BadBIOS is back
 The Federal Trade Commission (FTC) is the offical consumer watchdog in the USA.
The Federal Trade Commission (FTC) is the offical consumer watchdog in the USA.
As you can imagine, the FTC is particularly interested in dodgy marketing practices.
These days, that doesn’t only involve accuracy and fairness, but also covers issues such as how personal information about potential customers is collected and used.
For example, in recent months, the FTC has acted against a range of online activities that it has deemed devious, deceptive or dishonest, such as:
- A mobile phone tracking company that claimed to have an opt-out feature, yet not only failed to tell you about it, but also didn’t opt you out even if you found out what to do and asked.
- A Kickstarter project operator who attracted significant investment but then made little or no effort to spend the money as claimed, instead using it for his own “unjust enrichment”.
- A diet pill company that made unreasonable promises for its products, backed up its ads with fake endorsements, and violated anti-spam laws to spread the word.
Where next?
Today, the FTC is holding a workshop in Washington DC entitled Cross-Device Tracking.
Tracking you via your browser, or by means of a mobile app, is fairly straightforward, for example by setting a browser cookie, or using a unique identifier in the app.
Even if marketers don’t know who you are, they can target you more effectively with ads (or so that say, at any rate) if they know something about your interests and your product preferences.
And if they can feed you ads that are more likely to work, they can charge their customers more, and everyone is happier, including you (or so they say).
But tying together those identifiers between different devices is altogether more difficult.
You might have a cookie code of LNT67QTABZID in Firefox on your Windows laptop, but an advertising identifier of 13N5TSDFFYHT on your mobile phone.
To an online marketing company, that’s effectively two people – unless and until they figure out that the same person is denoted by both those codes.
Once they’ve done that, each code can stand in for the other, so both your laptop and your mobile activities can be tied back to you from then on.
Obviously, if you login to the same service as the same user on two different devices, that lets a service provider associate both those devices to you.
Likewise, a company might offer you a free service such as Wi-Fi, redemeed via a code that is SMSed to your phone, which lets them tie your laptop and phone together in future.
The FTC refers to this as deterministic tracking, because there is an explicit element to it, and there is at least some opportunity for you to give informed consent.
Probabilistic tracking
More worrying is so-called probabilistic tracking, where what you do and how you do it – such as device type, operating system version, screen resolution and IP number – is used to infer which devices probably have a common user.
As the FTC points out:
Such “probabilistic” tracking is generally invisible to consumers and, unlike tracking through cookies, the consumer has no ability to control it. Accordingly, this practice raises a number of privacy concerns and questions.
Inaccuracy is perhaps as much of an issue in systems of this sort.
A company could use all sorts of measurements, such as how you move your mouse, the way you type, and many other digital flourishes, as if they offered identification, not merely supposition.
And then, of course, they could sell on these unreliable “identifications” to third-party companies, where they might end up working against you in an almost Kafkaesque way.
BadBIOS is back
One of the most intriguing – and perhaps the most outlandish – technique for cross-device tracking is mentioned in the public comment submitted to the FTC’s workshop by the DC-based Center for Democracy and Technology (CDT).
The CDT makes reference to an Indian company that claims to offer a TV-to-smartphone tracking system that works, if you can believe it, using ultrasound.
Just like the BadBIOS controversy from late 2013, which was supposed to be hardware-level malware that could steal data even across a so-called network “air gap,” such as the one that exists between the average TV and smartphone.
The idea is that you can use regular audio waves to transmit data between two computers that have no other sort of network connection.
In the early days of modems, this technique was quite common, using an acoustic coupler that played modem tones directly into the mouthpiece of a regular telephone to transmit data from a remote site.
But BadBIOS introduced a new twist: unlike a landline voice telephone, modern devices have loudspeakers and microphones that are capable of producing and recording sounds at frequencies beyond the range of a normal human ear.
In theory, then, or at least in the laboratory, a even a computer (or a TV) with no LAN connection, no Bluetooth and no Wi-Fi, could produce sounds that a co-operating device nearby could receive and interpret as data, and you wouldn’t be able to tell.
Unlike the telltale tones of a modem connection, such as you can hear in the jingle at the start of every Sophos Security Chet Chat podcast, high-frequency sounds may be “audible” to a mobile phone’s microphone, but undetectable to the human ear.
Ultrasound tracking
The company described in the CDT’s documents claims that its mobile app framework can detect ultrasonic data codes that you embed in the soundtrack of your TV ads.
The idea is that if a viewer’s phone is turned on, and in range of the TV, and they have one of your apps installed and running, you will be able to tell whether they saw your commercial.
You’ll even be able to tell whether they switched channels during the commercial, or fast-forwarded through it.
If they didn’t skip the commercial, of course, you still won’t know whether they actually watched it or not.
Unless – and who can say? – you have another app that can keep track of the viewer’s smart home devices and monitor water usage (e.g. a toilet flush) or power consumption (e.g. a kettle activation) to help you guess whether they used the commercial break for other households tasks.
As the CDT notes, the insidious aspects of this sort of tracking are that:
[The tracking company’s] policy is to not “divulge the names of the apps the technology is embedded,” meaning that users have no knowledge of which apps are using this technology and no way to opt-out of this practice.
There’s nothing fundamentally wrong with tracking TV viewers’ habits, whether by explicit network feedback from a smart TV, or by audio feedback from a non-networked TV, provided that they know it’s happening, have agreed to it, and know they can withdraw that agreement at any time.
But just the mention of ultrasound, even without its memories of the BadBIOS story, and of mobile apps that secretly use your microphone to detect inaudible content, does have a whiff of deceit about it.
If mainstream apps – we’re thinking of Skype, Facebook and others – are willing to come clean about whether they use this sort of technology or not, we’ll be able to defeat this sort of tracking by deciding which apps we trust with our microphone.
So we await the outcome of the FTC’s workshop with interest!
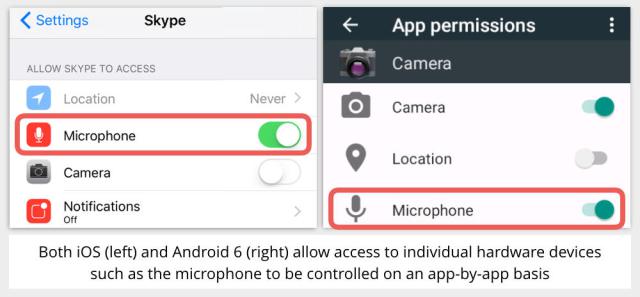
Will it actually work? Can inaudible ultrasonic frequencies make it to a viewer via the compression used by digital TV, for example? Audio compression relies on saving bandwidth by throwing out parts of the audio signal that don’t affect its clarity much, or even at all. Obviously, ultrasonic frequencies can unexceptionally be discarded altogether, because they have no effect on what a listener will hear. So broadcasters would, presumably, need to co-operate by using non-standard transmission encodings. We’re sceptical about the practicability of this system, but it is at least theoretically possible, and thus well worth considering at the FTC’s workshop, if only because it raises important issues about consent.
💡 LEARN MORE: BadBIOS malware explained ►
💡 LEARN MORE: Security and privacy on your phone ►
💡 FREE TRIAL: Sophos Mobile Control ►
Horror TV image courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/ina8tYvrkII/