Russian malware harvesting Telegram Desktop creds, chats
Already under attack by Russia’s telecommunications regulator, a new source of woe has emerged for crypto-chat app Telegram: malware.
In news that won’t surprise anybody at all, researchers from Cisco Talos say the malware attacking Telegram’s desktop app was written by a Russian speaker.
Vitor Ventura and Azim Khodjibaev explained what they saw in two April attacks involved collecting “cache and key files from end-to-end encrypted instant messaging service Telegram.”
The reason the malware attacked only the desktop version is because it “does not support Secret Chats and has weak default settings” – that’s a feature only of the desktop version, and Telegram warns users and explains why security is absent in that environment.
The attack works “by restoring cache and map files into an existing Telegram desktop installation, if the session was open,” giving the attacker the chance to access the victim’s session, contacts, and previous chats.
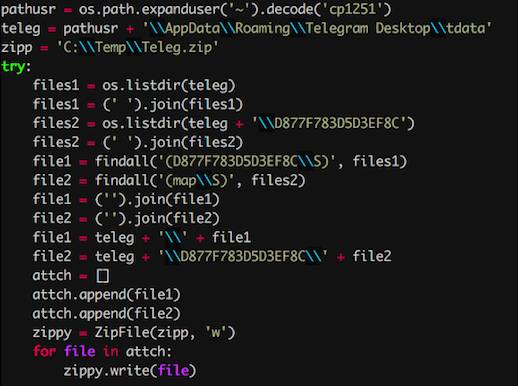
The malware readies data for exfiltration. Image: Cisco Talos
The Talos duo’s assessment that the malware’s author is a Russian speaker comes from a YouTube tutorial linked in the Talos post.
They located various handles and repositories associated with the attacker, named variously “Racoon Hacker … Eyenot (Енот / Enot) and Racoon Pogoromist (sic)”.
While Python is Enot’s first language as a programmer, Talos said it’s seen the malware in downloaders written in Go, AutoIT, Python, and a .NET prototype.
The malware scans hard drives on Windows targets for Chrome credentials, session cookies, and text files, which get zipped and uploaded to pcloud.com. ®
Sponsored:
Minds Mastering Machines – Call for papers now open
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2018/05/17/talos_telegram_desktop_attack/