If you’ve been following trendy news sites over the past week, you’ve probably heard of a new – or at least a newly popular – app called Gradient.
Gradient pitches itself as “the next big thing in the world of mobile photo editing”, heavily promoting a new feature that supposedly lets you:
Find what famous person do [sic] you look like with our brand new AI feature! Our precise technology powered by artificial intelligence will amaze you with an accurate result. Don’t forget to share it with your friends as a post or a story!
Despite the “photo editor” category being a crowded field on both Google Play and in Apple’s App Store. The company that produces the app, Ticket to the Moon, Inc. (TttM) has hit the publicity jackpot in the last few days, splashing out on celebrity advertising on social media sites such as Instagram.
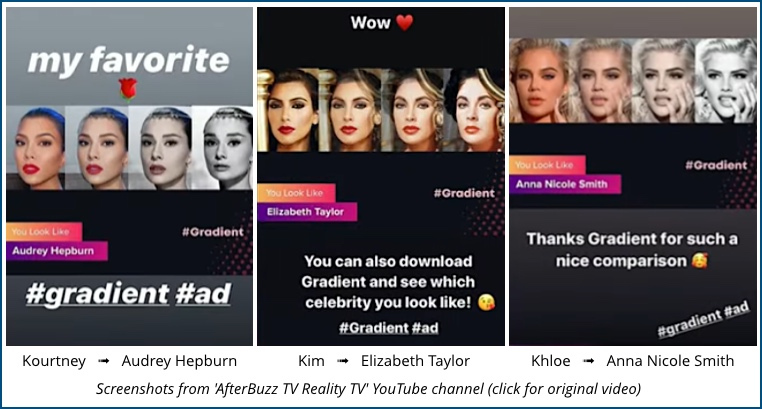
Apparently, three of the Kardashian sisters have recently posted paid endorsements for the Gradient’s You Look Like… feature, with Kourtney claiming the app matched her to Audrey Hepburn, Kim looking like Elizabeth Taylor, and Khloe coming up as the doppelgänger of the late Anna Nicole Smith.
We tried You Look Like… ourselves, and the results were rather less accurate than we expected from “precise technology powered by artificial intelligence.”
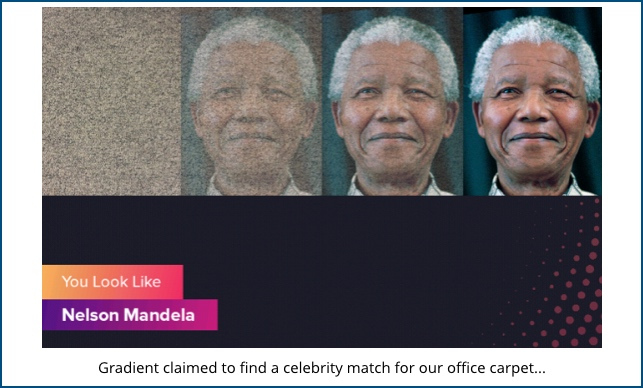
For example, we fed in a picture of the office carpet…
…and were confidently told that it looked liked Nelson Mandela.
If you don’t like the first celebrity you get, there’s a ‘next’ button that lets you try again.
We fed the Sophos Mobile Security shield icon into the Who’s Your Twin feature and were twinned variously with actress Vanessa Hudgens and psychonaut Aldous Huxley, which seemed a fascinatingly unlikely pair of matches.
The following day, Gradient paired up exactly the same shield with famous footballer David Beckham and US founding father James Madison.
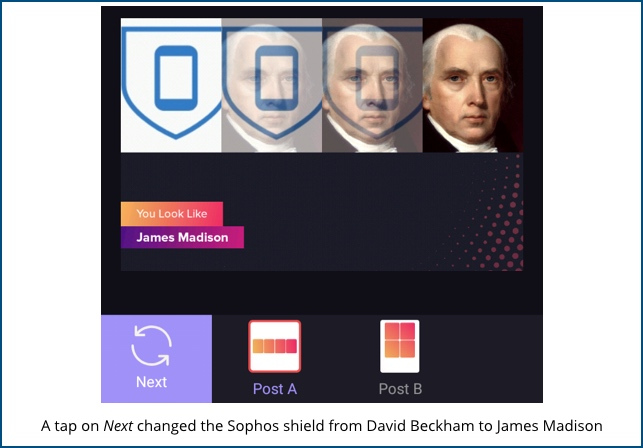
Harmless fun?
In short, the app looks more like a bit of passingly harmless fun than a serious facial recognition system…
…and that has got people wondering why an unknown company would spend a massive amount of marketing money – perhaps millions of dollars – on an app that feels unlikely to be a lasting and commercially viable phenomenon.
The burning question online, therefore, has been, “Is the app safe?”
If you remember the FaceApp privacy scare back in June 2019 – that was the app that claimed to show you what you’d look like in the future by applying an ageing algorithm – then you won’t be surprised to hear people voicing the same concerns over Gradient.
In particular, people are wondering, “What on earth are they going to do with the pictures that get uploaded?”
Like FaceApp before it, Gradient has terms of use stating [2019-10-28T14:50Z] that:
You hereby grant to Gradient a non-exclusive, fully paid and royalty-free, transferable, sub-licensable, worldwide license to use Your Content to provide our Service, subject to the Privacy Policy.
But, as we pointed out when FaceApp was all the rage, this sort of licence is neither unusual nor surprising, and many image processing and social media sites have similar terms and conditions.
A much bigger concern over Gradient, in our opinion, is the fact that although it’s technically a free app, it could end up costing you more than you thought.
The app’s Google Play Store page claims that the monthly fee is just $3.99, with $19.99 buying you a full year:
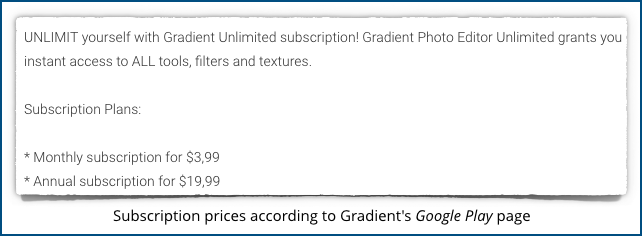
But the app itself says otherwise.
The in-app signup offered us a weekly subscription, with no free trial period, at $4.99 a week, or a monthly subscription at $19.99, which is the only way to get your three free days:

In fact, if you don’t cancel your subscription “at least 24 hours before the end of current period” [sic], then you will automatically be billed for the next period.
In other words, if you don’t go back into your Google Play or your Apple App Store account within 48 hours of signing up – which effectively makes the free trial period just two days rather than three – then you are going to be $20 out of pocket.
For this, and for any other subscription-based app you may be tempted by, take careful note of the fact that the subscription, and the recurring fees, is handled by your Google or Apple account, not the app itself, so simply uninstalling it will not cancel your subscription and will not stop you being billed every week or month.
We’ve written about apps with short trial periods and high price tags before, dubbing them “fleeceware” because of the astonishing prices they demand, and because trying-but-deleting the app doesn’t cancel the trial.
The developers of Gradient would probably argue that, unlike the fleeceware apps we highlighted back in September 2019, the Gradient app doesn’t bill you $100 or more in one go, and isn’t quite as elementary as some of the apps we described last time, such as a basic QR code reader costing €104.99.
Google and Apple seem to agree, because both companies are happy to host apps like Gradient – and are happy to take their cut of the subscription fee that these apps charge.
So, for now at least, our advice is old-fashioned caveat emptor, better known as “buyer beware”.
While we’re about it, we also urge you to do the right thing by your friends when it comes to apps like FaceApp and Gradient – abide by the terms and conditions that require you to have the right to upload images in the first place.
It’s tempting, and it feels like innocent fun, to upload photos of people you know in the hope of getting amusing results that you can share with your social media circle.
Please don’t do it – let your friends choose for themselves what to share, and where to share it.
What to do?
When it comes to in-app purchases:
- Read the small print. Be certain that you know what you are signing up for, when billing starts, and how to unsubscribe from recurring charges.
- Don’t assume that uninstalling an app ends your contract with the vendor. Check your Google or Apple account, and unsubscribe from there.
- Don’t mistake paid endorsements for product reviews! Sure, the Kardashians love the Gradient app – but, unlike you, they’re being paid to use it.
- If in doubt, leave it out. Don’t install an new app just because everyone else is using it – make sure there’s something you
Perhaps it would be better, if a little less lucrative, for online app markets like Google Play and the App Store to require that apps with “free trials” should require a opt-in subscription confirmation at the end of the trial period?
That way, free trials really would be free, and you’d get to choose whether you actually wanted to buy the app after you’d tried it, rather than before.
What do you think? Have your say in the comments below…
LEARN MORE ABOUT GRADIENT – WATCH NAKED SECURITY LIVE NOW
(Watch directly on YouTube if the video won’t play here.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/cKna-7UcJBE/