Members of the hacker collective Anonymous have declared war on the Islamic State, after the radical terrorist group claimed responsibility for the horrific attacks in Paris that killed over 120 people.
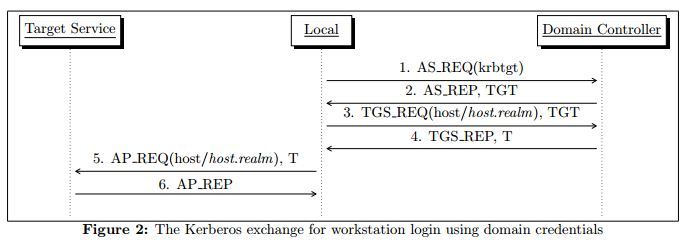
In a video posted to YouTube the day after Friday’s attacks, a man wearing a Guy Fawkes mask read a statement calling the attackers “vermin” and warning the Islamic State to prepare for “many cyberattacks.”
Speaking in French, the man said Anonymous would “hunt down” the attackers just as its members did after the terrorist attack in January 2015 on the French satirical magazine Charlie Hebdo, according to an English translation of the video:
On Friday 13 November our country France was attacked in Paris for two hours, by multiple terrorist attacks claimed by you, the Islamic State.
These attacks cannot go unpunished. That’s why Anonymous activists from all over the world will hunt you down. Yes you, the vermin who kill innocent victims, we will hunt you down like we did to those who carried out the attacks on Charlie Hebdo.
So get ready for a massive reaction from Anonymous. Know that we will find you and we will never let up. We are going to launch the biggest ever operation against you. Expect very many cyberattacks. War is declared. Prepare yourselves.
Know this: the French people are stronger than you and we will come out of this atrocity even stronger.
Anonymous sends its condolences to the families of the victims.
We are Anonymous. We are legion. We don’t forgive, we don’t forget. Expect us.
The video had been seen over 1.8 million times as of 7:30 pm GMT on Monday (16 November).
The video did not explain when or how those “cyberattacks” would happen, but on Monday, self-described Anonymous members said on Twitter that the attacks had begun.
After the attack on Charlie Hebdo in January, Anonymous members launched an #OpISIS to hack pro-Islamic State websites and social media accounts.
Another round of similar ops appears to be underway – #OpISIS and #OpParis.
By its nature, Anonymous is decentralized, and multiple Twitter accounts affiliated with Anonymous are taking credit for cyberattacks against the Islamic State.
One Twitter account, @opparisofficial, tweeted Monday that over 3800 pro-Islamic State Twitter accounts had been taken down.
Reuters reported that Anonymous members claimed to have identified 39,000 pro-ISIS accounts and reported them to Twitter, which supposedly took down 25,000 of those accounts.
Another Twitter account, @AnonyOpNews, Tweeted that Anonymous’s attacks on the Islamic State (also called ISIS, ISIL, and Daesh) would involve naming members of the terrorist group, similar to what Anonymous members did in an op against members of the Ku Klux Klan earlier this month.
And yet another Twitter account, @GroupAnon, declared war with the Islamic State, and stated that members of Anonymous are “better hackers.”
The Islamic State has used social media to recruit individuals to join its cause, and has used platforms like Twitter to threaten its enemies, including the United States.
Last month, a Malaysian man was arrested for allegedly providing material support for the Islamic State by hacking a US web hosting company to steal the identities of US service members and government employees.
The names and other identifying information of 1300 US service members ended up in the possession of a British citizen named Junaid Hussain, aka Abu Hussain Al-Britani, the leader of the Islamic State Hacking Division who was later killed in a US airstrike.
Hussain published the information via Twitter with instructions that sympathizers of the Islamic State should kill US service members “in their own lands.”
Pro-Islamic State hackers calling themselves the CyberCaliphate took over the Twitter and YouTube accounts of the US Central Command (CENTCOM) in January.
Despite Anonymous’s apparent intentions to join what is a global effort to defeat the Islamic State, it’s not clear that their tactics are effective, and they may even be counterproductive.
Some foreign policy analysts have said Anonymous taking out Islamic State websites and social media accounts could hurt intelligence-gathering by military and intelligence agencies that track the Islamic State through its online activities.
Meanwhile, social media has also served as an important source of information, and a way for people trying to connect with loved ones in the aftermath of the attacks.
Facebook turned on its Safety Check tool, helping people in France communicate that they were safe.
People all over the world took to social media on Friday after the terrorist attacks in Paris to express grief, anger and solidarity with France.
One of the most popular responses on social media – a simple, hand-drawn sketch of the Eiffel Tower resembling the peace symbol, created by a French graphic designer named Jean Jullien – went viral in the hours after the attacks.
Anonymous has been known to misfire with its approach, misidentifying people in its #OpKKK last month with no connection to the hate group, and use of illegal tactics such as distributed denial-of-service attacks.
Jullien’s stroke of the pen is, in my opinion, the more powerful and far-reaching response to the terrorist attacks.
Screenshot of Anonymous video via YouTube.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/onsGyjYizhA/