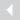Microsoft ‘Campaign Views’ Offers Full Look at Office 365 Attacks
Campaign views, a new capability arriving in public preview for Microsoft’s Office 365 Advanced Threat Protection (ATP), aims to provide greater context around email attack campaigns so organizations can learn how they were targeted and whether their defenses held up.
Attackers behind an email campaign typically use a crafted pattern or template for their messages. Emails are sent in waves, each of which is slightly varied to effectively bypass defenses or trick victims. Identifying this template, which defines the entire campaign, can help security teams pinpoint weaknesses in their defenses and prevent similar attacks in the future.
The problem is, it’s difficult for businesses to spot a comprehensive email attack campaign by looking at individual messages. If an attacker breaks into an organization and someone clicks a bad link, campaign views helps locate vulnerable users so remediation steps can be taken to limit the breach. The tool collects and correlates attacker-specific data, like sending domains, IP addresses, and URLs to help security practitioners adopt a more proactive approach to defense.
Office 365’s ATP protection stack already aims to block zero-day phishing and malware attacks with a layered defense system made up of tools to address protection at the perimeter, sender intelligence, content filtering, and post-delivery protection. These capabilities are meant to help pinpoint threats during mail flow and after email delivery. Campaign views takes a step back to provide more of a bird’s-eye view of a particular attack.
“Because these are brand-new attacks and our goal is to protect even the first user, these defenses operate even before campaign views comes together,” says Girish Chander, group program manager with Office 365 security. “The focus of campaign views is to layer on top of these protections to help security teams get a glimpse of the entire campaign that hit them.”
This tool is a more advanced way to cluster emails in a specific campaign based on the similarity of email template, payload, and other traits, even as factors like sending IP and sending address change. Its goal is to increase the effectiveness of SOC teams who were trying to identify campaigns within the organization by searching for all emails containing a specific attribute (sender, URL, etc.), which Chander says is a less effective technique. Campaign views leverages intelligence from the Microsoft intelligence security graph to better identify attacks.
In a single view, security teams can learn details about an entire campaign, including when it started, the sending pattern and timeline, how long it has been ongoing, and how many people fell victim to the attack. Admins can view the list of IP addresses and senders involved with orchestrating the attack and assess which emails were blocked, delivered to junk or quarantine, or delivered to the employee’s inbox. In addition to seeing all URLs used in the attack, security teams using Office 365 ATP Threat Explorer can learn if any users clicked on the phishing link.
(Image: Microsoft)
By seeing who fell for an attack and how, admins can learn who needs their credentials reset and who should be enabling multifactor authentication. Further, a broader view of a campaign can inform admins of poor security configurations that attackers are exploiting to gain access. A view of indicators of compromise gives admins the data they need to investigate other messages that exhibit the same characteristics and take remediation actions.
“It is, unfortunately, not uncommon to see poor configurations in organizations, such as ‘tenant allows’ of a broad swatch of sending domains or IP,” says Chander. “These tenant allows override any ATP catch and deliver the email to the inbox.” Because a lot of these flawed configurations have existed for some time, people often don’t know about them.
“However, what we’re finding is that when customers see the scale of the impact of these poor configurations, it becomes more contextual and urgent to deal with them,” he adds.
In reviewing an attack campaign, security teams should prioritize learning who was compromised and ensuring they’re protected to prevent the attack from spreading. In some cases, clicks were blocked by Safe Links, but the block was overridden by the victim. Microsoft notes there’s a high chance victims may have fallen for an attack hosted on a malicious site, either by handing over credentials to the fraudulent site or being hit with drive-by malware.
Microsoft reports early preview users of campaign views have identified multiple configuration flaws. One discovered a domain allow list was exploited by an attacker; as a result, 34% of phishing messages detected by ATP were rescued and then delivered to employee inboxes. Customers also report the tool make it easier to explain threats to the CISO and business peers.
Related Content:
- 10 Security ‘Chestnuts’ We Should Roast Over the Open Fire
- The Human Factor: 5 Reasons Why Cybersecurity Is a People Problem
- Password-Cracking Teams Up in CrackQ Release
- Success Enablers or Silent Killers?
 Check out The Edge, Dark Reading’s new section for features, threat data, and in-depth perspectives. Today’s top story: “Criminals Hide Fraud Behind the Green Lock Icon.”
Check out The Edge, Dark Reading’s new section for features, threat data, and in-depth perspectives. Today’s top story: “Criminals Hide Fraud Behind the Green Lock Icon.”
Kelly Sheridan is the Staff Editor at Dark Reading, where she focuses on cybersecurity news and analysis. She is a business technology journalist who previously reported for InformationWeek, where she covered Microsoft, and Insurance Technology, where she covered financial … View Full Bio
 Check out
Check out 

 Check out
Check out  Check out
Check out