Adobe publishes out-of-band Flash update
 This week, Adobe joined Microsoft in issuing an official November 2014 patch that didn’t come out on Patch Tuesday.
This week, Adobe joined Microsoft in issuing an official November 2014 patch that didn’t come out on Patch Tuesday.
Microsoft backfilled a patch that had originally been promised for Patch Tuesday but didn’t quite make the cut.
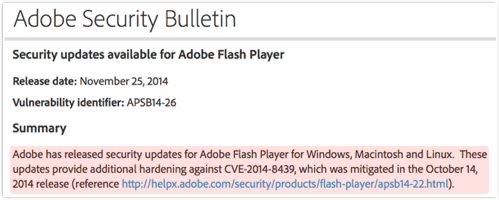
Adobe’s latest Flash update, dubbed APSB14-26, was more by way of a booster dose.
The latest patch adds additional protection against a vulnerability that was originally addressed in October 2014:
Adobe has released security updates for Adobe Flash Player for Windows, Macintosh and Linux. These updates provide additional hardening against CVE-2014-8439, which was mitigated in the October 14, 2014 release.
According to independent malware researcher Kafeine, who publishes on the website malware.dontneedcoffee.com, it looks as though the crooks worked backwards from Adobe’s October 2014 patch to get ideas for new ways to attack Flash.
Even if you ship patches in compiled binary form, and go out of your way to rebuild the changed components so that the decompiled code can’t easily be lined up with the previous versions, determined reverse engineers can almost always learn something about what you just fixed.
That, in turn, may give them hints about where to sniff around for related but as-yet-undiscovered holes.
That seems to be the case here: SophosLabs reports that it has seen a modest number of attacks that seem to be using the CVE-2014-8439 vulnerability, which Sophos products detect and block with the name Troj/SWFExp-CD.
The potential reversibility of patches is not an argument against patching, by the way: after all, holes that are fixed by today’s patches already exist, and thus need fixing anyway.
The bottom line
- If you are a Flash user, make sure you have this patch, whether you are on Windows, OS X or Linux. The trick to exploit it seems already to be in use by cybercriminals.
- Try uninstalling Flash to see if you can live without it. As this incident reveals, Flash is popular with crooks, who put plenty of effort into working out how to exploit it.
- Use your browser’s click-to-play option, also known as Ask to Activate, especially if you only need Flash occasionally. Flash won’t run until you say so, which reduces your exposure to unexpected and unwanted Flash content.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/j1q8x4JabR0/