COMPUTER RULES, LAST UPDATED 31 JULY 1988

Remember how IT used to be?
We do, because it’s #SophosRetroWeek, and we want to take you back to remember, too.
Back before BYOD, Android, Facebook, YouTube, Snapchat, WhatsApp, BitCoin, iTunes, the iPad, indeed, before iAnything.
Before mobile phones with six-core CPUs (heck, before mobile phones), before anyone knew what a “gigabyte” was, before USB, before Bluetooth.
Back before search engines, before WWW…way, way back, if you can believe it, even before LOLCATs!
Are you with us?
It wasn’t all roses.
In fact, it wasn’t even roses, because graphics cards were still an optional extra.
OK, so the operating system fitted into a tiny part of a single floppy disk, with room left over for your applications and your data, which was nice.
But the operating system was DOS, which was….well, it fitted onto a single floppy disk, that’s all we’re saying.
And we didn’t have Acceptable Use Policies or Computer User Rights And Responsibilities Agreements, which meant a lot less reading.
But we did have computer rules, and they went something like this:
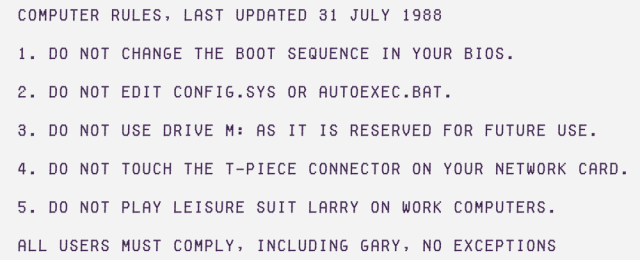
Of course, even though these rules look as capricious today as they probably seemed 27 years ago, they didn’t come about by accident.
Your Sysadmins came up with the rules because their lives were much, much easier – and the network worked way, way, better – as long as you stuck to them.
All of you, even Gary.
So please join us today in saying to all your tireless computer support crew, “Thanks IT, and Happy Sysadmin Day.”
PS. Don’t miss our #SysAdminDay guide to understanding what Sysadmins hear when you speak…
In case you’re wondering, here’s why the rules made sense, and weren’t just Sysadmins saying ‘DO NOT’:
1. These days, you can usually press a key like Esc to bring up a boot device menu. If you don’t press Esc, your computer boots automatically from its internal disk. Back then, you couldn’t do that. Your PC would boot from A: (floppy) by default, and every time you left a disk in there overnight, you ran the risk of infecting yourself with a boot sector virus the next morning. Sysadmins used to go round and change everybody’s BIOS settings, laboriously, by hand, so that the default boot disk was C: (hard disk). This reduced the incidence of boot viruses tremendously and saved them hours of hassle. Until you went fiddling, and changed the boot sequence back. Perhaps so you could boot off some game disk you had brought from home. Thus, Rule 1. (And see Rule 5.)
2. CONFIG.SYS and AUTOEXEC.BAT configured DOS when your PC booted up. With just 640KB of memory, every utility you added or tweak you made ran the risk of eating away at the capacity of your PC and breaking something that your Sysadmins would have to fix. Also, DOS only really supported one application at a time, unless you loaded special TSR (terminate-and-stay-resident) programs via AUTOEXEC.BAT. These often crashed each other, so Sysadmins stuck to tested combinations that made your PC work more reliably. Until you went fiddling, and loaded a cool new screensaver that a friend gave you, and the tower of cards collapsed. Thus, Rule 2.
3. Today, everyone has email in their browser, on their desktop and via their phone. In 1988, only go-ahead companies had email (almost always internal – no internet!), but plenty were planning for it. And what better drive letter to reserve for the email application than M:? Unless you’d already decided to use it for a RAMDRIVE, after violating Rule 2 to edit your own configuration. Thus, Rule 3.
4. Nowadays, you probably don’t have a network cable at all. You just use Wi-Fi. If you do have a cable, it’s a simple, double-ended thing. One end clicks into the wall and the other into your computer. Everyone connects “in parallel”, so if you unplug your cable, no-one else is affected. But in 1988, most LANs were 10BASE2, or thin ethernet. All computers on one network segment were connected “in serial” to the same, long piece of coaxial cable that everyone shared. Sysadmins looked after the crimped connections on that cable with loving care so it worked reliably. Until you fiddled with your connector, and cut off everyone from the network at once. Including your Sysadmins. Thus, Rule 4.
5. Leisure Suit Larry in the Land of the Lounge Lizards? You can work out Rule 5 for yourself. (The game is available online via your web browser these days. Just remember: Rule 5 has never been repealed. You know why.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Kk9YcWf3rxA/
