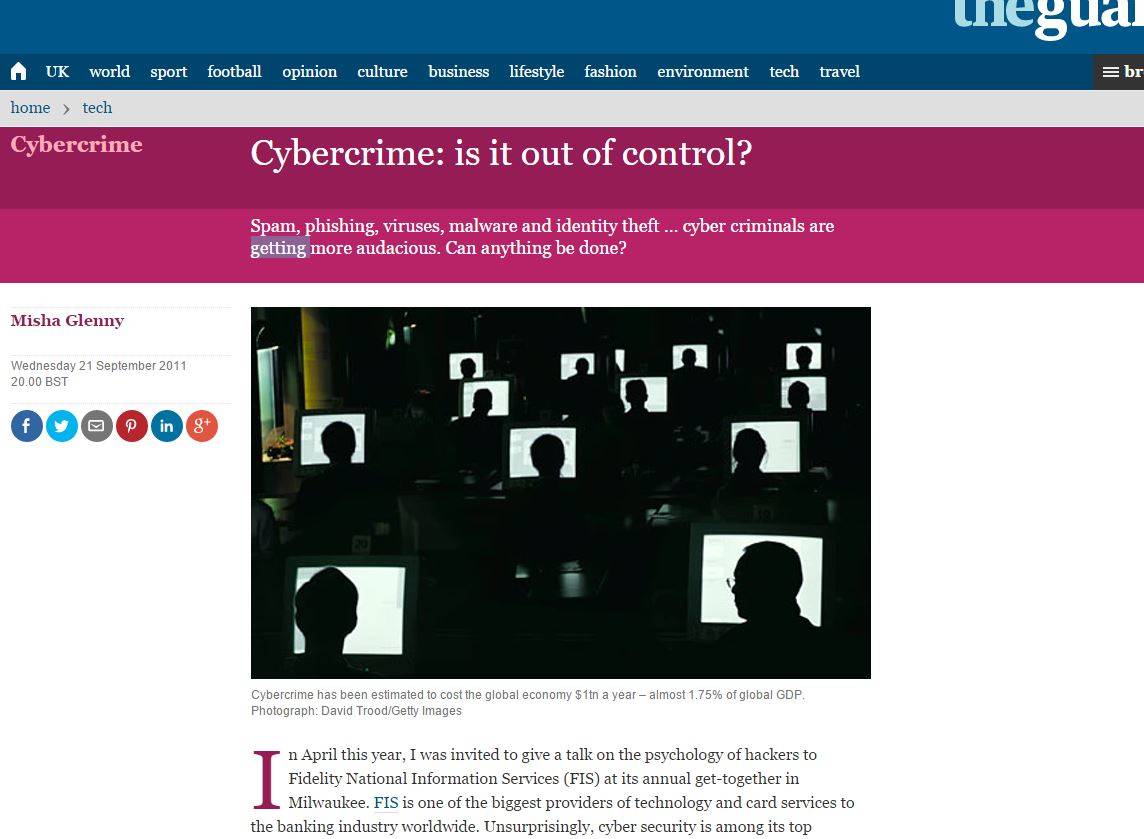
Hundreds of thousands of engine immobilisers hackable over the net
Kiwicon Kiwi hacker Lachlan Temple has found holes in a popular cheap car tracking and immobilisation gadget that can allow remote attackers to locate, eavesdrop, and in some cases cut the fuel intake to hundreds of thousands of vehicles, some while in motion.
The gadgets are rebranded white box units from Chinese concern ThinkRace that allow users to attach to their cars to enable remote tracking, engine immobilisation, microphone recording, geo-fencing, and location tracking over a web interface.
In Australia the units badged as “Response” sell for about A$150 at electronics chain JayCar or through some mechanics who offer to install the devices.
One of the unit’s relay leads is commonly attached to car fuel pumps as a means to remotely-immobilise stolen vehicles.
But session cookie vulnerabilities turn that function – in the worst case scenario – into a means to shut off fuel supply to cars while in motion over the internet.
Temple (@skooooch) told the Kiwicon security confab in Wellington today the flaws allow attackers who log into any account — including a universal demonstration account – to log into any of the 360,000 units ThinkRace claims it sold without need of a password.
“You just brute force everyone account, you can increment each one,” Temple told Vulture South.
“You could disable someone’s car if they have wired the relay, so if that happened on a freeway that is pretty dangerous.
“Most people would wire it this way, that’s the main point of it and the reason why mechanics sell it.”

Lachlan Temple. Photo by Darren Pauli / The Register
Temple says consumers can wire the relay to the starter motor meaning it would not stop the car while in motion and instead would prevent it starting up once turned off.
He says consumers should throw out the units.
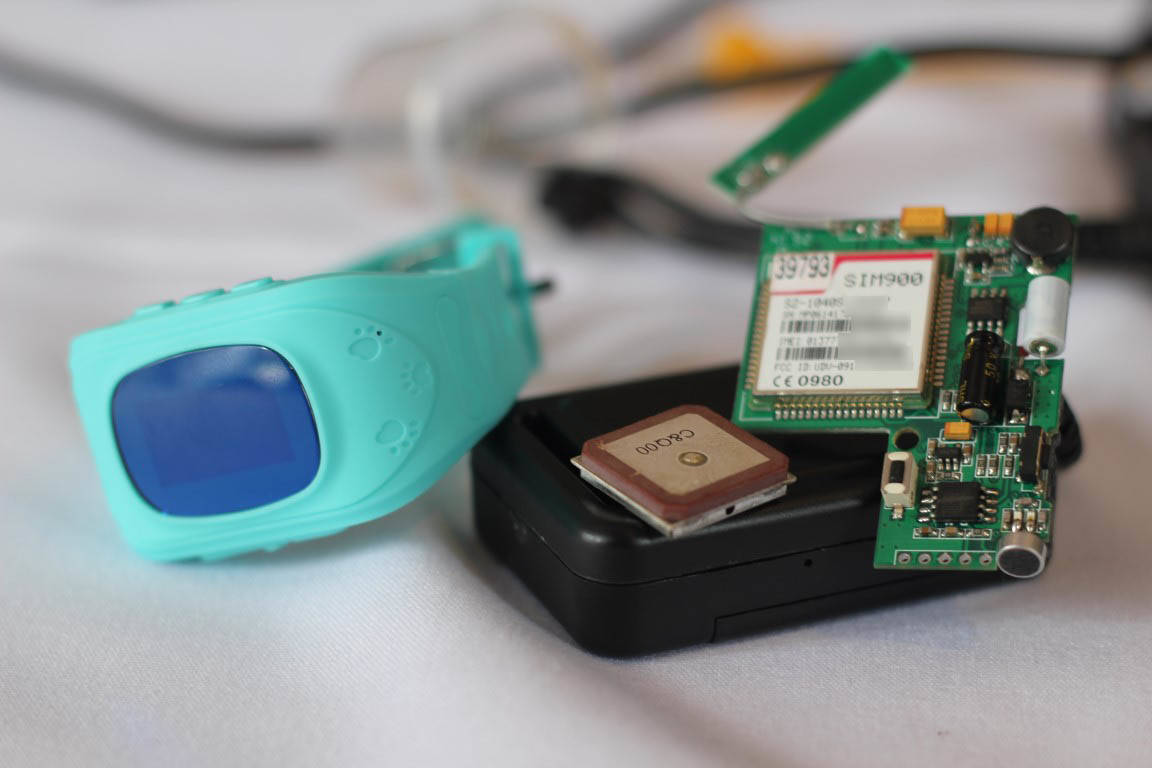
Attackers could also find user personal details including phone numbers which are registered in order for the device to issue alerts via an installed SIM card.
The GPS units and kid’s watch. Photo Darren Pauli / The Register.
A microphone installed in the devices also allows attackers to eavesdrop on cars.
The same units are built into children’s watches sold by ThinkRace and likely contain the same flaws allowing kids to be eavesdropped and tracked.
Temple will next turn his attention to more expensive tracking gadgets more likely used in commercial fleets. ®
Sponsored:
Building secure multi-factor authentication
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/12/11/hundreds_of_thousands_of_engine_immobilers_hackable_over_the_net/
 Katie Moussouris . Photo: Darren Pauli / The Register.
Katie Moussouris . Photo: Darren Pauli / The Register.