Every LTE call, text, can be intercepted, blacked out, hacker finds
Ruxcon Hacker Wanqiao Zhang of Chinese hacking house Qihoo 360 has blown holes in 4G LTE networks by detailing how to intercept and make calls, send text messages and even force phones offline.
The still-live attacks were demonstrated at the Ruxcon hacking confab in Melbourne this weekend, with the demo offering a recording of the hack perpetrated in part on a live network. It exploits fall-back mechanisms designed to ensure continuity of phone services in the event of overloads.
The tested Frequency Division Duplexing LTE network is more popular than TDD-LTE and operates in Britain, the US, and Australia. The competing Time Division Duplexing (TDD) LTE network is more common in Asian countries and in regions where population densities are higher.
Zhang conducted further tests after The Register inquired whether the attacks would work against TDD-LTE and found all LTE networks and devices are affected.
“I asked my colleagues to test TDD-LTE yesterday and it works well, so it really can work against all LTE devices,” Zhang says.
“This attack exists [and] it’s still reasonable.”
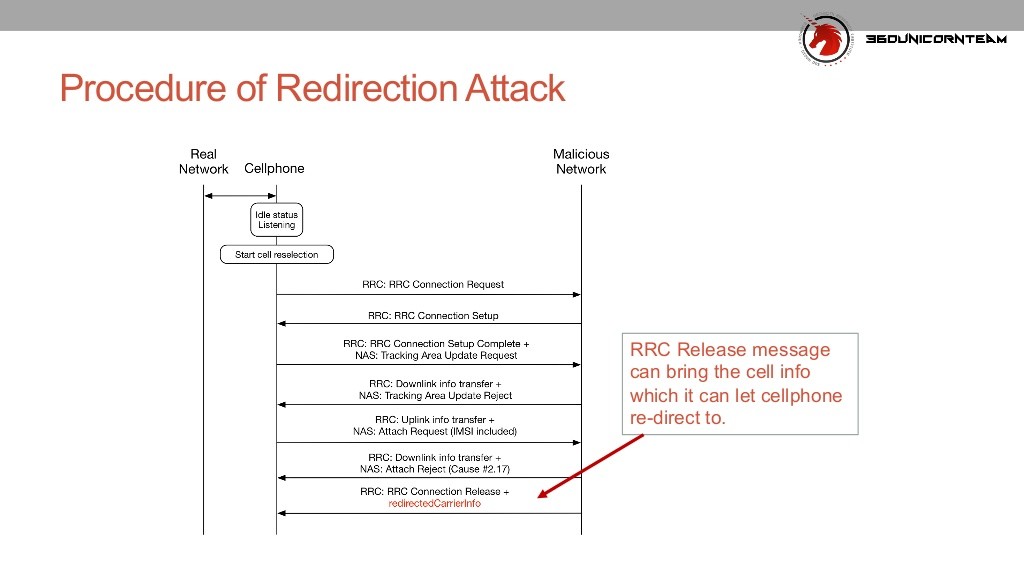
The attacks work through a series of messages sent between malicious base stations spun up by attackers and targeted phones.
It results in attackers gaining a man-in-the-middle position from where they can listen to calls or read SMS, or force phones back to 2G GSM networks where ony voice and basic data services are available.
LTE attack flow.
The attacks are not just fit for laboratories. At this year’s DEF CON hacker confab one reasearcher used IMSI catcher detection tools to find words
Zhang says the attacks are possible because LTE networks allow users to be handed over to underused base stations in the event of natural disasters to ensure connectivity.
“You can create a denial of service attack against cellphones by forcing phones into fake networks with no services,” Zhang told the conference.
“You can make malicious calls and SMS and … eavesdrop on all voice and data traffic.”
The Third Generation Partnership Project (3GPP) telco body has known of the hack since at least 2006 when it issued a document describing Zhang’s forced handover attack, and accepts it as a risk. The 3GPP’s SA WG3 working group which handles security of LTE and other networks proposed in a May meeting that it would refuse-one-way authentication and drop encryption downgrade requests from base stations.
Three of the fail-over emergency features can be abused for specific attacks, Zhang says; global roaming features allow IMSI capture, battery energy saving for denial of service, and load balancing for redirection.
Zhang uses Ravishankar Borgaonkar, and Altaf Shaik’s IMSI catcher with a femtocell to pull off the attacks.
A series of radio resource control protocol messages using the international mobile subscriber identity (IMSI) numbers captured in the IMSI catcher can allow attacks from denial of service, the ability to place calls and send text, or to interception communication.
Zhang modified the alpha open source Open LTE project to allow for tracking area updates, something critical to the attacks.
She says manufacturers should ignore base station redirection commands and instead use automatic searchers to find the best available. This would prevent attackers from forcing LTE devices to connect to malicious stations.
A warning message about security risks could suffice as a cheaper and less effective fix. ®
Sponsored:
IBM FlashSystem V9000 product guide
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2016/10/23/every_lte_call_text_can_be_intercepted_blacked_out_hacker_finds/