Three men at the head of ‘diversified criminal conglomerate’ used hacking to commit and enhance their securities fraud, illegal online gambling, illegal Bitcoin exchange, and illegal payment processing businesses, 23-count indictment alleges.
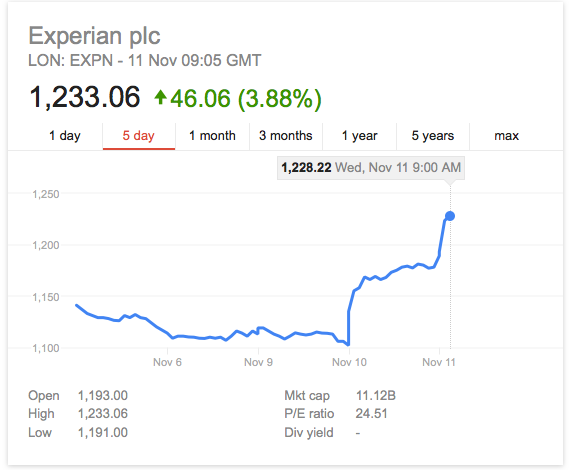
A 23-count indictment unsealed today shows that the 2014 JP Morgan Chase breach — which resulted in the theft of 83 million customers’ data — wasn’t just the work of talented cyber attackers. The breach was just one of the myriad illegal activities conducted by a “diversified criminal conglomerate” fueled by hacking.
The charges against Israeli citizens Gery Shalon and Ziv Orenstein, arrested in July, and U.S. citizen Joshua Samuel Aaron, who is still at large, include hacking, securities fraud, wire fraud, identity theft, illegal Internet gambling, and conspiring to commit money laundering. In a separate but related indictment unsealed today, Florida resident Anthony Murgio was charged for operating an unlicensed Bitcoin exchange services. The maximum sentences for the charges against Shalon alone, who is considered the “ringleader,” add up to over 200 years in prison.
“The charged crimes showcase a brave new world of hacking for profit,” said Manhattan U.S. Attorney Preet Bharara in a statement. “It is no longer hacking merely for a quick payout, but hacking to support a diversified criminal conglomerate. This was hacking as a business model.”
Cybercrime was used to commit, support, or enhance all of the group’s other illegal endeavors.
Between 2012 and 2015, Shalon and Aaron stole personally identifiable information from JP Morgan Chase, and eight other businesses operating within the financial services sector. They then used that stolen data to “artificially manipulate” the price of certain stocks, by marketing those stocks to the customer lists in a “deceptive and misleading manner,” according to the Department of Justice release.
“The alleged conduct also signals the next frontier in securities fraud,” said Bharara, “sophisticated hacking to steal nonpublic information, something the defendants discussed for the next stage of their sprawling enterprise. Fueled by their hacking, the defendants’ criminal schemes allegedly generated hundreds of millions of dollars in illicit proceeds.”
The attackers owned and operated unlawful Internet gambling businesses, and used cybercrime to protect those shadowy companies’ interests. Shalon broke into the networks of software providers the gambling businesses used, and monitored the emails of those software companies’ executives, to make sure their work with other gambling businesses didn’t compromise Shalon’s.
They owned and operated payment processors, IDPay and Todur, for illegal businesses — taking cuts of the profits from illegal pharmaceutical suppliers, malware distributors, and unlawful online casinos. They used cybercrime to protect that operation as well. Shalon and his co-conspirators hacked into an organization that monitors merchants and payment processors for trading in unlawful goods and services. The criminals then monitored that organization’s emails and detection efforts in order to prevent their own payment processors’ illicit activity from being detected.
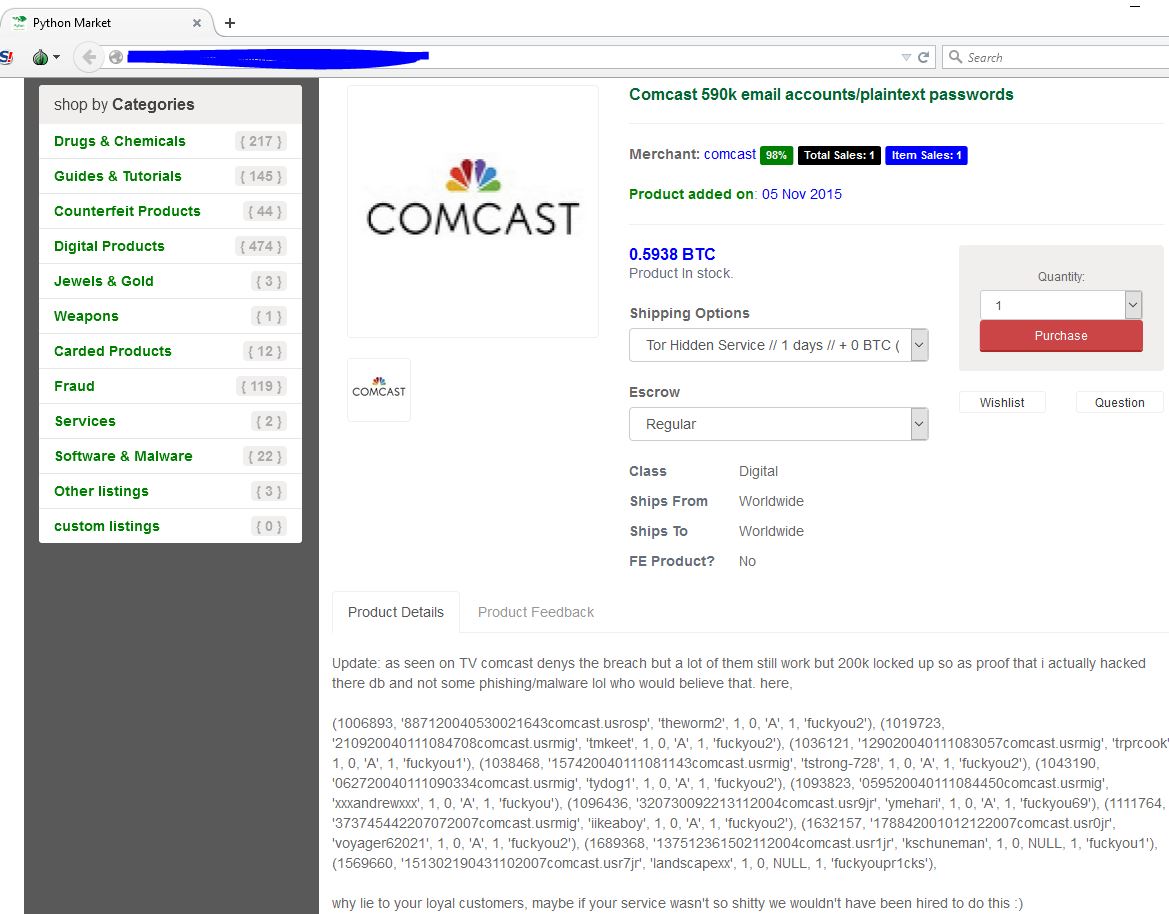
All told, 14 companies were breached.
Idan Tendler, CEO of FortScale and former commander of the 8200, the cyberwarfare division of the Israeli Defense Forces, says “The shocking size and reach of this cyber breach underscores the sophistication of today’s cyber criminal enterprises and shows what security teams across all industries are up against. Today’s hackers aren’t necessarily looking for a quick payday. Once the initial data theft is completed, there are countless opportunities for cyber criminals to conduct targeted campaigns.”
“The theft of data from [JP Morgan Chase] and the breaches at financial news outlets provided the ingredients to execute a very scalable and very profitable cyber crime operation,” says Fred Kost, SVP at HyTrust. “Stolen information such as that from JPMC and other financial institutions is not only valuable to cybercriminals as the identity of an individual, but they can also use it in many different second order actions to provide context for more elaborate attacks and schemes for financial gain. It was as if they were running diversified lines of business, all well orchestrated and vertically integrated.”
Philip Lieberman, president of Lieberman Software, says that part of the trouble lies in whether financial services companies and stock exchanges can change their culture to adapt to new risks. “Changing a ship designed for commerce into one suitable for both trade and warfare takes time and wisdom,” says Lieberman. “The challenge is not the change in technology, but with the behavior of all involved. Those charged with movement of goods tend to obstruct the need to arrive safety by depending on their knowledge and behaviors obtained long before the warfare began.”
Shalon, Aaron, and Orenstein evaded authorities as long as they did by filtering their proceeds through 75 shell companies, banks and brokerages across the world, and by using aliases — between the three of them they used over 200 fake identities, and over 30 false passports purporting to be issued by the United States and 16 other countries.
“While we continue to see breaches go undetected for long periods of time, it’s unlikely operations of this magnitude will become commonplace. They are harder to carryout undetected,” says Kost. Nevertheless, “We will likely see more of these creative ways of monetizing stolen information in the future as attackers evolve and look for newer ways to profit from hacking.”
Sara Peters is Senior Editor at Dark Reading and formerly the editor-in-chief of Enterprise Efficiency. Prior that she was senior editor for the Computer Security Institute, writing and speaking about virtualization, identity management, cybersecurity law, and a myriad … View Full Bio
Article source: http://www.darkreading.com/attacks-breaches/jp-morgan-breach-only-one-piece-of-vast-criminal-enterprise-indictments-reveal/d/d-id/1323084?_mc=RSS_DR_EDT