The Australian government wants to force companies to help it get at suspected criminals’ data. If they can’t, it would jail people for up to a decade if they refuse to unlock their phones.
The country’s Assistance and Access Bill, introduced this week for public consultation, strengthens the penalties for people who refuse to unlock their phones for the police. Under Australia’s existing Crimes Act, judges could jail a person for two years for not handing over their data. The proposed Bill extends that to up to ten years, arguing that the existing penalty wasn’t strong enough.
The Bill takes a multi-pronged approach to accessing a suspect’s data by co-opting third parties to help the authorities. New rules apply to “communication service providers”, which is a definition with a broad scope. It covers not only telcos, but also device vendors and application publishers, as long as they have “a nexus to Australia”.
These companies would be subject to two kinds of government order that would compel them to help retrieve a suspect’s information.
The first of these is a ‘technical assistance notice’ that requires telcos to hand over any decryption keys they hold. This notice would help the government in end-to-end encryption cases where the target lets a service provider hold their own encryption keys.
But what if the suspect stores the keys themselves? In that case, the government would pull out the big guns with a second kind of order called a technical capability notice. It forces communications providers to build new capabilities that would help the government access a target’s information where possible.
In short, the government asks companies whether they can access the data. If they can’t, then the second order asks them to figure out a way. Here’s a flowchart explaining how it works.
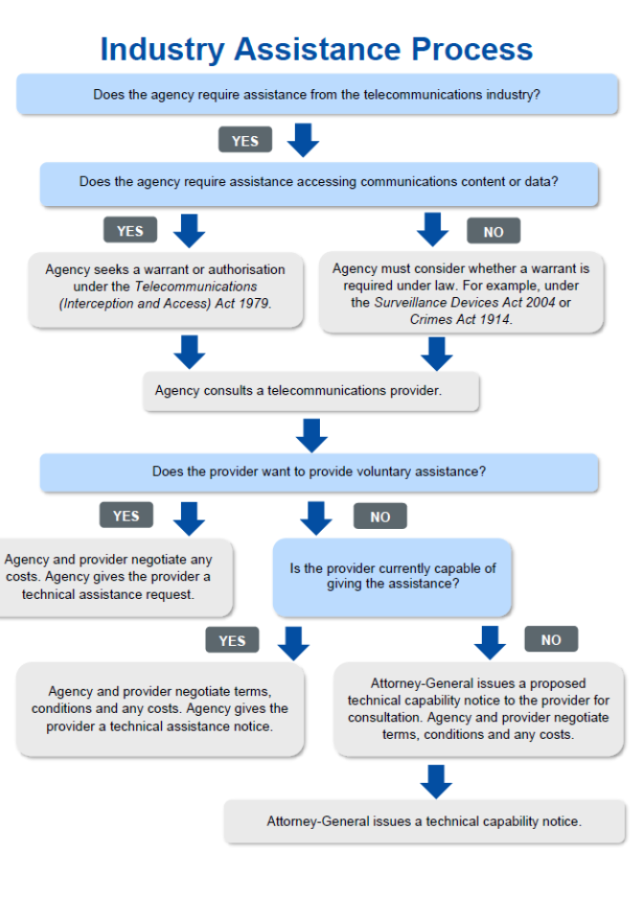
No backdoors
The government’s explanatory note says that the Bill could force a manufacturer to hand over detailed specs of a device, install government software on it, help agencies develop their own “systems and capabilities”, and notify agencies of major changes to their systems. In short, it would force communications providers to work extensively with the government to gain access to a target’s data where it was in their power to do so, and it would also compel them to keep all of this secret.
What if the communications provider doesn’t want to help? Then they could face penalties from the government, or “injunctions or enforceable undertakings”.
There are a few things that the Bill doesn’t allow. The government can’t force a company to build weaknesses into a product, or stop it from fixing those that it finds. That rules out encryption backdoors, then. Neither can it access information without a warrant.
However, the proposed legislation also creates a new class of access warrant that lets police officers get evidence from devices in secret before the device encrypts it, including intercepting communications and using other computers to access the data. It also amends existing search and seizure warrants, allowing the cops to access data remotely, including online accounts.
The backdoor war
In proposing this legislation, Australia joins a complex and heated debate about the role of encryption in the tech business. The Bill effectively rules out the inclusion of encryption backdoors, but seeks help from as many people as possible to get at the data, using a variety of loosely-defined methods.
Many services such as Snapchat don’t use end-to-end encryption, meaning that a government could use legislation like this to make it hand over a user’s encryption keys.
In this sense, it mirrors the UK’s Investigatory Powers Act, which asks telecommunications companies to remove electronic protections where possible. It also parrots FBI officials, who have said that they aren’t asking for encryption backdoors but that they do want vendors and service providers to break it where necessary.
The tensions over forced decryption have played out across the globe. In the US, Apple has tussled with the FBI in court over its unwillingness to help the feds break into its devices.
On the other side of the world, Russia blocked privacy-focused messaging company Telegram after it failed to hand over encryption keys that protect its cloud-based chats. However, Telegram also offers ‘secret chats’ for the extra-paranoid, which support end-to-end encryption, and the company couldn’t hand over those keys even if it wanted to.
There are two sides to the encryption argument. Security advocates including Sophos argue against the use of encryption backdoors, warning that criminals could discover and use them. Privacy advocates like Telegram founder Pavel Durov don’t like backdoors or forced decryption because they don’t want the authorities overstepping their bounds.
On the other hand, the authorities want to get at encrypted data somehow because they want it to stop criminals such as child abusers and terrorists. The latter have been known to use the Telegram service to plan their attacks.
The flurry of legislation around the world addressing this issue is a product of that complex debate. It also highlights the disparity between the legal system, which moves at a snail’s pace, and the technology world, which moves at the speed of light. One thing is for sure – it is a debate that is far from over yet.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/DRIAaE-M4k4/







