Apple ships OS X 10.9.2
Forget my unofficial patch for OS X!
Apple has done what it said, and delivered the latest update to Mavericks, numbered OS X 10.9.2, “very soon.”
As usual, Apple’s dedicated Security Updates page (HT1222) doesn’t yet mention what’s in 10.9.2. [As at 2014-02-26T00:44Z.]
→ For the Nth time, I implore Apple – and you should email Cupertino about it to add your voice, too – not to follow an update process that explicitly refers you to HT1222 for security information but doesn’t update that page until much later.
But the Combo Update download page does mention what we all want to hear:
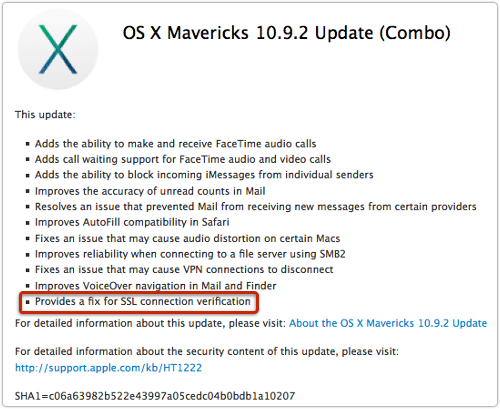
This update … provides a fix for SSL connection verification.
The notes don’t actually say CVE-2014-1266, but that’s what it’s all about.
In case you missed the brouhaha, CVE-2014-1266 was patched in iOS 7.0.6 late last week, with little more to go on than that it fixed a problem with “SSL connection verification.”
Apple generally remains pretty tight-lipped about the specifics of what it just patched, which was a bit of a pity in this case.
The brevity of the iOS notification merely egged on security researchers to answer for themselves the question, “Is it, or isn’t it, an exploitable Man-in-the-Middle hole?”
Was the bug of a fail-safe sort that might sometimes cause legitimate sites to produce errors?
Or was is a fail-soft fault that might allow imposter “secure” sites to pass muster as the real thing?
Of course, as we discussed in detail elsewhere, answering those questions also delivered the answer to, “Is the same bug in OS X?”
Yes, it is.
The bug was caused by a line of C code that says goto fail, which was a self-descriptive irony too amusing to ignore.
So the bug quickly became known as the “goto fail”, or even the “double-goto-fail.” (The error was that the line appeared twice instead of once.)
With the right preparation, an attacker who misdirected your attempts to visit, say, https://secure.example/ could have exploited the goto fail to trick you into visiting an impostor site without any tell-tale HTTPS certificate warnings popping up.
The 10.9.2 update, then, is one you ought to apply right away.
You’re probably wondering why Apple didn’t simply push out the iOS and OS X updates at the same time.
We shall probably never know for sure, but a likely reason is that the iOS update was a comparatively modest security fix, chiming in at a few tens of megabytes, while the OS X update is about 800MB, and offers a range of other changes and enhancements beyond the SSL fix.
Perhaps Apple felt it could do with a few more days of testing OS X 10.9.2?
That’s all moot now, as is my unofficial patch published on Monday, which closed off the hole with a minimalistic change of just 5 bytes to the bug-affected system file.
→ I’ve installed the official update, and I can confirm that disassembling the updated SecureTransport library in 10.9.2 shows that the certificate verification code has been repaired – including the previously missing call to the all-important sslRsaVerify() function. The new library file has version number 55471.14.0, up from 55471.0.0 in the buggy version.
By the way, while you’re waiting for the OS X 10.9.2 update to download, take heed of this lesson it teaches you.
A patch for iOS turned into sort of “attack becaon” that quickly led researchers to an identical but unpatched bug in OS X.
The two products share lots of source code, so an injury to one is frequently an injury to all.
This is the same sort of problem that will plague Windows XP when XP’s final security patch is shippped in April 2014.
Patches for Windows 7 and Windows 8 might lead researchers to an identical but unpatched bug in Windows XP.
Unlike in this case, where OS X “caught up” within a few days, Windows XP will never catch up – in fact, it will be behind for ever.
So, remember (if you will forgive Windows sticking its nose into an article about OS X) that friends don’t let friends use XP.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/zV9d3Wbgdz8/