Sites knocked offline by OpenDNS freeze on Google
Innocent websites were blocked and labelled phishers on Wednesday following an apparent conflict between OpenDNS and Google’s Content Delivery Network (CDN).
OpenDNS – a popular domain name lookup service* – sparked the outage by blocking access to googleapis.com, Google’s treasure trove of useful scripts and apps for web developers. According to reports, a flood of errors hit pages that used Google-hosted jQuery and hundreds of thousands of sites fell over.
Visitors to websites were confronted with a message saying: “Phishing site blocked. Phishing is a fraudulent attempt to get you to provide personal information under false pretenses.”
Other visitors were greeted with a 404 error, aka the dreaded ‘file not found’ message.
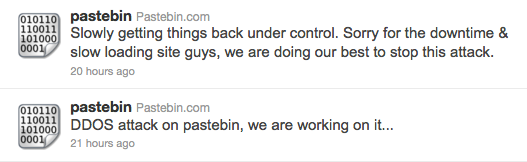
Web design and hosting specialist Brit-Net, whose operations director Mat Bennett captured the phishing error message here, told The Reg the outage lasted for nearly three hours.
As sites and service providers struggled to get back online they employed fallback scripts and re-routed traffic to Microsoft’s rival CDN. Brit-Net was among those updating its code to point to Microsoft.
The cause of the problem with OpenDNS seemed to be the googleapi.com security certificates, according to Bennett and this article advising on working around the problem.
The fact the issue popped up suddenly on Wednesday would suggest that engineers at Google had been fiddling with SSL certificates or made some other change that conflicted with OpenDNS. Google was not available for comment at the time of publication.
Bennett told The Reg that one consequence of the outage for his company is that it would institute a system that sets Google as the default but would switch to Microsoft’s CDN if Google’s system drops out in future to save having to manually tweak web apps. ®
Bootnote
* DNS, for the uninitiated, is the vital system that points browsers at the correct servers when given a human-readable address, such as facebook.com or theregister.co.uk. Although ISPs provide DNS services for their customers, punters can opt to use alternative providers, such as OpenDNS.
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/01/05/google_opendns_clash/