Secret-sharing app Whisper shared secrets like last known location and actual password tokens in exposed database
Whisper, a mobile app for sharing those thoughts you’d rather not make public, turns out to be better at sharing secrets than keeping them, spilling a whopping 90 metadata fields associated with users in an exposed database.
The app, launched in 2012, is intended as a way for people to “share real thoughts and feelings, forge relationships and engage in conversations on an endless variety of topics – without identities or profiles.”
But as reported by The Washington Post, security researchers found 900 million user records publicly accessible online, exposing both deliberately public and private metadata that could serve to identify supposedly anonymous users of the app.
That 5TB, 75-node database, which has been locked away since Monday, when the company and law enforcement were notified, presents a risk that some app users could be identified and linked to supposedly anonymous posts and potentially sensitive associations, such as membership in fetish groups, hate groups and suicide support groups, for example.
It’s not clear how long the data has been exposed or whether anyone copied the exposed info before it was secured. The data did not include usernames, but did include fields like age, gender, nickname, country, interested_in, IP address and timezone. User-submitted images and videos were available as well, but hosted elsewhere in cloud storage buckets.
In a phone interview with The Register, Dan Ehrlich, security consultant with Twelve Security, said colleague Matt Porter had spotted the unprotected Whisper ElasticSearch database.
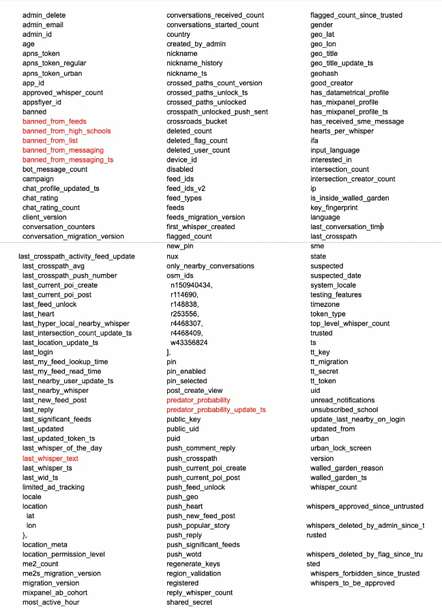
List of Whisper metadata fields in exposed database
Ehrlich observed that while Whisper makes maybe five fields of metadata public in posts, the posts available in the ElasticSearch database have about 90 metadata fields (see above) associated with them, including last known geolocation and the actual password token – usable for logging in as that user.
Using the command line tool cURL, the researchers were able to do just that by sending a Base64-encoded key and token to the message API endpoint. “It is possible to log in as any user anywhere,” according to Ehrlich.
Among the records was a list of international military bases intended, as the Post tells it, for a never-realized suicide study. Those records, in conjunction with geolocation data, might provide a way to infer membership in the military. Given Whisper’s financial ties to Tencent, which invested in the company in 2014, and reports that Chinese companies like Tencent work with Chinese government entities, Ehrlich said there was reason to be concerned.
According to Ehrlich, the database contains a significant amount of information associated with millions of minors who use the app, despite the fact that the app is only supposed to be available to those 17 or older.
Collecting and keeping
He also points out that Whisper appears to have kept data since 2012 without deleting it. “It is not clear if all records have been kept, but a very overwhelming majority of them certainly have,” he explained, pointing to an associated Amazon S3 bucket called “whisper-deleted.s3.amazonaws.com” and the presence of record types that store groups from which users have unsubscribed and previous usernames.
The Whisper app also scores users on their likelihood to be a sexual predator, in the predator_probability data field. Some 9,000 users had a probability assessment of 100 per cent and another 10,000 were rated at 50 per cent, according to data provided by Ehrlich.
The Register asked Whisper’s parent company, Media Lab, to explain how it makes that calculation. We also sought comment from Whisper. We’ve not heard back.
In a statement provided to the Post, a company spokesperson insisted it doesn’t track users and that its internal database (a different one, presumably) is not publicly accessible.
In 2014, The Guardian reported that Whisper was tracking the location of its users, even those who declined to be tracked. Whisper’s editor-in-chief at the time claimed The Guardian was lying, prompting the paper to defend the accuracy of its reporting. Whisper received a letter inquiring about the report from then US Senator Jay Rockefeller (D-W.Va.), leading to a response (PDF) from CEO Michael Heyward and the firing of Whisper’s editorial team.
Ehrlich believes Whisper’s representations at the time did not accurately portray its data collection practices. ®
Sponsored:
Quit your addiction to storage
Article source: https://go.theregister.co.uk/feed/www.theregister.co.uk/2020/03/11/secret_sharing_app_whisper_shared_secrets_in_exposed_database/