Cryptocurrency phish dials back the fear, cranks up the politeness
Have you heard of a cryptocurrency outfit called Luno?
We hadn’t heard of it until today – there are lots of cryptocoin companies out there, after all – but cybercrooks certainly had.
According to its own website, Luno (it’s the word for moon in the constructed global language Esperanto, in case you’re wondering) has processed cryptocurrency transactions for more than 2,000,000 people in 40 countries since 2013.
And that’s more than enough potential phishing victims to make it worthwhile for crooks to pump out a spama kampanjo (that’s Esperanto for spam campaign, as you probably guessed) to try to trick Luno users into handing over personal data, including their Luno password.
So, rather sadly for Luno, quite a few people are going to be hearing the company name for the first time in the context of an attempted fraud against them.
Like this:
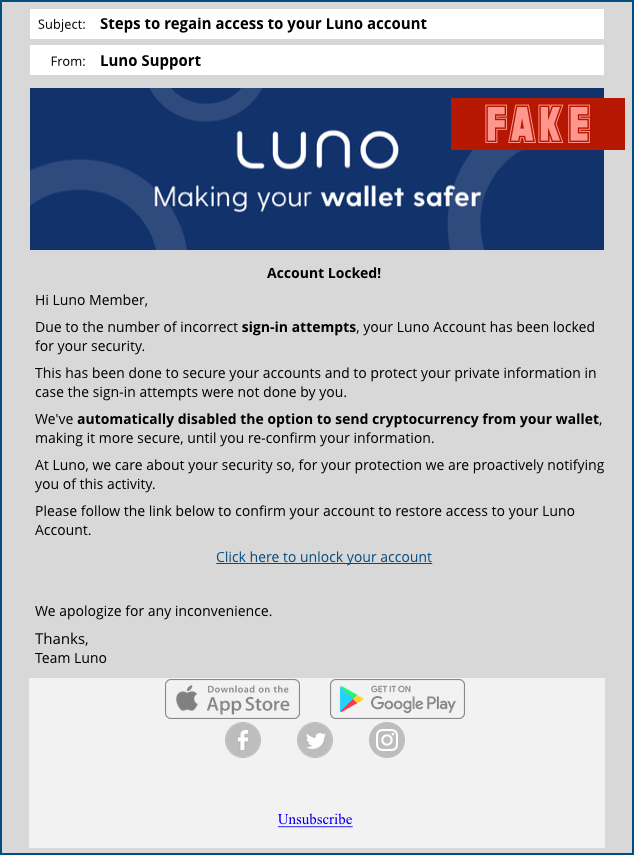
Now, here’s the thing.
A great many spammers are sloppy, and make lots of mistakes in grammar and spelling – with the result that many of us have fallen into the trap of relying on typos and language blunders as the primary “tells” that we’re talking to a crook.
So if you’ve drifted into the habit of watching out for roten speling and gramattic mistakens in order to detect bogus messages, you could easily fall for this one.
It’s not written in quite the sort of English that a fluent, native speaker of the language would use – there’s a certain linguistic clumsiness throughout – but it’s as well-written as many official and supposedly professional documents that we’ve received in recent years, from both the public and private sector.
This email also avoids the overly dramatic style that characterises many phishing campaigns, where the crooks rely heavily on a combination of fear and pressure to URGE YOU TO ACT and, indeed, to ACT RIGHT NOW.
As phishes go, we have to admit, very grudgingly, that this one is better than most.
Obvious anyway
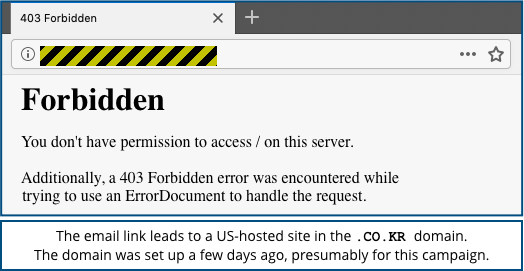
Fortunately there are other obvious signs that this is a phish, notably that reputable companies try to avoid putting links in their emails that lead directly to authentication pages, and even if they do, you shouldn’t click them anyway.
Also, the link in this phish doesn’t point to the sort of URL you’d probably expect – it leads off to a weirdly named and unencrypted (non-HTTPS) server in the .CO.KR (South Korea) domain.
Of course, in the same way that crooks are learning to spell and punctuate correctly, they’re also learning to use HTTPS websites for their scams, so you see a padlock when you click their links…
…but in this case, they haven’t bothered, so you can instantly use that fact as an unassailable reason, all on its own, to delete the email.
The .CO.KR server used by these crooks is in fact hosted in the US, using a domain that was set up just this week, presumably for short-term use in this and other similar scams.
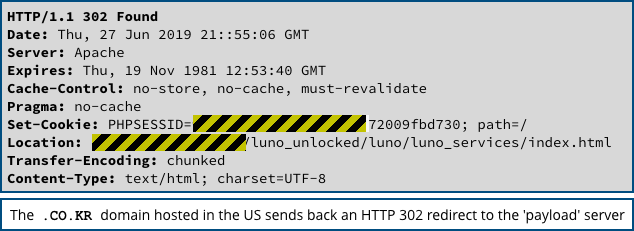
This US-based server is used only to redirect you to a .COM web address, this time hosted in Serbia, where you are presented with a fake “account unlock” page:
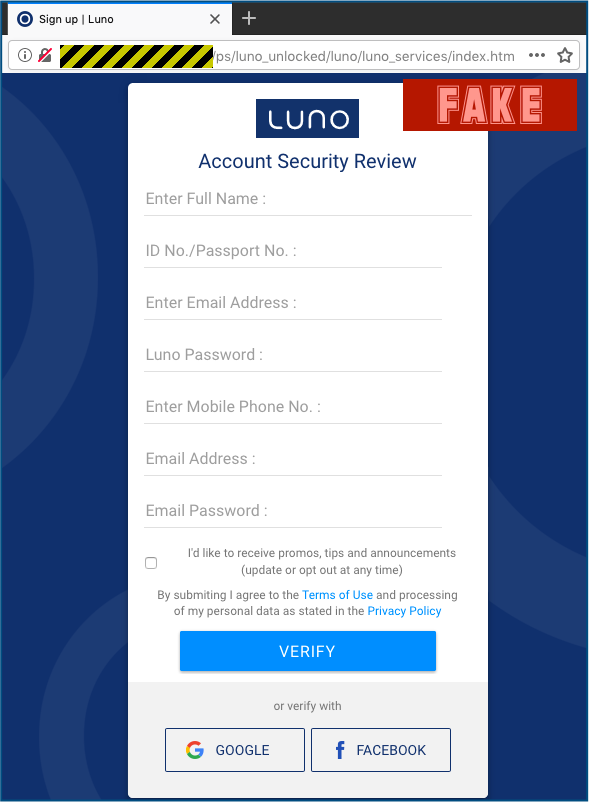
The domain name used for the second step of the scam – the address you end up seeing in your address bar, albeit without a padlock – was registered several years ago, and was presumably bought up or hacked by the crooks to give their scam some apparent legitimacy to reputation-based cybersecurity scanners.
For all we know, the owner of this domain bought it on a whim back in 2011, set up a default web server with all the best intentions…
…and then left it lying around, assuming that a server that’s not doing anything can’t cause any harm.
Until it gets “borrowed” as a sort of accomodation address for malicious web pages and scripts during a scam campaign or a malware attack.
What to do?
- If an email looks like a phish because it’s badly written, spelled and punctuated, it IS a phish. If the warning signs are obvious, don’t ignore them!
- But if an email has correct grammar and spelling, that doesn’t make it legitimate. Crooks know how to copy-and-paste, so it’s easy for them to concoct decent-looking emails even in languages they don’t understand.
- If an email looks like a phish because it insists that you login using a link in the email itself, it IS a phish. Don’t follow links that could have been sent by anyone, and probably were.
- If a website isn’t using HTTPS, don’t visit it. Some legitimate sites still haven’t bothered to add encryption to their servers – if we all stop visiting them, they’ll soon get the message to adopt HTTPS.
- But if a webserver does use HTTPS and shows a padlock, that doesn’t ensure it’s legitimate. Crooks can hack existing servers that are already encrypted, or simply get their own web certificates. The HTTPS padlock is important because it stops other people snooping or changing web pages on their way back to you, but it doesn’t vouch for the truth or accuracy of the web content itself.
- Don’t leave old domains, accounts and web servers lying around unpatched and unloved. You may end up inadvertently giving free cloud services to a crook – and if you do, the finger of blame will end up pointing at you.
If in doubt, leave it out.
If you really are a Luno customer, and you’ve received a message like this, why would trust anything in the email?
That would be like asking the defendant in a criminal trial to serve on their own jury.
Never take any cybersecurity action based on the say-so of a message that “just showed up”.
After all, if you phone the “emergency number” given in a scam email, the crook who answers will tell you what you want to hear; if you try to verify “facts” by visiting a website someone else told you to use, you’ll see what the inventor of the “facts” wants you to see.
Simply put – it’s better to follow your own nose to validate facts than blindly to follow someone else’s!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/42oofly2AD4/