Bitcoin user loses $10K to typosquatters
Thanks to András Mendik of SophosLabs in Sydney for the technical background to (and, indeed, the idea for) this article.
 Last week, SophosLabs alerted us to a Bitcoin phish orchestrated by email.
Last week, SophosLabs alerted us to a Bitcoin phish orchestrated by email.
This week, they’ve pointed out a Bitcoin phish that relies on typosquatting.
Typosquatting is where you register a domain that is close to the name of someone else’s site – SOHPOS, for example, instead of SOPHOS – and wait for users to stumble into your path because of minor typing mistakes.
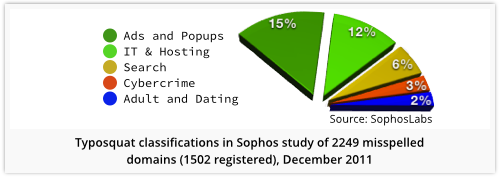
We conducted a systematic study of typosquatting just over two years ago, by deliberately making every possible one-character typo in six domain names: Facebook, Google, Twitter, Microsoft, Apple and Sophos.
To be more precise, we programmed a bunch of computers to automate the work for us, because there are 2249 different ways of misspelling the names above. (Omit one letter, add in one letter at each possible point, or type one of the existing letters wrongly.)
Two-thirds (1502) of the off-by-one domain names were registered, sucking down a whopping 14,495 different URLs when we visited them.
While a few typos made reasonable alternatives (Racebook for Facebook, for example), many were there to fool you.
The outright imposters presented content that you would readily associate with the real site – brand deception, in other words – to convince you that you’d reached the right place.
Indeed, according to SophosLabs classification data, there was a fair amount of downright dangerous jiggery-pokery going on amongst these typosquatters, including 3% of them classified outright as “cybercrime”:
So we were sad, but hardly surprised, to hear the story of a chap who claims he lost a fair few Bitcoins – BTC16.50, worth close to $10,000 at current prices – by hitting one extra key.
Instead of typing B-L-O-C-K-C-H-A-I-N, he managed to hit an extra -O- (diagonally above -K-) to produce B-L-O-C-K-O-C-H-A-I-N.
O, the irony! If he’d explicitly prefixed his URL with https:// then the fake site he ended up on wouldn’t have responded at all, and he’d have been safe.
But he didn’t do that, relying instead on being redirected to the site’s HTTPS pages when the time came to login.
Here’s a Spot the Difference of the login screen he saw after his key-fumble, compared to the real thing:
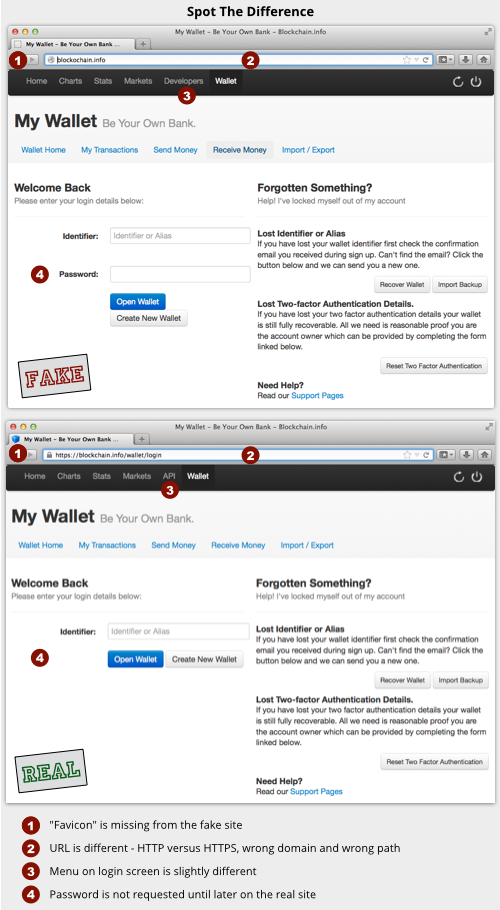
As with last week’s email phishing case, most of the differences are visually inconsequential (and could anyway have been avoided by the crooks if they had taken slightly more care), but one important difference stands out clearly: HTTP where you want to see HTTPS.
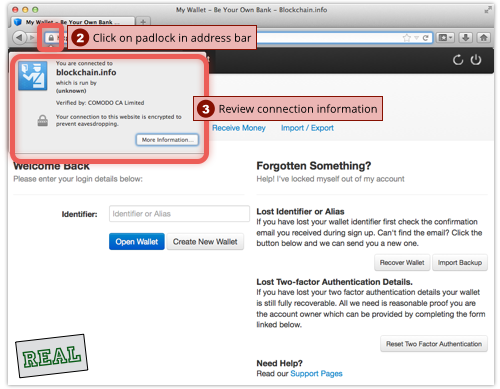
As Chester Wisniewski explained in last week’s Sophos Security Chet Chat podcast (the relevant section starts at 8’51” in the audio below), the absence of HTTPS where you would expect it is an instant giveway, but the mere presence of a padlock is not enough on its own .
The crooks almost certainly can’t get their hands on the genuine cryptographic keys for the blockchain.info domain, so it would be toweringly difficult (if not actually impossible) for them to mock up an entirely convincing version of their target’s secure site.
But they could, probably not without too much difficulty, get an HTTPS certificate for their own imposter site.
That would allow them to present you with the next best thing, visually speaking: an HTTPS URL and a padlock in the address bar, but for the wrong site.
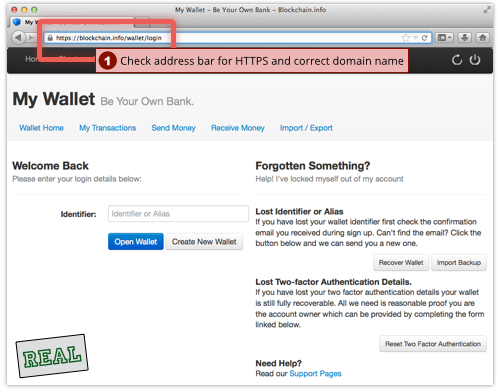
So, let’s review once more how to check not only that a site you expect to be secure really is using HTTPS, but also that it really is the site you expect.
We’ll show you with two popular browsers, Internet Explorer on Windows, and Firefox on the Mac; the procedure with other browsers is very similar.
Here’s how to do it with Firefox, and what our Bitcoin victim would have seen if he were on the real site:
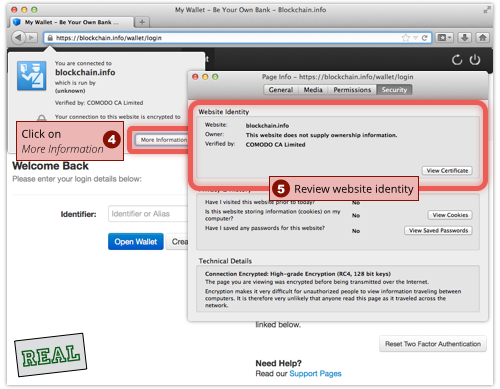
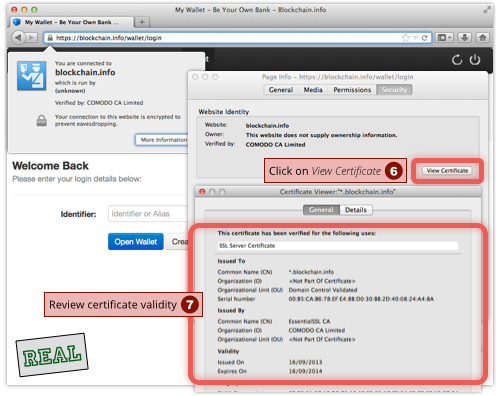
And here’s how to do it if you are using Internet Explorer:
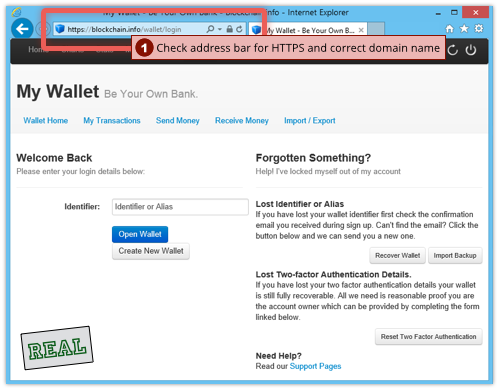

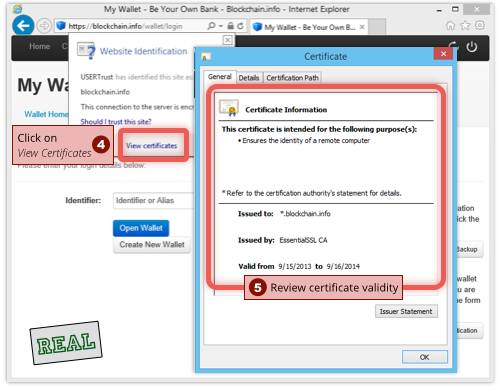
By the way, if you use a password manager to keep track of your passwords (and to pick strong passwords for you), you’ll enjoy some extra protection against imposter websites.
That’s because a typosquat domain like this, or a phishing site like last week’s email-based scam, simply won’t be in your password list.
The password manager won’t even offer to put a password in for you on a bogus site, because it won’t know what password it’s supposed to use!
And whether you use a password manager or not, try saying the following lines of doggerel out aloud to yourself whenever you you see a password prompt in your browser:
Before you log in, don’t forget/To check the site’s certificate.
PS. If you’d like to see a 51-second overview of our Typosquatting report, with a dramatic visual summary of the sort of chicanery you can expect if you get just one character wrong, take a quick look at the following video. (It was made for the Christmas season of 2011.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/ne46fSoBthc/