Apple’s iOS 7.0.4 fixes a “too easy to buy stuff” security flaw
 If you’re an avid iDevice user, you’ve probably already received Apple’s fourth bug-fix release of iOS 7, unsurprisingly named 7.0.4.
If you’re an avid iDevice user, you’ve probably already received Apple’s fourth bug-fix release of iOS 7, unsurprisingly named 7.0.4.
At an average of one update every two weeks since iOS 7 launched in September 2013, you might view this a sign that Apple’s code quality has gone down, following the argument that more vulnerabilities needing patching must mean worse code.
We often hear this argument trotted out against other software vendors, with a count of known vulnerabilities used an an inverse measure of security.
On the other hand, you might view it as a sign that Apple is becoming more responsive to security issues by pushing out updates quickly, rather than waiting to bundle multiple fixes into a single patch.
Obviously, well-written software without security holes will never need updates, and will therefore rack up zero patches.
But it doesn’t work the other way around.
You can’t make poorly-written software secure by neglecting, or even refusing, to publish patches for it, so a low patch count can’t be used as a quality metric on its own.
And don’t forget that exploit-finding is now worth money, sometimes big money, so vulnerability counts are likely to rise, all other things – including software quality – being equal.
A lot of the coverage for the iOS 7.0.4 update has focused on a non-security bug fix in FaceTime, but there’s also an officially-listed security patch:

App and In-App purchases may be completed with insufficient authorization.
Description: A signed-in user may be able to complete a transaction without providing a password when prompted. This issue was addressed by additional enforcement of purchase authorization.
As far as we can tell, this flaw doesn’t mean that you can buy stuff on someone else’s dime without knowing their password.
But it could allow purchases on your device to be approved unexpectedly (or unscrupulously), so it’s good to have it fixed.
Many users probably already have the update, or will want to grab it promptly.
The only users left in uncertainty here are those who are hoping to jailbreak their iOS 7 devices some time in the future.
The irony, of course, is that jailbreaking relies on experts finding an exploitable vulnerability that can be used to liberate your iPhone or iPad from Apple’s strict lockdown.
Word on the street seems to be that a jailbreak for iOS 7 is likely soon, and will probably work against versions up to iOS 7.0.3.
But Apple might quietly have found the same hole that the jailbreakers are working away at, and have fixed it in iOS 7.0.4.
Once you upgrade, you can’t – or you’re not supposed to be able to – downgrade, which is Apple’s way of stopping you jailbreaking newer iOSes by reverting to the buggy ways of older versions.
 Some hackers are saying “not to worry,” because the changes in 7.0.4 are minor enough that they shouldn’t make any difference to the current progress towards iOS 7 “freedom.”
Some hackers are saying “not to worry,” because the changes in 7.0.4 are minor enough that they shouldn’t make any difference to the current progress towards iOS 7 “freedom.”
Until they’re sure iOS 7.0.4 is jailbreak-safe, though, some avid jailbreakers are likely to wait.
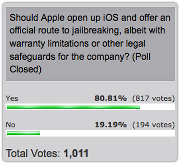
It’s a pity that Apple won’t embrace the jailbreaking community: Naked Security readers certainly seem to think they should.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/XF_5TSVHAxQ/