Android banking malware with a twist in the delivery
 In baseball (or so I am told), it’s a curveball or a knuckleball.
In baseball (or so I am told), it’s a curveball or a knuckleball.
In cricket, an altogether more slippery and treacherous game, it’s a googly or a doosra.
You’re expecting the ball to come at you in a predictable direction.
But a hidden twist in the action brings the onslaught from another angle altogether.
Here’s an intriguing tale of an Android malware curveball spotted recently in SophosLabs.
The crooks want to infect you with malware that knows how to intercept incoming SMSes and redirect their content elsewhere.
You can see where this is going: mobile malware that reads your SMSes before you do can steal important data such as the two-factor authentication (2FA) codes sent to your email provider or your bank, giving cybercriminals a way into your account despite the extra layer of protection in place.
But until the crooks can get their malicious Android package (APK file) into the Play Store, you’re not going to be able to install it unless you have changed the default security settings to allow apps from outside Google’s official marketplace:
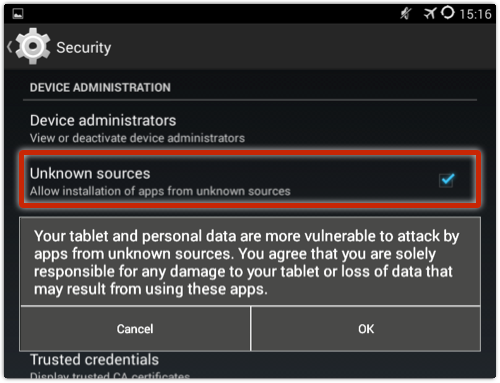
There may be another way in, however, even if you haven’t enabled so-called “off-market” apps.
Many, or at least some, of you may have enabled Developer Options on your device:
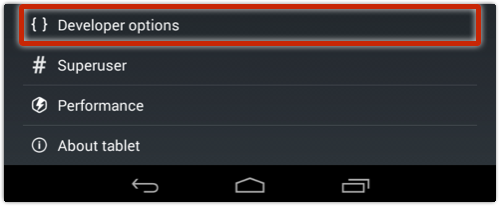
Once you have enabled Developer Options, you can turn on Android Debugging and get (very handy) low-level acccess to your device via USB, using what is known as ADB, or the Android Debug Bridge:
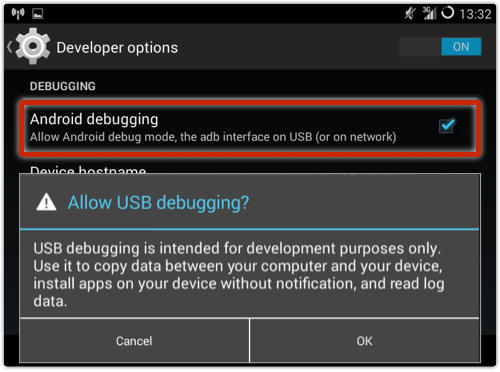
You’ll notice the warning about allowing you to “install apps on your device without notification,” and that’s the backdoor that the creators of the Troj/DwnlAPK-A malware are looking for.
Even if you have the front door locked to keep unapproved apps out, the USB debugging backdoor will allow any app in.
Here’s what Troj/DwnlAPK-A does if it manages to infect your computer.
• Installs a bogus “Service for adobe client product” under the name “Object Update Monitor”:
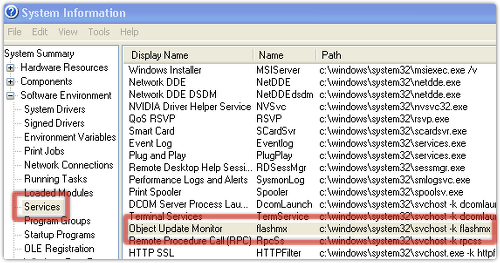
• Downloads a configuration file iconfig.txt listing the next files to fetch.
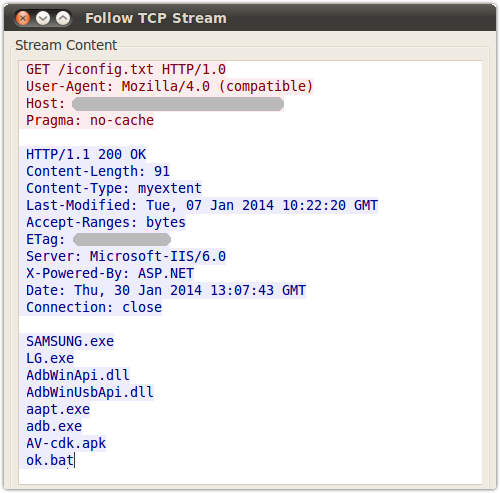
• Fetches the files from iconfig.txt.
• Runs ok.bat to install the downloaded Android malware.
The files SAMSUNG.EXE and LG.EXE appear to be regular, clean files that enable full USB-to-phone connectivity on Samsung and LG devices respectively.
→ We haven’t checked whether this means the malware will fail if you have a phone or tablet from another vendor. If so, that’s handy for you, but still amounts to security through obscurity – the crooks could just package different installers in their next version of the malware, or even in the next version of iconfig.txt. On a Mac, for what it’s worth, it’s all the other way around: regular USB connectivity for Android requires special Android File Transfer software (not needed on a Windows PC), while the Android Debug Bridge “just works” without additional drivers.
Similarly, the adb*.* files and aapt.exe come from the Android software development kit (SDK), so the malware depends only on your device having debugging turned on, not on the SDK being installed on your computer.
The file AV-cdk.apk, of course, is the Android malware package, detected by Sophos as Andr/FakeKRB-G.
The side-effect of ok.bat is the same as running the following command at a command prompt:
C:UsersYourname adb install AV-cdk.apk
The name AV-cdk may sound as though it’s pretending to be an anti-virus package, but once installed, the app hides in plain sight with a Google Play Store icon,
However, it gives itself the rather Appleish name of “Google App Store”:
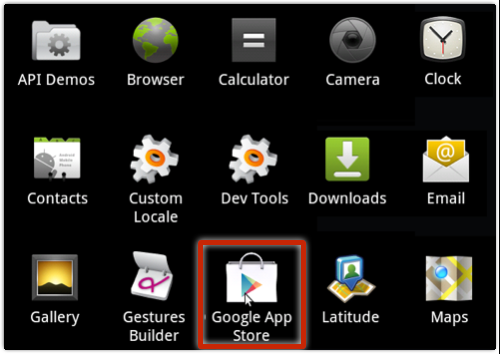
The real Play Store app simply calls itself “Play Store”:

With functionality to intercept your SMSes, amongst other malicious functionality, the Andr/FakeKRB-G malware is not something you want on your device.
What to do if you are an ADB user
As you can see, this malware depends on you having a weakly-protected Windows computer, and a developer-enabled Android device.
There’s not much excuse for the former, but there are many good reasons, even for non-developers, for using the Android Debug Bridge.
So, if you have enabled, or intend to enable, ADB-based debugging, here are some precautions to take:
• Turn off the Android debugging option when you don’t need it.
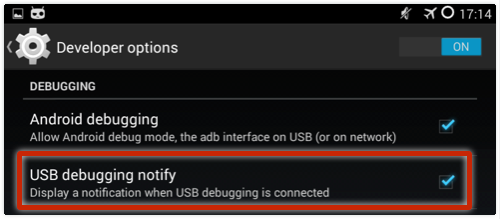
• Turn on the USB debugging notify option at all times:
• Avoid the Always allow from this computer option if you can, so you always get connection warnings:
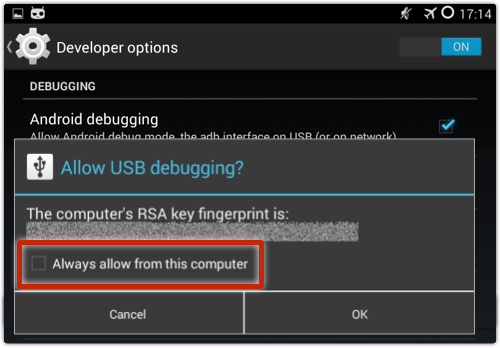
• If you do enable Always allow, use the Revoke authorizations option when you are done with ADB:
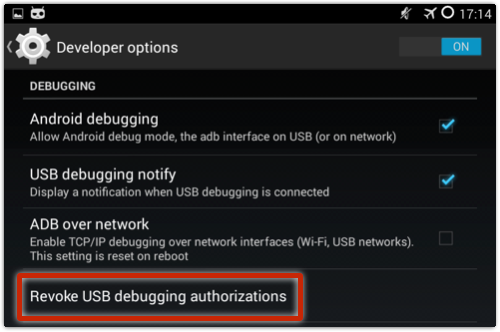
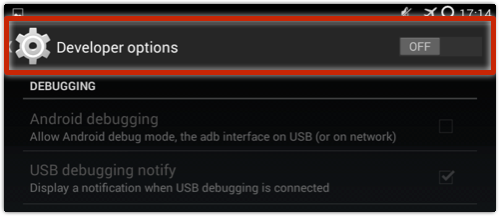
• If you do enable Developer Options, turn them off when you no longer need them:
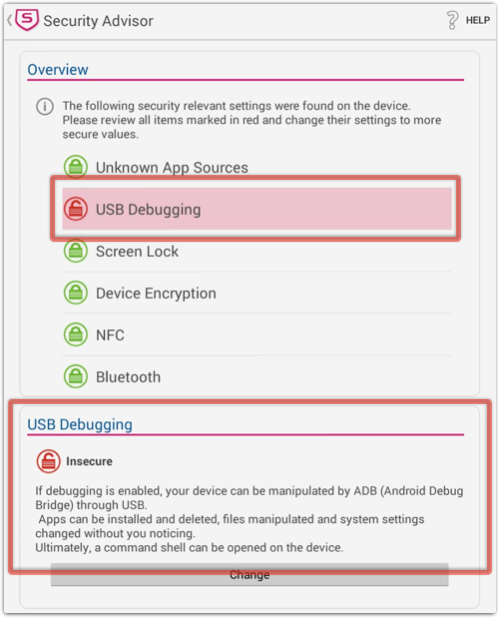
• Use the Security Advisor in Sophos Free Antivirus and Security for Android to watch out for risky system settings:
Where are those Developer Options, anyway?
We know what you’re dying to ask now, namely, “How do I activate these Developer Options in the first place?”
Here’s as much of a hint as we’ll give you.
Go to About Tablet | Build number and…knock several times to enter.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/sUSyL886UIQ/