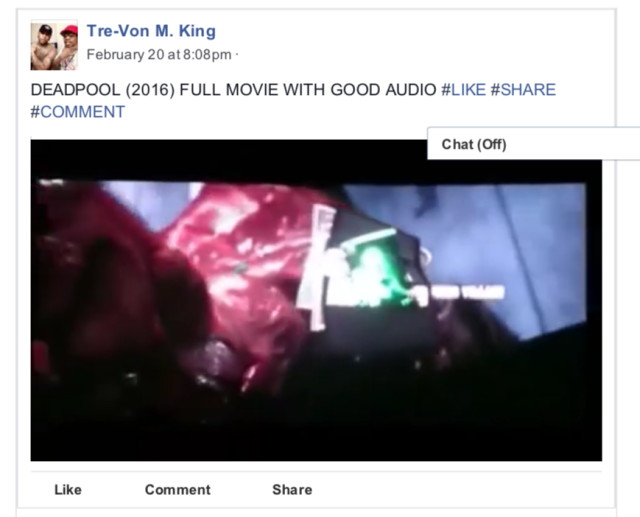
Man who shared Deadpool movie on Facebook faces 6 months in jail
You can share how much you liked a movie on Facebook, but you’re not supposed to share the actual movie on Facebook! Trevon Franklin did it anyway, and now he’s facing six months in jail.
The 22 year-old, who went by the name ‘Tre-Von M. King’ on Facebook, pled guilty this year to sharing a pirated copy of the movie Deadpool on his Facebook page, just a week after it hit theatres. In a sentencing memorandum issued on 12 September, the US government recommended six months behind bars.
In 2016 Franklin, then 20 years old, uploaded the movie to his Facebook account:
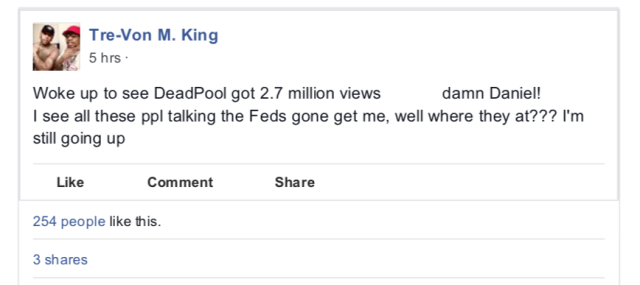
It went viral, and the file was viewed six million times, according to the court papers.
People warned him that it wasn’t wise and may earn him some interest from law enforcement, but he remained unperturbed, arguing that he had never sold the movie online. Anyway, the feds hadn’t come after him, he pointed out.
Then he created a new group called “Bootleg Movies” where he promised to share more.
“Someone going to catch a case 5 years have fun with that”, said one commenter in response. Another just posted an excerpt from the FBI anti-piracy warning, adding: “You’ll realize how bad you’ll wish it didn’t go viral.”
Among those that saw all this were representatives of Twentieth Century Fox, who were not pleased. The FBI was alerted, and started an investigation that led to his arrest in June 2017.
He was indicted with reproducing and distributing a copyrighted work, which carries a maximum three-year sentence. In June this year, he pled guilty to a misdemeanor.
Franklin’s lawyers outlined a troubled childhood fraught with personal difficulties. In a letter to the court, he said:
I [now] understand that every action has its consequences… I regret posting the movie. I didn’t think how serious the crime was that was being committed. I know not to commit a crime like copyright infringement again, or any crime because I am a father not a criminal.
In the sentencing memorandum, the government asked for him to serve six months, followed by a year of supervised release, and a mandatory fine of $100…
Given the brazen and public manner in which defendant both flouted the law (which was pointed out to him by several Facebook users) and appeared not to care that he was willfully infringing on Fox’s copyright (which was also pointed out to him by Facebook users), and given defendant’s insistence that he was not going to suffer any consequences for his crime, other than to “become more famous”.
The government added that the sentence would be a deterrent for Facebook users who may otherwise believe that there are no consequences for sharing illegal material online.
Franklin’s actions might strike readers as the misguided act of one incredibly misinformed Facebook user, but this isn’t an isolated case.
Business Insider reported that there are plenty of Facebook groups, with tens of thousands of members, hosting and publicly sharing pirated content. We were able to find free copyrighted movies readily available on the site in less than sixty seconds with a quick search.
In the last few days, Facebook has told us that it is now smart enough to distinguish between fake images and legitimate ones. Will pirated content be next in Facebook’s clean-up strategy?
Follow @DannyBradbury
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/u0hoOLTqAHw/