D-Link patches “Joel’s Backdoor” security hole in its SoHo routers
About six weeks ago we wrote about an amusingly alarming security hole in various D-Link routers.
Simply by configuring your browser’s User Agent setting to a not-terribly-secret string of characters, you could skip the router’s login page and thus administer the router without knowing the password.
The alarming part of the hole is that the string is comparatively easy to find in the firmware of all affected routers:
xmlset_roodkcableoj28840ybtide
The amusing part is what happens if you ignore the xmlset part and reverse the rest:
Edit by 04882 Joel: Backdoor
We were never quite sure if this was a cheap trick by D-Link so that its own command line utilities could work what you might call “frictionless magic” with your router – look Ma! no password required! – or if it was the accidental aftermath of debugging code that got forgotten.
We never found out who Joel was, either, and we have no idea if 04882 was his D-Link staff number, his nickname, or even some kind of curious date-and-time marker.
The immediate workaround for “Joel’s Backdoor” was to make sure that your router wasn’t accepting admininstrator connections (known as remote management) from the WAN interface, i.e. from traffic coming directly from the internet.
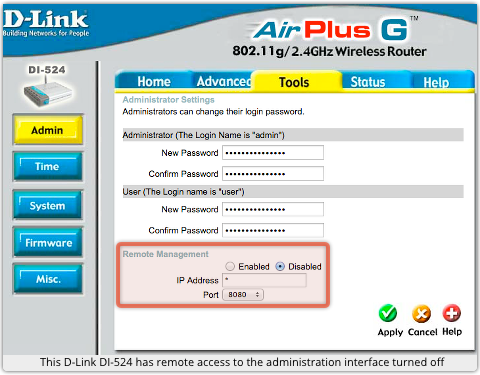
Fortunately, remote management from outside is blocked on D-Link routers by default, thus greatly reducing the risk to most devices.
→ With or without a security hole like this, you almost certainly don’t want remote administration enabled on a SoHo router. Attackers will spot your router at home, and they will regularly and routinely be probing for holes, known and unknown, that could get them into your network. (Check your logs for proof.) Never rely on being “too small and uninteresting” for the crooks.
Nevertheless, it’s still a pretty big risk if anyone on your network can tweak, or be tricked into tweaking, your router settings.
Even if you only let trustworthy friends or family onto your LAN, they might be infected with malware that gives cybercrooks a foothold inside your network and thus direct access to your router.
Or they could be tricked into clicking on a link that was served up from outside, but which points to an internal configuration page on your router.
So the good news is that D-Link has just published firmware upgrades for the routers affected by “Joel’s Backdoor,” namely the following models:
DIR-100 Rev A1 Upgrade 1.13 - 1.14/1.14B01 DIR-120 Rev A1 Upgrade 1.03/1.04RU - 1.05B01 DI-524 Rev E3/E4 Upgrade 5.12 - 5.13B01 DI-524UP Rev A1/A2 Upgrade 1.07 - 1.08B01 DI-604UP Rev A1 Upgrade 1.03 - 1.04B01 DI-604+ Rev A1 Upgrade 1.10 - 1.11B02 DI-624S Rev B1/B2 Upgrade 1.11 - 1.12B01 TM-G5240 Rev A1 Upgrade 4.00B29 - 4.01B01
You can find out more about the hole that was patched (and hear our advice to programmers on avoiding this sort of vulnerability) in this Sophos podcast:
![]()
(Audio player above not working for you? Download to listen offline, or listen on Soundcloud.)
Our discussion of the D-Link hole starts at 2’56”.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/DrjiA9ETPuM/