Facebook apps expose millions of users’ Facebook data
It’s happened again!
Unsecured personal data found lying around in the cloud!
Unfortunately for Facebook, which has been caught up in numerous “concerned about cybersecurity” stories lately, this isn’t just any old data…
…it’s data that was acquired via Facebook by third-party apps.
It’s a little bit like what happened with Cambridge Analytica – the infamous Facebook app provider that offered so-called psychometric tests to seduce you into giving away a lot of detail about what made you tick, and then turned round and used that data in ways you almost certainly didn’t expect.
Ironically, even though these latest two data spillages, announced yesterday by leak-seeking cybersecurity company Upguard, aren’t quite as scary as the Cambridge Analytica story, they are in some ways even worse.
These breaches happened through plain old carelessness – databases hosted in the cloud and apparently almost casually left open to the world.
That’s like running your own servers in your own server room, but leaving the server room door unlocked with a big sign on it saying, “Free admission. Please don’t be naughty.”
In fact, it’s like copying critical data from your own servers onto a whole boxful of unencrypted USB drives and walking round a Dark Web convention handing them out to all and sundry.
What leaked?
According to Upguard, the latest leaky buckets it found belong to:
- Cultura Colectiva, a Latin American social networking collective that spilled a giant database of more than 500 million entries, probably covering millions of users (the site itself claims 45 million subscribers). The data apparently included Facebook IDs, likes, friends and more.
- At the Pool, a Facebook app that seems to have died out back in 2014, leaving its collected data orphaned and exposed. This data apparently included names, email addresses, Facebook IDs and passwords (not Facebook passwords, but stored in plaintext).
In other words, even though this isn’t “a Facebook breach”, because no one broke into Facebook itself, it is “a breach of Facebook data”, made possible by the enormous reach and influence that the Facebook platform enjoys.
Where to go?
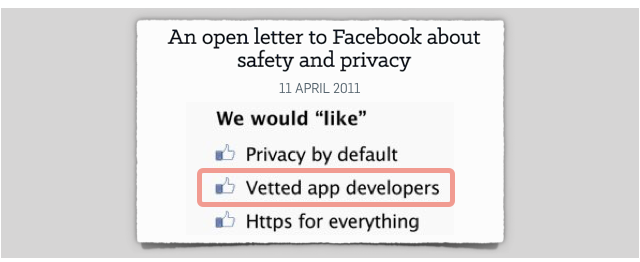
It’s almost exactly eight years since we wrote an open letter to Facebook, saying:
We would “like”: Privacy by default, Vetted app developers, Https for everything.
To our very pleasant surprise, Facebook was one of the first big cloud operators to bite the HTTPS bullet, encrypting and authenticating its traffic everywhere, all the time.
At the time, many other companies were complaining that it would be too hard, too expensive, too slow and mostly pointless to encrypt everything, but Facebook proved them all wrong.
But not much has happened in respect of our second “like”, namely greater control over app developers.
The reason for keeping tighter reign on app developers is that they have a privileged position in a rich and sprawling kingdom.
Facebook apps essentially knit themselves into the Facebook ecosystem for free, almost instantly enjoying the imprimatur and reach of the world’s biggest social networking company.
And with freedom comes responsibility – whether that’s the duty not to do sleazy things with data shared in good faith, or simply the duty not to leave collected data lying around insecurely.
Let’s hope that Zuck’s recent company-wide bulletin about getting more serious about privacy brings results – we’re hoping to see fewer apps of higher quality from more reliable developers.
Facebook pulled off a security revolution when it reinvented its transaction security by rapidly adopting HTTPS everywhere-and-all-at-once…
…so let’s hope it can transform itself again, and get rogue apps under control, too.
What to do?
- Review your Facebook apps and their permissions right now. Go to
https://www.facebook.com/settings, chooseApps and Websitesfrom the left-side menu, and use the list of apps and websites, if any, to view and update the info they can request or to remove the apps and websites you no longer want. - Review your privacy settings more generally while you’re about it. Use the
Privacymenu item on the Settings screen to access thePrivacy Settings and Toolspage. - Turn on 2FA if you haven’t already. Because you can. Use the
Security and Loginpage to set yourself up. You can hand over your mobile phone number for SMS login codes, use an authenticator app, or set up a login token like a Yubikey if you have one.
While we’re handing out advice, here are some general thoughts for the many app prdoucers and consumers out there:
- If you’re an app developer, whether of Facebook apps, Google Play apps or software for any other platform, stop seeing security as a cost to be driven down. Make it a value that you can use to establish your trustworthiness.
- If you’re an app user, learn to be selective. Choose apps from companies that have earned your trust rather than simply claiming it. Avoid apps just because they’re fun or cool. Less is more.
- If you’re an app enabler like Facebook, regardless of the scale of your operation, remember our plea from April 2011, “We would like: vetted app developers”. Rapid signup procedures for developers may be egalitarian and convenient, but they seem so often to end in tears.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Ef3wbf61duI/