Chinese web giant finds Windows zero-day, stays shtum on specifics
Chinese company Quihoo 360 says it’s found a Windows zero-day in the wild, but because it’s notified Microsoft, it’s not telling anyone else how it works.
In this Weibo post (unless you speak Mandarin you’ll need a translation tool), the company announced an “APT attack” on the unspecified zero-day “on a global scale”.

Windows 10 Spring Creators Update team explains the hold-up: You little BSOD!
It called the vulnerability a “double kill” bug, said it exploits “the latest version of Internet Explorer and applications that use the IE kernel”, and added that it’s being spread in Microsoft Office documents that include a malicious Web page.
If a victim opens the document, the post claims, the malicious code will run in the background to execute the unspecified attack program.
Its only illustration of the attack is in the Chinese-language-annotated image below.
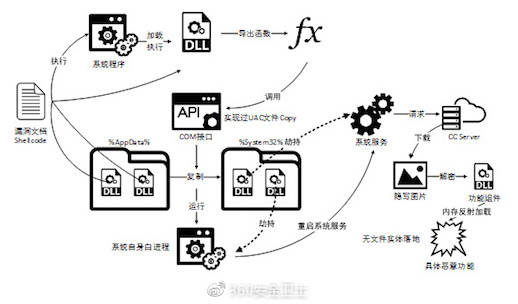
Microsoft would far prefer that users stopped using Internet Explorer and adopted its Edge browser instead. Some users are proving stubborn, though: according to Net Market Share, IE still has a rusted-on 12 per cent of the browser market.
That’s why last week’s Patch Tuesday plugged a serious, if legacy, IE vulnerability: CVE-2014-0322, a remote code execution bug. ®
Sponsored:
Minds Mastering Machines – Call for papers now open
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2018/04/23/quihoo_360_yes_we_found_a_windows_0day_no_you_cant_know_what/