Symantec bundles CEO out the door, parachutes in chairman
Analysis Software jack-of-all-trades Symantec has replaced dapper CEO Enrique Salem with board chairman Steve Bennett. Salem, we think, got the bullet for failing to conquer the mobile security market, his handling of the Backup Exec outrage, and his humdrum financial performance.
The company’s profit dipped this quarter, the first financial period of 2013, to $172m, down 9.5 per cent compared with the same three months a year ago. This figure is well down from $559m recorded in the previous quarter, which was bulked up by a payment from Huawei when the telco equipment giant bought out the Huawei-Symantec joint venture.
Revenues in Q1 2013 were up just 1 per cent year-on-year to $1.668bn, the seventh quarter in a row of $1.6 to $1.7bn sales. Salem had been tasked with lifting Symantec out of its revenue doldrums, relatively speaking.
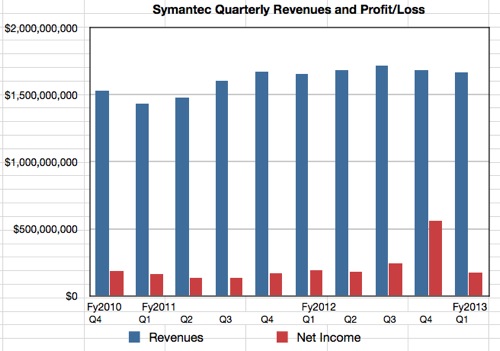
Symantec’s figures to Q1 FY2013
The fact that Symantec’s board chairman is taking over indicates that Salem has gone with some haste: there has been no succession plan for this situation, that much is clear. Bennett said in a statement:
Enrique Salem has been a significant contributor during his 19 years’ associated with Symantec, including the last three years as CEO. While progress has been made over the last three years in many areas, it was the board’s judgment that it was in the best interests of Symantec to make a change in the CEO.

Enrique Salem
Bennett vented the board’s frustration thus: “My view is that Symantec’s assets are strong and yet the company is under-performing against the opportunity. I’m looking forward to working with the team to build upon the significant assets in place to help Symantec accelerate value creation for all of its stakeholders.”
Symantec has a new lead independent director who can make comments on the business inappropriate for a chairman or CEO. That person is Dan Schulman, who said: “The board’s decision to make a leadership change was not based on any particular event or impropriety but was instead made after ongoing consideration and a deliberative process.” Translation: Enrique, we thought long and hard, and we reckon it’s time Symantec backed up to another chief exec – just our little joke, there.
Being told Salem made a significant contribution in the circumstances but not thanked speaks volumes.

Steve Bennett
Bennett joined Symantec’s board in February 2010 after he was president and CEO of Intuit for eight years. He looks like a permanent rather than a stopgap CEO for Symantec, and said he viewed the job as a three or five-year task, followed preferably by an internal replacement. He said: “We are making progress on many fronts, but we believe we can further accelerate the company’s value to employees, customers, partners and shareholders.” Not good enough, in other words.
Symantec’s sales in the consumer segment have eroded under competition from increasingly capable freebie gear from the likes of AVG, Avast and Microsoft.
In addition the firm failed to switch away from its traditional software renewal business or set the world alight in the storage and system management market.
Less tangibly, Salem came across as a grey bureaucrat, hopelessly outgunned in the battle for big ideas when put against more charismatic figures such as Eugene Kaspersky, and seemingly without the ability to fire up Symantec’s sales team or channels.
As chief operating officer, Salem also earned the ire of its distribution network by dissing US resellers behind closed doors.
Chief financial officer James Beer said today: “We saw strength in endpoint protection, consumer security, authentication services, data loss prevention, and backup appliances.”
Here’s the company’s latest results break down:
- Consumer products contributed $521m, 31 per cent of total revenues, and decreased 1 per cent year-on-year.
- Security and Compliance contributed $501m, 30 per cent of revenues, and increased 7 per cent annually.
- Storage and Server Management contributed $584m, 35 per cent of revenues, and decreased 2 per cent annually.
- Services contributed $62m, 4 per cent of revenues, and declined 2 per cent annually.
Revenues from the Clearwell and Live Office acquisitions generated $24m.
In the earnings call Bennett admitted that the Backup Exec product faced challenges – a major update upset a lot of people. He said Symantec will work to get it back on track.
Bennett will undertake a 90 to 120-day tour of the company to chat to employees. He’ll probably make some short-term decisions but couldn’t say or wouldn’t say what they are right now. He seemed particularly keen on a Symantec eCommerce engine, though. Positioning Symantec as the mobile security market leader is a priority for him.
He also said Symantec generates more cash than it needs to run day-to-day and make any desired acquisitions – so he’ll help decide how to return any excess cash to shareholders, implying share re-purchases and/or dividends.
Asked if Symantec should be restructured and possibly broken up he said: “I start with a clean sheet of paper. The most important thing is strategy, and structure follows strategy. … I believe our assets are better than our performance and I need to understand what’s in the way.”
The estimated revenue for the next quarter lies between $1.635bn and $1.665bn, a decline of between 1 to 3 per cent year-on-year – more of the same as it will be too soon for any new Bennett broom to have an effect. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/07/25/symantec_ceo_change/