How to Structure an Enterprise-Wide Threat Intelligence Strategy
The ever-expanding range and diversity of cyber threats make it difficult for organizations to prioritize their offensive and defensive strategies against attackers. From malware, ransomware, and other attacks coming from the outside, to insider threats and system vulnerabilities from within, today’s expanded attack surfaces cut across the whole enterprise landscape — and that means an enterprise’s threat intelligence strategy must address the entire IT ecosystem.
To be effective, threat intelligence must be proactive, comprehensive, and done in a way that doesn’t inadvertently create more risk. Unfortunately, as a recent Ponemon survey illustrates, most organizations fall short of this goal — tripped up by a range of challenges, including a lack of expertise and overwhelming volumes of data. Improved threat intelligence comes from improving the strategy, techniques, and tools employed by enterprises to probe their networks for weakness and shore up defenses and resiliency.
A “Dirty Internet” of Threats and Vulnerabilities
The digital universe is vast, but it’s also “dirty” in the sense of data seeping across perimeters and network boundaries. This “digital exhaust” — evidence of visits, searches, purchases, and other behaviors that users leave behind on the Internet — is growing quickly and is grist for hackers looking to penetrate systems and databases.
Unfortunately, one of the most valuable forms of digital exhaust comes as a by-product of poorly designed threat intelligence. Too often, threat intelligence involves tools and processes that, while designed to monitor the perimeter and internal systems for threats, unwittingly leave behind artifacts of that troubleshooting activity that malicious actors can ultimately use against the organization.
This “fly on the wall” process of observation could even uncover specifics about who is conducting the threat intelligence and what devices they’re using. Adding to the challenge, today’s threat actors are sophisticated enough that firewalls, VPNs, proxy servers, and other traditional secure access solutions are too weak to stop them.
What’s needed is a new approach to operating on the Internet that makes use of managed attribution techniques, including data obfuscation, identity and location masking, and multiple levels of encryption and authentication to reduce and virtually eliminate the attack surface. In other words, an ideal threat intelligence strategy would not only protect data from breaches but also protect data in the event of a breach. Both goals can be achieved.
Anonymity and Managed Attribution
Anonymity is an important component. This is where technology is used to conceal your identity, location, and details about the device you are using as you conduct threat intelligence. Managed attribution takes things a step further, not only hiding your identity and location, but actually making it appear as if you are someone else operating from somewhere else — a soccer parent in Manitoba, say, instead of a systems analyst in Arlington, Virginia.
Further, organizations need to manage both the technical and personal side of user identities. Technical attribution might involve a virtual desktop that’s clean and separate from the data on an actual device; there are even systems that frequently and randomly swap IP addresses at the point of presence. Personal attribution, meanwhile, involves multiple profiles that can be swapped out as quickly and easily as signing in and out of the platform. Suddenly, the soccer parent in Manitoba becomes a street merchant in Madrid.
Securing Data for a Secure Future
Ultimately, the entire network architecture should be cloaked from the view of threat actors looking to seize access and advantage. This involves obfuscating network operations through a cloud of encryption and IP hopping capabilities that mask user and organizational data through a series of complex pathways, directory nodes, and networking hops that scramble the meaning and context around data and its users.
While the attack surface can’t be eliminated entirely, obfuscation can turn that surface into a meaningless or unappealing target to potential threat actors. It’s even possible to obfuscate entire pieces of infrastructure — email systems, application servers, and storage facilities — and this can all be designed and implemented in the cloud.
The innovation around threat intelligence is constant, and for good reason. It’s not just that organizations need to protect assets today; they also need to be prepared (as much as possible) for tomorrow’s unknown and unknowable threats. Effective threat intelligence can also help organizations meet regulations such as the EU’s General Data Protection Regulation as well as existing standards that require them to employ technical and organizational measures that ensure an appropriate level of security.
For all these reasons, improved threat intelligence can and should be a priority for any organization or government agency. The right strategies, tools, and partners can lead to a higher level of security that keeps both cyber-threat teams and organizational data safe and secure from evolving and ever-growing cyber threats.
Related Content:
- 6 Steps for Sharing Threat Intelligence
- 4 Basic Principles to Help Keep Hackers Out
- Why Sharing Intelligence Makes Everyone Safer
- Is Threat Intelligence Garbage?

Learn from the industry’s most knowledgeable CISOs and IT security experts in a setting that is conducive to interaction and conversation. Register before July 27 and save $700! Click for more info.
Tom Badders is the Senior Product Manager for Secure Mobility Products and Services at Telos Corporation, a leading provider of continuous security solutions and services for the world’s most security-conscious agencies and organizations. Leveraging over 40 years of … View Full Bio

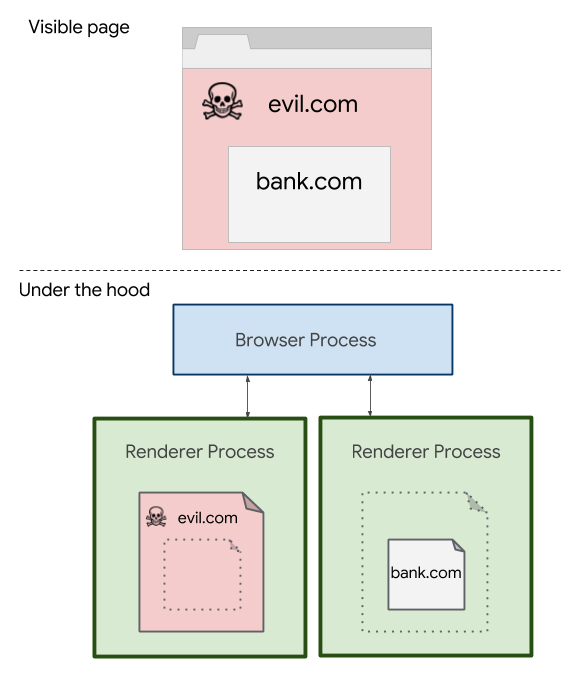





![Site Isolation in Chrome diagram [source: Google blog post] Site Isolation in Chrome diagram](https://stewilliams.com/wp-content/plugins/rss-poster/cache/c6035_site_isolation_chrome.jpg)