Who’s right on crypto: An American prosecutor or a Lebanese coder?
Special report The debate over encryption has become particularly intense following the deadly attacks in Paris.
Politicians, police, and government agents insist the encryption in our software and gadgets be limited. Tech companies and programmers insist the encryption be implemented fully securely.
This past week, there have been two posts from opposite ends of this debate, both argued passionately and eloquently, that highlight the complexities around the issue.
One comes from Manhattan’s District Attorney and is a 42-page report [PDF] making the case for law enforcement access to smartphones; the second is a blog post from a 25-year-old Lebanese security researcher living in Paris whose secure chat app has become the focus of media interest after the recent attacks.
The question is: who’s right? The American prosecutor or the Lebanese coder?
The two questions
The debate boils down to two basic questions. One: should investigators be able to get hold of communication data if they strongly feel it will solve a crime? And two: how would that system actually work?
With few exceptions, almost everyone agrees that, yes, the police and Feds should be able to access information that will assist in sending down criminals, so long as there are adequate measures to prevent the system from being abused.
The problem comes with the second question: how is it actually done? And here lies the problem, because the answer to that question in many respects overrides the first.
Encryption is about mathematics, not policy. If you create a system that makes data accessible only to Alice and Bob, and inaccessible to Eve, and you then try to ensure the data is somehow accessible to people indistinguishable from Eve, you have to purposefully break the system. And that break, no matter how eloquently implemented, is still a break. Once it is there, it cannot go away.
Technologists and coders have become increasingly outspoken about the fundamentally flawed logic of creating an encryption system with a hole in it, in significant part because Edward Snowden revealed the lengths to which the US government was prepared to go to access all data.
Previously, tech companies had reached an uneasy agreement that they would include carefully designed holes in their systems so information could be provided to a third party in extreme circumstances – typically the production of a search warrant.
And while local law enforcement – like our prosecutor from New York – largely stuck to that agreement, it was clear that the security and intelligence services did not. Once the hole exists, if you know its full details, you are free to access information on anyone using that system.
With smartphones in particular becoming increasingly important to everyone’s privacy, ready access has become far more than logging suspicious activity. Your phone now contains your interactions with friends and family; personal pictures; your locations now and over time. With apps, your phone contains your financial information, your searches for information, access to secure work networks, your personal life.
In his report, Cyrus Vance Jr, the Manhattan District Attorney, argues: “What makes full-disk encryption schemes remarkable is that they provide greater protection to one’s phone than one has in one’s home, which, of course, has always been afforded the highest level of privacy protection by courts. Every home can be entered with a search warrant. The same should be true of devices.”
Except in many respects, smartphones contain more personal information than your own home – and all in one tiny portable device. While you may be able to find details on people’s personal finances in a filing cabinet in a house, there won’t be a drawer – even a locked one – that contains the details of every location you visited in the past few weeks, complete with timestamps.
In your house, you may have left some letters, or even printed out an email. You may have photo albums. But the interactions we have these days with our phones are more akin to recording our voices. Law enforcement needs more than a search warrant to install a bug in your home. And while people still keep photo albums, they don’t come with GPS coordinates and instant links to the identities of the other people pictured.
In short, while entering your home is a significant invasion of privacy, the physical interference is actually likely to reveal less about yourself than the ability to go through your phone.
The law enforcement case
That said, Vance does make a persuasive case.
His report [PDF] includes real-world examples of where access to people’s phones has led to real evidence that has led to real convictions. And the examples are harrowing:
- A man accidentally filmed his own murder. The recovered video supported eyewitness accounts and the shooter was found guilty and given 35 years.
- Text messages sent between two accused rapists concerned the use of mace spray which is being used as a piece of evidence in their trial.
- Child abuse images were taken off a phone after the owner showed one to a taxi driver.
- A sex trafficker’s phone contained photos of him posing with women who appeared in online prostitution ads. They were used in his trial and helped lead to his conviction.
- A credit card swiping ring that fleeced restaurant customers of over $1m was taken down thanks to the details on a phone from one of the waiters involved.
- A murder suspect was actually cleared when his phone’s details made it clear he was not involved; a second phone found at the scene of the crime led to the person responsible.
The prosecutor makes the argument that if tech companies do not include some method for accessing information then “we risk losing crucial evidence in serious cases if the contents of passcode-protected smartphones remain immune to a warrant.”
Unlocking ‘droids
There’s an interesting factoid in the report – Google can remotely unlock up to 77 per cent of Android devices today:
“Forensic examiners are able to bypass passcodes on some [Android] devices using a variety of forensic techniques. For some other types of Android devices, Google can reset the passcodes when served with a search warrant and an order instructing them to assist law enforcement to extract data from the device. This process can be done by Google remotely and allows forensic examiners to view the contents of a device.
“For Android devices running operating systems Lollipop 5.0 and above, however, Google plans to use default full-disk encryption … that will make it impossible for Google to comply with search warrants and orders instructing them to assist with device data extraction. As of October 5, 2015, approximately 23 per cent of Android users were running Lollipop 5.0 or higher.”
And the paper cites a conversation from jail in which an inmate asks a friend to check what operating system his iPhone is using. They upgraded their phones at the same time and the fact that the friend’s phone was running iOS 8 meant that the cops would not be able to access his phone data. “That means God might be in my favor. I don’t think they can open it,” the inmate said over the recorded phone line. “I mean, you know how much shit is on that phone.”
If the only way to access a phone’s data is for the user to type in their personal passcode, then the police will be missing out on hugely valuable information. “It is the rare case in which information from a smartphone is not useful; rather, it is often crucial,” he argues, citing 111 search warrants between September 17, 2014 and October 1, 2015 where his office was not able to get at phone data because of new encryption standards.
And it wasn’t just suspects refusing to hand over the code: in some cases, the phone belonged to a dead victim. It is not hard to imagine the enormous frustration that must exist in a detective at a crime scene if she is simply not able to get at what may be critical evidence because she doesn’t know what the correct four numbers are.
In short, the district attorney argues that the previous system – where the authorities would get a search warrant after it had persuaded a judge of “probable cause” and then send it with the phone to the manufacturer’s headquarters in California and get a hard drive back in return with all its contents – was a good balance between security and privacy.
It gave law enforcement what it needed; it meant that the average Joe was not impacted. Getting access to details through cloud-storage rather than directly from a phone was also not equivalent, Vance argues, even producing a table that highlights the sort of information that can be acquired from phones themselves, cloud storage, and network operators.
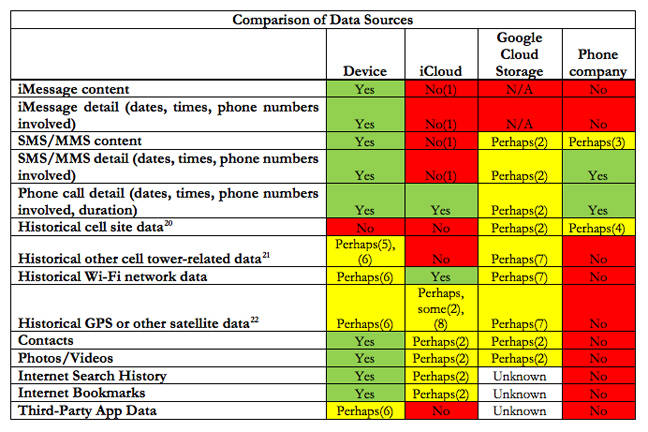
A table from the Manhattan District Attorney pointing out what data can be accessed by different means
The district attorney rails against the default encryption that Apple and Google have introduced that means they don’t have ready access to a phone’s data, and argues for a new law to pass through US Congress that would make it a requirement for “any designer of an operating system for a smartphone or tablet manufactured, leased, or sold in the US to ensure that data on its devices is accessible pursuant to a search warrant.”
Sponsored:
OpenStack for enterprise: The tipping point cometh
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/11/24/perspectives_on_encryption/