up a brand new domain name as a landing page for updated information.
Being brand new, this one-off domain, equifaxsecurity2017 DOT com, had no reputation with any search engines, looked like a scam itself, and as good as begged typosquatters to register similar names to trap unwary visitors.
Equifax went on to compound that blunder when its PR company tweeted out an incorrect version of the new “security incident domain”, making a bad thing even worse.
The PR company wrote securityequifax2017instead of equifaxsecurity2017 – fortunately a security researcher registered the misnamed domain before the crooks could do so.
This is a blunder that simply wouldn’t have happened if Equifax had stuck to a URL that was part of its regular website.
Sears Holdings has gone for searsholdings.com/update and Delta has chosen delta.com/response, thus taking advantage of their already-known domain names and the HTTPS certificates associated with those domains.
Just two notes, though, as we write this [2018-04-05T15:00Z]:
- Sears Holdings officially linked to the
http://version of its page. Because the page is also available by usinghttps://, why mention the unencrypted HTTP version at all?
Hey, @Sears @SearsHoldings – well done making your breach response URL part of your existing domain (not like Equif… twitter.com/i/web/status/9…
—
Paul Ducklin (@duckblog) April 05, 2018
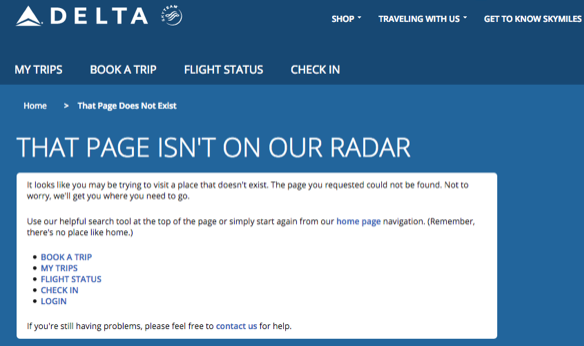
- Delta’s page didn’t exist yet and gave an error. The error page confusingly said, “THAT PAGE ISN’T ON OUR RADAR”. Why not create the page with a “coming soon” message instead, rather than reporting an error and inadvertently encouraging customers to go looking elsewhere?
What to do?
We don’t yet know what really happened, except that an online support company ended up creating a whole host of unwanted support issues for its customers.
In the meantime: watch those credit card statements; consider requesting a new card if you think you might be affected; and remember…
…you can outsource your work, but not your accountability.
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/tRC9oKWnpog/