Android "FBI Lock" malware
 SophosLabs just alerted us to yet another example of Android ransomware.
SophosLabs just alerted us to yet another example of Android ransomware.
Ransomware is the stuff that locks up your computer or phone with a pop-up that covers all your other apps, and sometimes even scrambles your data files.
What we’re talking about here is extortion or demanding money with menaces.
That’s because there’s a secret code that can unlock your phone, or decrypt your files, but only the crooks have it (or so they say).
If you want a copy of the recovery code, you have to pay.
The “fees” vary, from tens to hundreds, sometimes even thousands, of dollars.
Usually, payment is by some largely anonymous and irreversible mechanism, such as Bitcoin or a Moneypak voucher.
A persistent threat
Ransomware has been a persistent threat on desktop and laptop computers for several years.
The best-known example of lock-out malware is Reveton, which freezes out all other programs on Windows, including Task Manager, groundlessly accuses you of a crime (usually relating to piracy or pornography), and invites you to pay about $300 to make the “charges” go away.
And the best example of file-scrambling malware is CryptoLocker, which leaves your computer unlocked and running fine, but scrambles all your files with a strong cryptographic algorithm, before asking you for $300 for the decryption key.
→ The operational heart of the CryptoLocker malware, which relied on servers run by the crooks to produce and distribute a unique pair of encryption/decryption keys for each victim, was nobbled in a recent takedown operation driven by US law enforcement. Sadly, other malware has risen to take its place, because law enforcement can’t prevent people from getting infected by future variants, but the takedown was nevertheless an impressive and disruptive result.
With millions of ransom dollars, probably even hundreds of millions, already squeezed out of hapless victims around the world by desktop and laptop malware, it’s hardly surprising to see the crooks increasingly turning their malevolent attention to mobile devices.
This latest Android ransomware reported by SophosLabs follows a familiar theme, very much like the Koler malware we wrote about in May 2014.
But the new malware has a slight sting in the tail that Koler didn’t, making it trickier to remove.
So we thought we’d take you swiftly through the clean-up process.
FBILock-A
The malware, identified by Sophos as Andr/FBILock-A, masquerades as a Flash Player app:
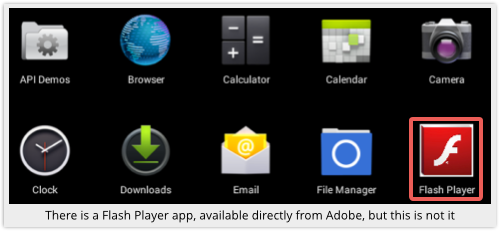
Android doesn’t have Flash support, and even Adobe’s own Flash Player is no longer available as an add-on in the Play Store.
So this is may well seem like an enticing extra, and one for which you would expect to have to enable “Allow apps from unknown sources.”
On opening the app, it pops up a request to become a Device Administrator:
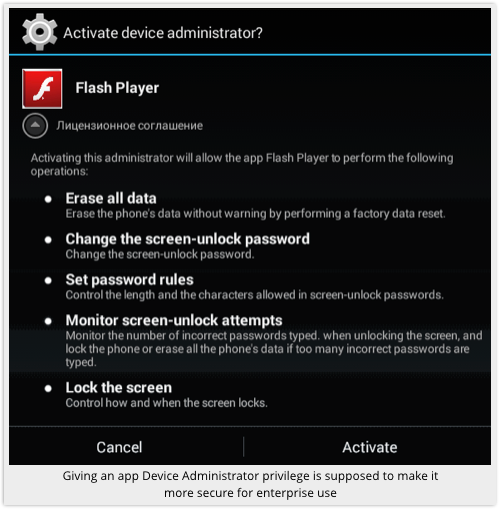
This is an official feature in Android intended to make the platform easier to control (and thus more likely to win acceptance) on a business network.
Ironically, a Device Administrator (DA) app is meant to be more secure than its vanilla counterparts, because a DA app can subscribe to centrally defined policies that enforce configuration settings such as minimum password length, data encryption and use of the camera.
Once launched, whether you allow the app to assume its requested DA powers or not, Andr/FBILock-A soon lives up to its name:
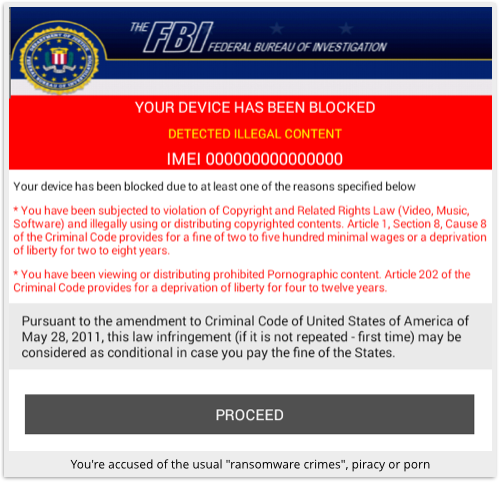
The extortion demand comes as soon as you tap PROCEED:
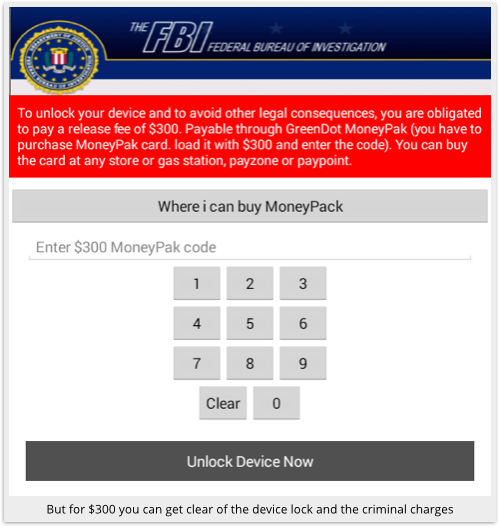
It is now very difficult to do anything with your phone, because the menaces screen keeps popping back up over whatever apps you try to run, including Settings, which you’d usually use to stop and get rid of misbehaving apps.
Using Safe mode
As we explained before, when showing you how to remove the Koler malware, you can get control back over your phone by using Safe Mode.
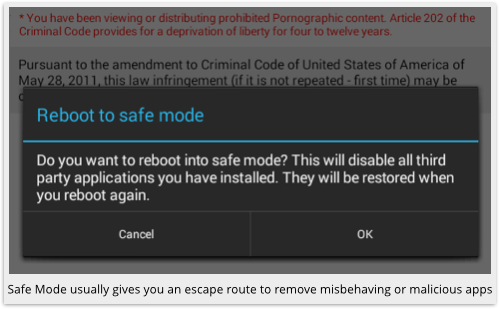
The mechanism for enabling it varies by device; one common way is to hold down the Power button; then tap and hold Power Off; then tap [OK] at the Reboot to safe mode dialog.
When Safe Mode is visible at the bottom left of your screen, apps that you’ve added to your phone shouldn’t be running, so FBILock can’t pop up to protect itself from removal.
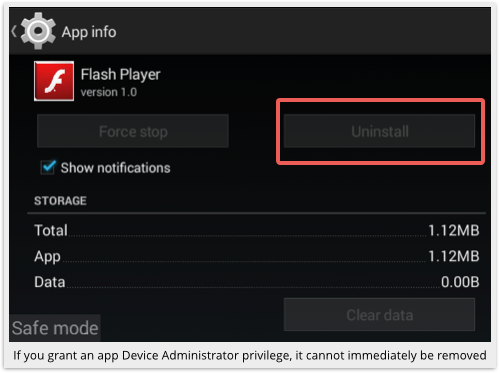
But when you head to Settings | Apps and tap on the fake Flash Player icon, you’ll see that the Uninstall option is greyed out:
You need to head to Settings | Security and go into the Device administrators screen:
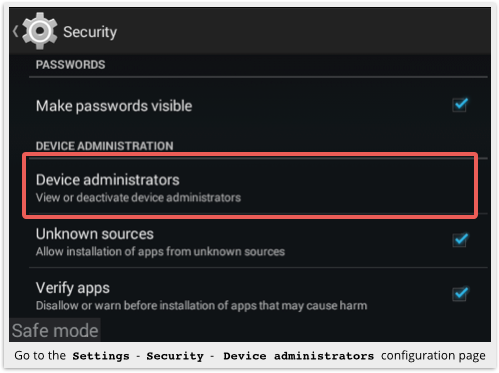
Tap on the FBILock app and you will be able to deactivate its administrative powers:
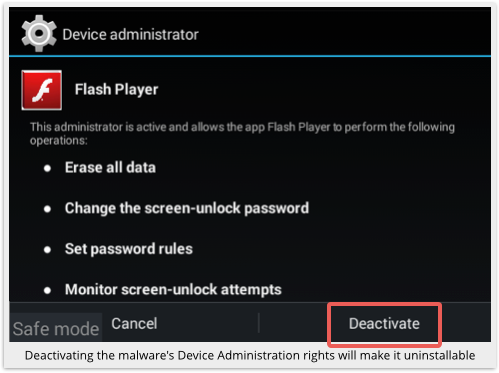
Now go back into the Settings | Apps page for the malware app, and the Uninstall button should be ready and waiting for you to use it:
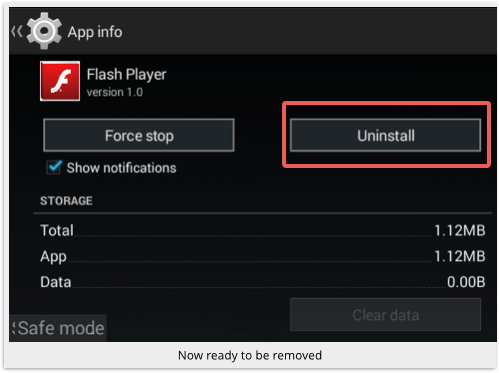
Uninstall the app, and you just saved yourself $300 and a trip to the convenience store to buy that Moneypak card.
Next steps
Why not do either or both of these:
- Head back to Settings | Security | Device Administrator and turn Unknown sources off.
- Head to Google Play and get your free copy of Sophos Anti-Virus and Security for Android.
Image of handcuff silhouette courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/N9wTRJ71rnw/