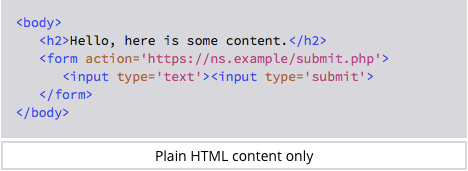
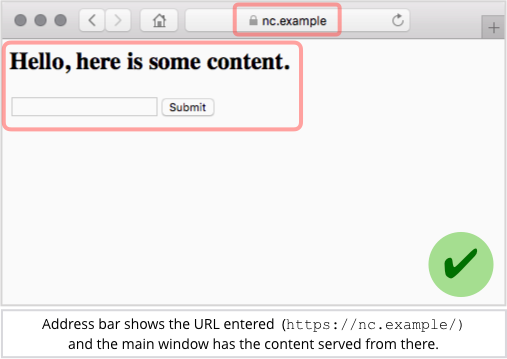
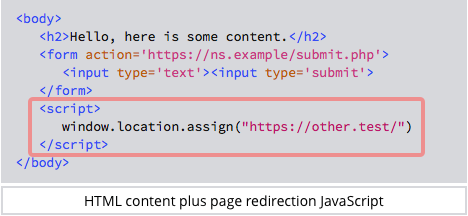
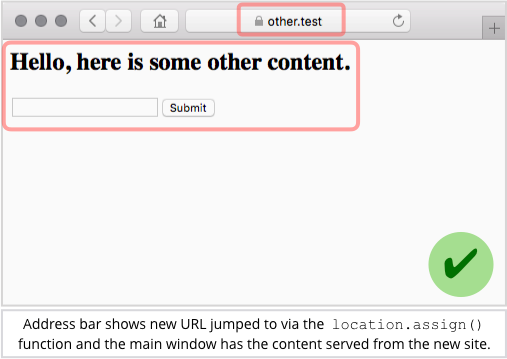
Military, Government Users Just as Bad About Password Hygiene as Civilians
Military and government users aren’t engaging in password hygiene any better than their brethren in less sensitive, private-sector positions, according to a new study out this week, which shows both sides creating weak passwords at about the same rate.
The examination of password strength came by way of WatchGuard Technologies’ Q2 2018 “Internet Security Report,” which analyzed a data dump of 117 weakly encrypted credential pairs protected only with SHA-1 hash functions from a 2012 breach at LinkedIn. The study showed that credential pairs associated with .mil and .gov accounts were easily crackable — within a week — about 50% of the time. This was only slightly less than the rate of weak passwords in pairs associated with civilian accounts, which were at about 52%.
Among the sample of cracked government passwords were plenty of common doozies that typically make it into bad password hall of shame lists. The top two bad passwords in government-associated accounts were, respectively, “123456” and the ever-present “password.”
“We didn’t find many surprises in that the most commonly used bad passwords remained largely the same,” wrote WatchGuard researchers. “However, it should be quite surprising that government and military entities use such horrible password practices. We can only hope that these were all dummy accounts that weren’t used for anything of consequence.”
Clearly, the sample set wasn’t among credentials for government systems, so the results need to be taken with a large grain of salt here. But the prevailing point remains that these government and military users should probably know better than to use bad passwords anywhere they set up an account. The fact that many of them don’t heed hygiene best practices can probably be extrapolated to at least some degree across the rest of their digital footprints. When government agencies don’t account for this universally weak human factor of passwords, there’s bound to be rampant insecurity of accounts.
“For our federal government, no amount of budgetary pressures or other excuses should be tolerated when it comes to failing to have utilized a basic cybersecurity technique, such as MFA — especially since ‘user convenience’ is not the overriding concern,” says Todd Shollenbarger, COO of Veridium, who adds that NIST’s update of its Digital Identity Guidelines has done the hard work of outlining what needs to be done to shore up credentials. “What’s now needed — obviously — is for our federal government agencies to use it.”
And in separate but related news, this week a group of US senators chastised Secretary of State Mike Pompeo for lack of multifactor authentication (MFA) adoption within the Department of State.
“We urge you to improve compliance by enabling more secure authentication mechanisms across the Department of State’s information systems,” wrote Sens. Ron Wyden, Cory Gardner, Edward Markey, Rand Paul, and Jeanne Shaheen, referencing a General Service Administration (GSA) that showed the agency had only deployed MFA across 11% of required devices. “This password-only approach is no longer sufficient to protect sensitive information from sophisticated phishing attempts and other forms of credential theft.”
- Authentication Grows Up
- Beyond Passwords: Why Your Company Should Rethink Authentication
- 4 Benefits of a World with Less Privacy
- ‘Security Fatigue’ Could Put Business at Risk

Black Hat Europe returns to London Dec 3-6 2018 with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions and service providers in the Business Hall. Click for information on the conference and to register.
Ericka Chickowski specializes in coverage of information technology and business innovation. She has focused on information security for the better part of a decade and regularly writes about the security industry as a contributor to Dark Reading. View Full Bio


![Cold boot attack variant mighe be used to steal encryption keys from laptops Chilling reality of cold boot attacks [source: F-Secure]](https://stewilliams.com/wp-content/plugins/rss-poster/cache/8c65f_cold_boot_attack.jpg)