This fall – very likely in September – Apple will unveil the next major release of its mobile operating system, iOS 12. The beta version of iOS 12 has been available for a little while now, so I took it for a test and tried out some of the security-related changes we’ll see rolling out when it is released.
Safari stomps out social trackers
Apple has been making a point to position itself as taking user privacy seriously on a number of fronts. With the iOS 12 update, Safari takes a cue from a number of other browsers in slapping the hands of social media trackers and forcing them to stop tracking users.
From iOS 12, Safari will both stop advertisers from knowing uniquely identifying information about the user’s phone, and stop sharing-buttons and comment boxes from tracking users unless the user has opted in to interacting with those buttons/boxes.
This will prevent social media sites (read: Facebook) from keeping tabs on users when they’re not using the sites, and will also prevent advertisers from tracking phone users (to serve up highly-targeted ads, of course) while they’re going about their browser-y business.
Many browsers already had either built-in or add-on features for the privacy-minded, in some cases quite similar to what Safari will now offer – for example, Firefox’s Facebook Container add-on. A notable difference here is that these tracking protections will now be present in the browser by default, guarding the privacy of users who may not even have realized they were being tracked in the first place.
iOS can now update automatically
After installing iOS 12, your phone will reboot, and as with all major iOS updates, you’ll go through a brief initialization process. These are usually pretty similar – enter your iCloud credentials, and set up a passcode if you haven’t already (and you should). However, this time, a new feature stood out: Enable automatic updates for iOS.
Right now, users have to manually download and install each iOS update. Given all the incremental updates that roll out between major versions, this can be both burdensome to users and suboptimal for security reasons: Users who don’t install updates right away (or don’t know how) are missing out on updates that could protect them from active threats and attacks.
Apple will now put the option unskippably front and center for its iOS users as they run iOS 12 for the first time, with a big prompt to turn on automatic updates:
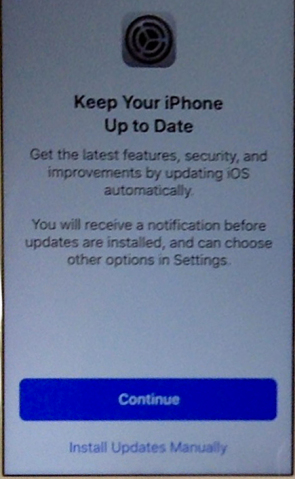
Users who have this option enabled will get a warning from their phone that a new update will install, as well as a notification after-the-fact that they’ve been brought up to date.

Credential AutoFill supports third-party password managers
Many of the updates in iOS 12 seem to indicate that Apple wants to make it easier for everyone to manage their passwords, even if they don’t want to exclusively use Apple products. Of course, their preference is that iOS users stick with Safari, so the bulk of these updates will only work when it is being used as the web browser.
That said, third-party password managers will be able to AutoFill credentials into apps and Safari via an API. So if you’re visiting a website and you know your (non-Apple) password manager of choice has the login credentials stored, you no longer would need to do a somewhat annoying switch-back-and-forth-cut-and-paste dance to grab the username and password between your app or browser and your password manager. Instead, the password manager will work much like it does on your computer-based browser, where Safari will show an option to auto-populate your credentials from your password manager right in the QuickBar.
This credential AutoFill feature will only work if your third-party password manager (like 1Password or LastPass) supports Apple’s password manager API for iOS 12.
Right now as we’re in beta, password manager makers are still working on getting their side of things up and running, but 1Password and LastPass have both said they will support AutoFill when iOS 12 officially launches. (KeePass users, there have already been several requests for iOS AutoFill support on several KeePass mobile apps, so keep an eye out for this feature.) Previously, iOS users who wanted something like this would have had to install an extension or opt to use iCloud keychain.
For iOS users who are loyal to both non-Apple password managers and non-Apple browsers (like Firefox or Chrome), at this point it still looks like it’s up to them to download mobile extensions or add-ons if they want a similar experience.
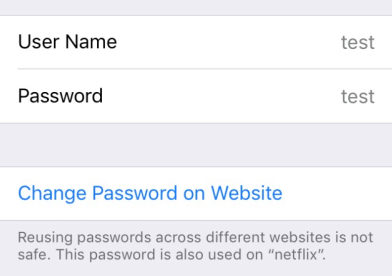
Making it easier to replace reused passwords for strong, unique passwords
In addition to helping users adopt stronger, unique passwords by making it easier for them to use a password manager, iOS 12 will also give users a friendly poke if they’re re-using passwords across sites.
iOS 12 will also go a step further and generate a unique, complex password to replace the old one, and offer to store that new password in the iCloud Keychain.
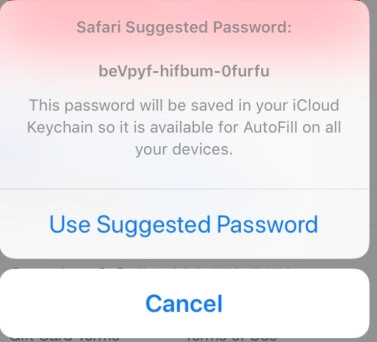
This is functionality that many third-party password managers offer as well, but having this built-in will allow for better password hygiene in users who rely on Apple-native products. A change like this might not have the pizazz that impresses most iOS users, but these features will make it easier to have better, more unique passwords – all without much effort or thought on the side of the user.
Making SMS 2FA a little less annoying
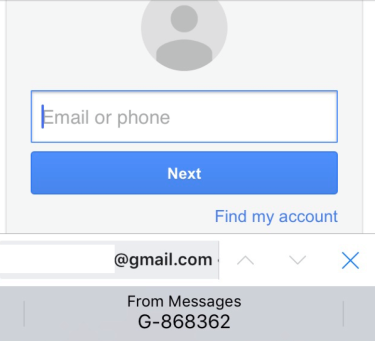
While a larger discussion (justifiably) continues around the security of SMS 2FA, and how to get more people to adopt token-based 2FA instead, the reality is while it may not be the best solution for 2FA, it’s often the only choice available. In the pursuit of not letting perfect be the enemy of good, there’s an update in iOS 12 that will make it even easier to grab the 2FA code texted to you.
The code will now be easy to highlight within the Messages view, and the code will also appear as an AutoFill text field within the browser, so users won’t have to click back and forth between apps to get the code they need.
If you’re thinking this is all small stuff, consider that the little changes do add up for a big impact. For years IT and security pros have been wheedling, begging, pleading, forcing users to use strong, unique passwords. We’ve written about why unique passwords matter, and how it can be so simple to do when you use a password manager.
But getting on board with this kind of thing requires considerable time and effort (researching a password manager, downloading it, setting it up), as well as, well… giving a hoot about any of this to begin with.
Any measures that reduce the friction in adapting better security is a good thing. Usability and security should not be enemies. We may have our work cut out when it comes to making security something that “the average user” cares about, but that’s why I applaud any measures that make better security something the average user can do.
So what say you? Will you be installing iOS 12 in beta and giving this a test drive? Here’s hoping all third-party password managers make the deadline so their extensions are ready when iOS 12 launches.
In the meantime, I’m taking advantage of a non-security iOS 12 update: a reminder to call my mother!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/qCPm7WAV_Wo/











