Apple lets rip with update spate: OS X, iOS, Safari, iTunes, QuickTime

Apple just opened the stopcocks and released a Hoover Dam’s worth of security-related updates.
Yes, there are numerous new features and products in there too, but it’s the security fixes that make a compelling reason to update.
As usual, Apple’s Security Updates landing page, HT201222 (often still linked to under its old 4-digit code of HT1222), has a summary of the non-Windows updates.
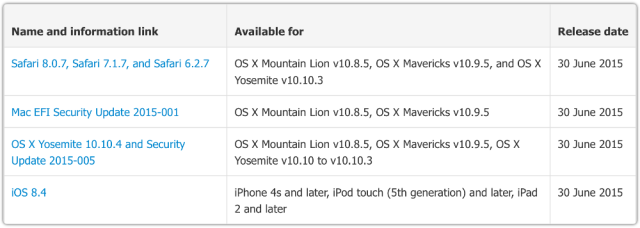
To summarise:
- Yosemite, the current release of OS X, goes to 10.10.4.
- The previous two OS Xs get a standalone security update, 2015-005.
- The previous two OS Xs get a standlone firmware update.
- iOS goes to 8.4.
- Safari goes to version x.x.7.
- iTunes goes to 12.2 for Mac and Windows users.
- QuickTime goes to 7.7.7 on Windows (Vista and 7 only).
What to do?
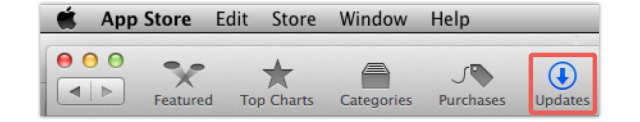
To see if your Mac is up-to-date go to Apple Menu | App Store | Updates.
Although Mac users will see an iTunes update in their mix, it looks as though the security-related fixes apply only to Windows.
That’s both good and bad news for Windows users.
Good because the fixes are out at last; bad because there are 39 CVE-numbered bugs on the list, including remote code execution holes, with 15 of them dating back to 2014.
QuickTime’s Windows-specific update seems a little more current, with 9 CVE-numbered bugs, all apparently fairly recently reported.
To update QuickTime on Windows, run the Apple Software Update program from the Start menu.
Why do it?
Rather than try to deal with OS X and iOS by “summarising in detail,” patch by patch, we’ll just say that there are lots of security holes fixed, including at least:
- Remote Code Execution (RCE). That’s where externally-supplied content, like a web page, could trick your Mac or iDevice into running malware without even an “Are you sure?” pop-up.
- Memory layout disclosure. That’s where an outsider can find out which programs are loaded where in memory, thus neutralising the protection of ASLR (address space layout randomisation) and giving crooks a clearer target to aim at when they attack.
- Elevation of Privilege (EoP). Here, a crook who has already broken in as a regular user can grant himself more power, often all the way up to root (Administrator). This makes a bad thing even worse.
- Security bypass. All the above bugs bypass security, of course. But there are many other forms of bypass, such as letting users get at or change files they shouldn’t even be able to see. Modest-sounding holes like this can often help crooks orchestrate a more serious attack.
- Browser data leakage. That’s where one web page is able to read private data, such as login tokens or authentication cookies, belonging to another page. By this means, an attacker could could hijack existing connections, for example to your webmail or social networking accounts.
In other words, there are plenty of holes that crooks and other attackers could exploit to get in and take over your device.
Understanding security vulnerabilities
Listen to our Sophos Techknow podcast
(Audio player above not working? Download, or listen on Soundcloud.)
When to do it?
It’s true that if you use OS X and iOS, you are much less likely to end up in the gunsights of a cybercrook than if you use, say, Windows or Android.
But that doesn’t mean you can skimp on security.
That would be like giving up on seatbelts and taking up speeding when you visit a country that has a better road safety record than your own.
One of the reasons for a better safety record is better safety practices!
Update early, update often…
Sophos Anti-Virus for Mac Home Edition
Want to keep an eye out for malware, malicious web links and other threats to your beloved Mac?
Sophos Anti-Virus for Mac Home Edition is 100% free (email address required), with no expiry and no time limit on updates.
Sophos for Mac also stops threats for Windows too, so it even protects non-Mac users you share files with.
Choose from blocking viruses in real time (on-access protection), scanning at scheduled times, or running a check whenever you want.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Av2aFga57-k/