LogMeIn’s purchase by LastPass password manager service was not well received by LastPass users. In fact that outrage was sufficient that LastPass quickly shut down comments on its blog. Why the outrage and who is LogMeIn?
LogMeIn may be best known as the company that shut down its free remote desktop sharing service with a mere week’s warning in early 2014. Even in a web filled with capricious, disappearing services, LogMeIn’s mere week’s notice stands out as almost spiteful. Combine that with LastPass’s history of customer service and it’s not hard to see why users were unhappy about the deal.
For its part, LastPass says its business model is not changing and that the service will remain essentially as-is under its new owners.
Unfortunately for LastPass fans, if you dig around the Internet Archive you can find similar statements from Delicious, Pownce, Bump and countless other small services that were purchased and later abandoned. LastPass may well be different, but since there’s a chance you might only have a week to find something new, now is a good time to start looking for alternatives.
The best alternative to LastPass depends somewhat on how you use LastPass and what, if anything, you’d like to be different.
There are two broad categories of password managers. The cloud-based solutions like LastPass offer automatic syncing between devices, while others like KeePass reside on your local machine and you’re on your own for syncing (which can be done via Dropbox, OwnCloud, SpiderOak, Syncthing or any other you already use). The primary difference between the two approaches comes down to control of your data.
Cloud-based sync services store your data on their servers. The best of these offer zero-knowledge storage, which is to say that your data is encrypted and decrypted only on your devices. That means that these services, the storage system they use behind the scenes and the people working for them have no access to your unencrypted data or your encryption keys.
If you’re looking for a drop-in cloud based replacement for LastPass, there are dozens available, but the big standout is Dashlane. It has everything you’re used to with LastPass – browser plugins, autofill, password strength indicator, secure notes – and throws in a few things LastPass doesn’t offer like the ability to share a password and some digital wallet features.
Dashlane offers a free tier if you just want to try it out, but the free version doesn’t sync between devices, so to really replace LastPass you’ll need to sign up for the premium version, which will set you back $40/year. Also note that there’s no Linux client, but there are browser plugins that make it easy enough to use Dashlane on Linux.
Another noteworthy possibility in the cloud-based category is Encryptr. Encryptr is free, open source (based on the Crypton project, itself an outgrowth of SpiderOak), and reasonably cross platform. It’s currently available for Android, Windows, Linux, and Mac OS X. An iOS version is in the works, but not yet available.
Browser plug ins are a feature of Dashline
The problem with Encryptr is that it currently lacks browser integration, which makes it a considerably less capable LastPass replacement.
Other services worth investigating include the more enterprise-oriented Secret Server and AuthAnvil, as well as ZohoVault (which is offering a year of its business version for free to LastPass users). There’s also the biometric-based Sticky Password.
The problem with replacing LastPass with another, similar cloud-based service is two-fold. First you may well find yourself back here again in a few years when the new service is sold and, second, the only real advantage is the built-in syncing. But chances are you’re already using some kind of sync service – be it SpiderOak, Dropbox, Owncloud, SyncThing, and so on – why not sync your passwords yourself?
If you handle the syncing yourself, all you need to worry about is finding an application that can encrypt and decrypt your data on all your devices. Fortunately there are quite a few apps that can do that, most notably KeePass.
KeePass may be slightly confusing for newcomers since there are two variants, KeePass and KeePass X. There’s not much difference between them, though KeePass seems to have better plugin support if you’d like to add extra features like syncing to Amazon S3, a duplicate checker, or better Ubuntu integration.
KeePass is a database that stores encrypted versions of all your passwords – just like the hosted services above – that you can secure with a master password, key file or both. You can then sync that database file using the syncing tool of your choice and access it on any device that has a KeePass client. There are clients available for Linux, Windows and OS X, as well as unofficial clients for Android, iOS, Windows Phone, Blackberry and most web browsers.
Depending on your platform, KeePass may not be quite a simple as LastPass, but it does place everything directly under your control, which means you won’t have to worry about any web services shutting down or company being sold.
The last possible LastPass replacement that I’ll mention is the password manager I opted for: pass. Pass is primarily a command line tool (there are some GUIs available as well, but all are third-party tools), best thought of as a nice wrapper around GnuPG. Pass stores each site or note as a single file that’s then encrypted and decrypted using a GPG key.
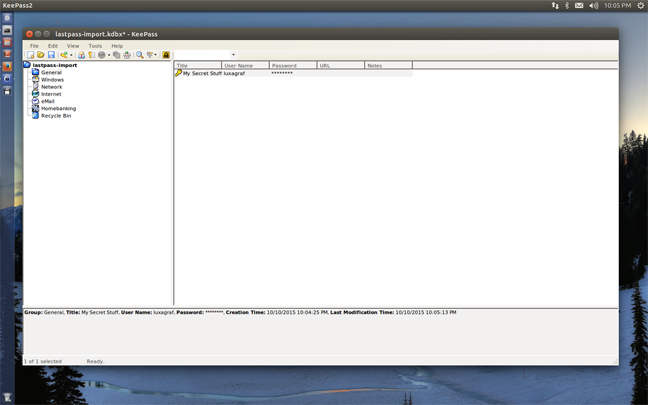
KeyPass database protection with plugin support for synching to services like Amazon S3
The pass community has created clients for Firefox and Android, which are the other two places I need to access my passwords. It’s not for everyone, but if you’re comfortable with the command line and want to keep things simple, pass fits the bill.
In a perfect world, the LastPass acquisition wouldn’t change anything – the service would just continue as it always has. However, experience shows that it often doesn’t work out that way. If you prefer not to wait around and find out, there are, fortunately, plenty of alternatives.
The good news is that LastPass hasn’t changed anything just yet, so you have time to try out the rest and see which one you prefer. I suggest starting out with KeePass or, if you want to stick with something cloud-based and closer to LastPass itself, Dashlane. ®
Sponsored:
Improve app performance in the hybrid enterprise
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/12/02/password_manager_get_out_options/