Syrian Electronic Army brings down Twitter and The New York Times through domain name provider hack
 Slightly more than a week after the Syrian Electronic Army (SEA) redirected readers of Time, CNN and The Washington Post through its hack of Outbrain, the group continued its online assault of Western media companies by taking down social media giant Twitter and “newspaper of record” The New York Times.
Slightly more than a week after the Syrian Electronic Army (SEA) redirected readers of Time, CNN and The Washington Post through its hack of Outbrain, the group continued its online assault of Western media companies by taking down social media giant Twitter and “newspaper of record” The New York Times.
The methods are unknown, but some basic detective work suggests they are continuing their previous work of using phishing to compromise trusted third parties of major brands, rather than attacking the targets directly.
Both The New York Times and Twitter purchase their internet domain names from a company called Melbourne IT Ltd, which does business as Internet Names Worldwide.
This appears to be the source of the trouble.
Starting at about 2013-08-27T12:00-4 (noon on the US East Coast), the first signs of trouble for The New York Times began.
The name server records for Internet Names Worldwide were redirected to M.SEA.SY, MOD.SEA.SY and SEA.SY, servers under the control of the Syrian Electronic Army.
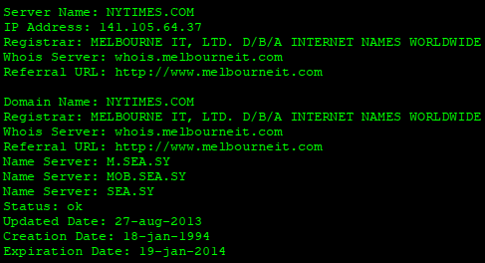
This did not impact most internet users immediately, however, as DNS records for high traffic sites are commonly cached for extended periods of time – in the case of the Times, just short of 23 hours.
If we dig a little deeper, we see the IP address of the new name server, 141.105.64.37, which is owned by an ISP in Moscow, Russia.
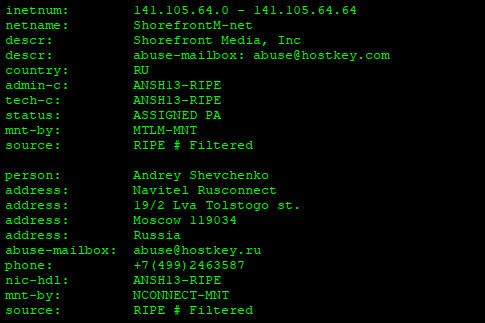
This ISP hosts both the SEA’s website as well as other controversial sites like Qatar Leaks.
Just a short while later Twitter started experiencing the same issues. Twitter’s records at Internet Names Worldwide were altered in a similar way to those at The Times.
It looks as though the hack was meant merely to divert visitors to the SEA’s own site, but (in a fit of almost-amusing irony) produced enough redirected traffic that the SEA effectively DoSed itself, and the site went down.
These incidents demonstrate a sad truth: Security is hard.
Media organizations are well aware of the previous antics of the Syrian Electronic Army and have worked hard to raise their game.
Employees at these companies have been trained to watch out for phishing attacks and be more suspicious of requests for information.
While these reactions are appropriate, they are not enough. You are only as strong as your weakest link, which in this case appears to be an external internet service provider.
Understanding all of the bits and pieces your organization relies on to do its work is only the first step in assessing your “hackability”.
 I hear from many IT professionals at conferences, seminars and customer engagements that their management wants to know that they are “secure”. The answer they want is an answer you really shouldn’t give.
I hear from many IT professionals at conferences, seminars and customer engagements that their management wants to know that they are “secure”. The answer they want is an answer you really shouldn’t give.
You can reduce your risk, though.
By raising awareness among your employees about phishing attacks, these incidents can help demonstrate the real risks of being tricked.
Use it as a reminder to everyone about proper authentication practices at your organization.
You should also work with your service providers to find out what they are doing to protect your organization against attacks on their infrastructure.
Note: As of 2013-08-27T23:25Z, Twitter’s Indian domain name (twitter.co.in) is still under the control of the Syrian Electronic Army. It is advisable to use twitter.com until Twitter regains control.
Image of a house-lock courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/GeyGcZqSiqc/