Adobe has Patch Tuesdays, too – a reader reminds us!
Naked Security reader Haemish Edgerton just gave us a very polite but effective scolding (Linus Torvalds, take note!) for neglecting to mention the Adobe fixes that came out on Tuesday.
As Haemish pointed out:
I realize that the Apple iPhone 5S fingerprint sensor was automatically going to get a lot of attention in the context of security, but Adobe updates are important too :)
Sorry, Haemish.
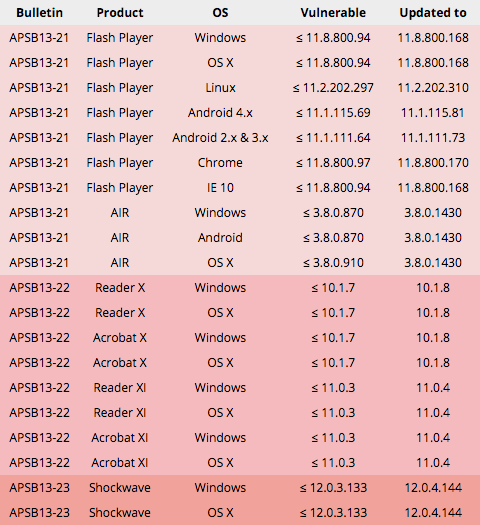
For the record: there were three bulletins, four platforms affected (Windows, Linux, OS X and Android), five products updated, and fourteen vulnerabilities (CVEs) covered.
The bulletins are: APSB13-21, APSB13-22 and APSB13-23
All three bulletins list the vulnerabilities as potentially exploitable for Remote Code Execution (RCE), or, in Adobe’s own words, as bugs that could “allow an attacker to take control of the affected system.”
As is often the case with Adobe’s updates, there are lots of version numbers to take into account.
That’s especially true of Flash Player, where it seems that the product’s source code for the various platforms supported is currently at a wide range of different stations in Adobe’s railway network. (Platforms. Stations. Geddit?)
Here is what to look for if you want to see if you are vulnerable:
Confused?
Spare a thought for the guys in Adobe Quality Assurance!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/V7SuBOWfWh8/