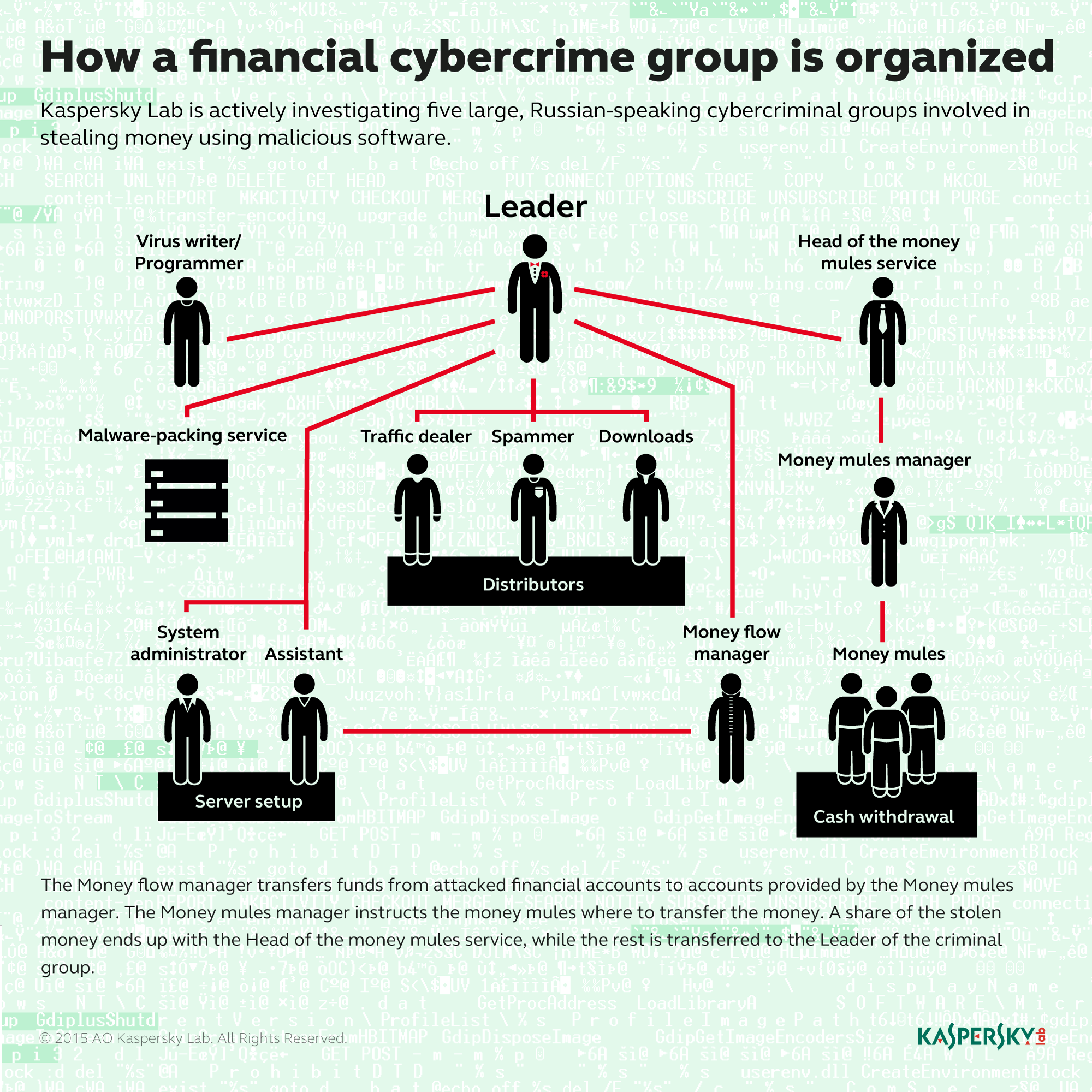
Mostly harmless: Berlin boffins bleat post epic TrueCrypt audit feat
Ten auditors from the lauded Fraunhofer Institute for Secure Information Technology have given TrueCrypt a security tick after completing a comprehensive six-month audit under contract from the German Government.
The 77-page report dug up extra vulnerabilities in the once-popular encryption platform but say none are sufficient to undermine the jettisoned software.
The unknown and mysterious authors of TrueCrypt abandoned the platform in May last year, leaving behind what appears to many to be a sly warrant canary warning users that it is not secure.
Since then a separate team of researchers under the Open Crypto Audit Project in April found TrueCrypt to be “well-designed”.
In September Google’s James Foreshaw found privilege escalation holes that the former audit missed and have since been fixed in the VeraCrypt spin off.
Now boffins Germany’s Federal Office for Security in Information Technology have shed more light on the software in the staid Security Analysis of TrueCrypt (PDF) paper, revealing new flaws in the process but giving the platform a security tick.
“Our general conclusion is that TrueCrypt is safer than previous examinations suggest,” wrote Research lead and Technische Universität Darmstadt professor Eric Bodden.
“I would say that the TrueCrypt code base is probably alright for the most parts.
“The flaws we found were minor, and similar flaws can occur also in any other implementation of cryptographic functions. In that sense TrueCrypt seems not better or worse than its alternatives.”
Bodden says code could do with some refactoring and better documentation, however.
The paper expands on Bodden’s thoughts but gives the same ‘mostly harmless’ verdict, as follows:
“Overall, the analysis did not identify any evidence that the guaranteed encryption characteristics are not fulfilled in the implementation of TrueCrypt. In particular, a comparison of the cryptographic functions with reference implementations or test vectors did not identify any deviations. The application of cryptography in TrueCrypt is not optimal. The AES implementation is not timing-resistant, key files are not used in a cryptographically secure way and the integrity of volume headers is not properly protected.”
They point out that TrueCrypt cannot protect against active attacks like keyloggers and other malware which requires things like Trusted Platform Modules or smartcards. ®
Sponsored:
OpenStack for enterprise: The tipping point cometh
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/11/23/truecrypt_anlaysis/