Anatomy of an iTunes phish – tips to avoid getting caught out
 Do you know how to ride a bicycle?
Do you know how to ride a bicycle?
It’s easy, isn’t it?
But do you remember how hard it turned out to be when you first tried?
Who would have thought?
We often forget that many things are “obvious” only with experience, meaning, in fact, that they’re not really obvious at all.
That’s why we do phishing walkthroughs fairly regularly on Naked Security.
The idea is to step you through a typical email phish, pointing out the telltale warning signs in the original email and the web pages that follow, so you know what to look for in future.
So, even if you’d back yourself to spot a phish every time, here’s a step-by-step account that might help to save your friends and family in the future.
An iTunes phish
This phish arrived as a spam email claiming to be from Apple.
The App Store and iTunes boast tens of billions of music and app downloads between them, so the Apple brand is popular with scammers.
→ At the end of 2011, we investigated nearly 15,000 typosquats (deliberately misspelled domain names) for six brands. 86% of all possible one-character errors in typing apple.com had been registered, predominantly for disreputable purposes, the highest figure of the six.
Ripping off Apple’s brand as a call-to-action in spam is hardly surprising: there’s a good chance that any randomly chosen spam recipient will have dealt with Apple online before.
In this case, the scammers are trying to trick you into suspecting that someone else has been paying for downloads using your account.
They’re hoping you’ll click on the Transaction Details Here link as a first step to finding out what’s going on:
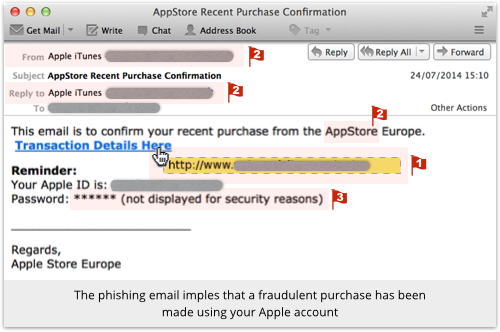
The red flags in this email are:
- Hovering over the link reveals a URL that is clearly unrelated to Apple. We have redacted it here, but it is a URL on a legitimate website that seems to have been hacked.
- The From and Reply to addresses are unrelated to Apple and unlikely for any official email. (But be careful: the text that is displayed as the sender’s address is part of the email itself, so a careful crook can make it look as legitimate as he wants.)
- It’s not the AppStore, it’s the App Store.
- Apple can verify your password, but not recover it. The company never stores your raw password, so it can’t send it to you, and would never imply that it could.
The fake Apple Store
If you do click to see the claimed transaction details, the link directs your browser to a boutique website that sells perfumes and fragrances.
It’s a legitimate business that was almost certainly running an insecure version of WordPress.
That allowed the crooks to implant their own content, and gave them a window of opportunity to use an otherwise-reputable domain name to serve their criminal purposes.
This hacked WordPress site then silently redirects your browser to the phishing site proper, bringing up a page with visual material ripped off from Apple, giving it a familiar and believable visual appearance:
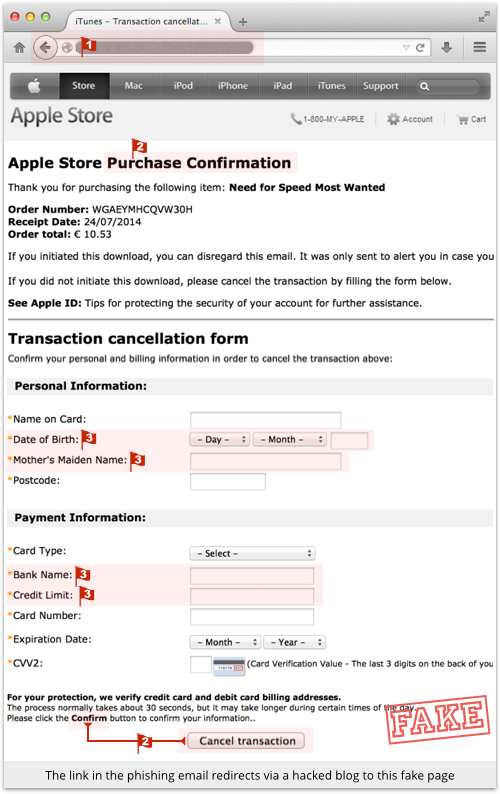
Nevertheless, as in the email, there are red flags in all three of our categories:
- A non-Apple URL that is requesting confidential information on an insecure (non-HTTPS) page.
- Inconsistencies in visual appearance, probably due to sloppy copy-and-pasting by the crooks. For example, the heading “Purchase Confirmation” doesn’t describe the rest of the page, and [Cancel transaction] is described as the “Confirm button.”
- Questions you would never usually be asked, even in a genuine payment transaction, such as credit limit, mother’s maiden name, and so forth.
By the way, be cautious of what you infer from mistakes in a web page.
Obviously, if there are mistakes, they are a negative indicator, and you should assume you are dealing with a phish.
On the other hand, the absence of mistakes is not a positive indicator: it might tell you nothing more than that you are dealing with careful crooks.
The fake “SecureCode” screen
If you get this far, the crooks have already stolen a lot of Personally Identifiable Information (PII) from you.
The next step tries to trick you into “verifying” your identity by giving away your VISA or MasterCard SecureCode.
SecureCode is a secondary authentication system used in many transactions that requires you to verify yourself to your payment card provider in a separate step from providing your card details to the retailer.
The idea is that you present a password directly to VISA or MasterCard, not to the merchant, for an extra layer of validation.
The bogus SecureCode page looks like this:
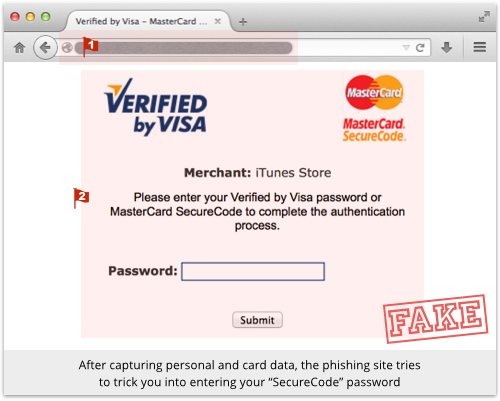
Everything is wrong here, because a SecureCode verification isn’t a secondary step requested by the merchant as a precursor to the transaction.
It’s a separate step initiated by the payment card company once the merchant has gone ahead with the payment processing:
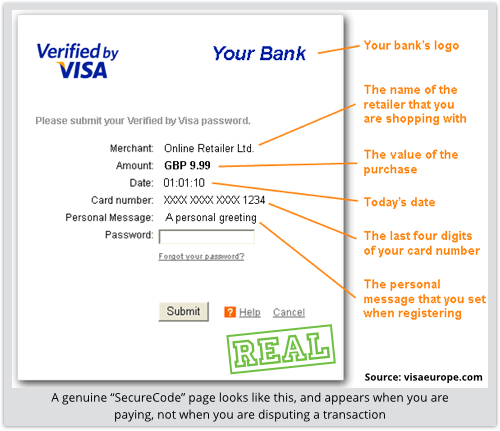
In this case, of course, you shouldn’t see a SecureCode validation page, because there is no payment involved.
Remember that you’re supposed to be challenging a transaction that has already been processed.
The reassurance page
You’re in trouble now, because the crooks have your card details, plus your SecureCode password, plus enough information (at least with the less cautious sort of financial institution) to give them a good shot at phoning up and convincing your bank that they are you.
If they can do that, they may be able to redirect your statements, change the phone number you use for notifications and two-factor authentication, and even lock you out of your own account.
Any of these things would make it slower for you to spot that there was a problem, make it harder to report and fix the problem when you realised, and give the crooks more time to plunder your account.
So they enter the last phase of the phish, meant to reassure you that things have gone your way, not theirs:
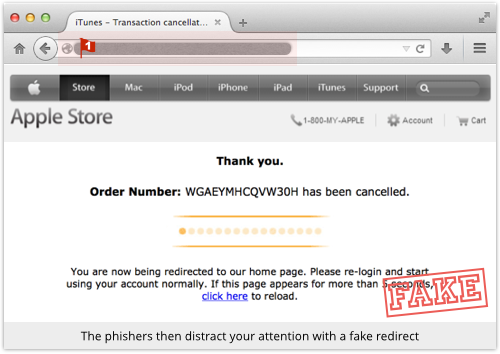
This page is really just a bit of visual theatrics, but nevertheless you would expect it to have an Apple-based URL and to use HTTPS.
The final reassurance is that you are redirected to the real Apple Store, by way of avoiding an abrupt ending to the “transaction”:
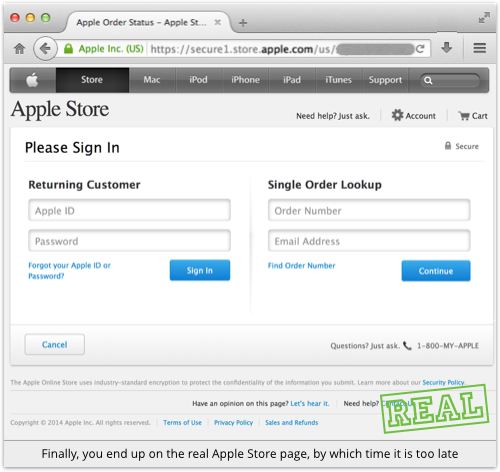
Ironically, even if you haven’t been suspicious so far, this last step ought to set off warning bells, simply for what it is, rather than what it isn’t.
Suddenly, and for the first time, you’re on a URL that looks as though it really belongs to Apple and uses HTTPS.
Also, the site has some small but obvious visual differences from what you’ve been seeing all along.
So the last page might very well be what you need to throw the bogosity of the previous pages into stark relief.
If that happens, act at once: you still have a chance to beat the crooks, especially if they were intending to sell your credentials on to someone else, rather than to start bleeding you themselves.
Call your card issuer, and use the number printed on the back of your card to make sure you don’t get tricked again!
Free Sophos UTM Home Edition
Want to block phishing emails and links for your friends and family on your home network?
If you have a spare PC or laptop handy, why not try the Sophos UTM Home Edition?
You get all the features of our commercial product, including not just web and email filtering, but also a network intrusion detection system; full-blown VPN support; regular and frequent updates; and licences to install and manage Sophos Anti-Virus for Windows on up to 12 PCs.
All for $0.
Image of goldfish and net courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/oV1Z5M9IjWw/