Critical DoS messaging flaw fixed in December Android update
For anyone lucky enough to get them, Android’s December 2019 updates arrived this week, patching a small list of system and Qualcomm flaws across the operating system’s two patch levels.
In Google’s estimation, at the top of the urgent list on the 2019-12-01 patch level (see below for explanation) is CVE-2019-2232, a critical flaw affecting Android versions 8.0, 8.1, 9, and 10.
This, Google said, could allow an attacker to cause a “permanent” denial of service by sending users a specially crafted message. The company doesn’t qualify what it means by this alarming description, and there is no indication it’s being exploited, but users won’t want to find out the hard way.
Overall, the update fixes 15 CVEs (2019-12-01) and 5 CVEs (2019-12-05), with another 22 patching Qualcomm components.
Patch level 2019-12-01
This level affects most third-party handsets – those not made by Google. If the patch level on your phone uses the ‘01’ date beside the month, that means you’re getting the security updates up to and including that date, which is to say all the essential ones.
Three fixes on this level are listed as critical, but for two of these – CVE-2019-2222 and CVE-2019-2223 – the rating only applies for versions 8.0, 8.1, and 9. On Android 10, that drops to ‘high’. That could be because 10 has extra mitigations or because it uses Project Mainline through which some critical updates are applied more quickly via Google Play.
One recently disclosed flaw that was quietly fixed some time ago via the Play store is the hijacking flaw affecting Google’s camera app.
Patch level 2019-12-05
If your device specifies this date, you’re getting everything in 2019-12-01 plus the additional five CVEs and the Qualcomm stuff. However, arguably, the real difference between these two levels isn’t the updates on offer, but when they become available. For 05, that should be from this week – for 01, it could be weeks or months.
You can find out by checking Settings About phone Android security patch level.
On Android 9, this changes to Settings System Advanced System updates.
Note that individual manufacturers add their own updates to Google’s. For example, for Samsung, this month’s crop is outlined on its security update site.
Having different patch levels plus separate Qualcomm and vendor patches is confusing for users. That’s one reason why Google recently started looking into overhauling how Android uses the Linux kernel that sits at its heart, to make things simpler, easier and cheaper for all concerned.
Goodbye Pixels
If you own a 2016 Google Pixel or Pixel XL, this month’s update will be the final one that those devices receive, extending their patched life by a month longer than was originally promised.
For more on the support period for other Google devices, see the table on this support page.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Z6rqHUlLVrM/
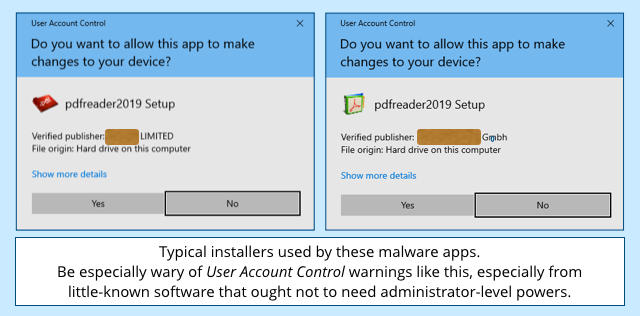
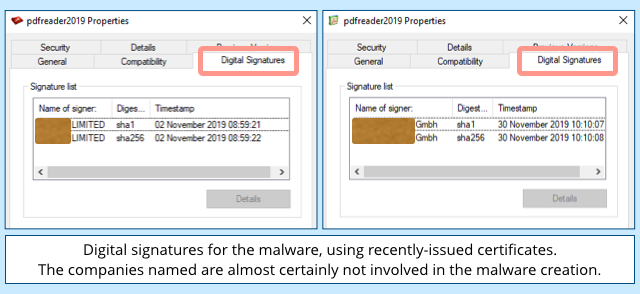

 Check out
Check out  Check out
Check out