Festive season security myth: "If there are no links in an email, it can’t be a phish."
 Technological defences can help a lot in protecting you from phishing and fraud.
Technological defences can help a lot in protecting you from phishing and fraud.
We’re sure you’re familiar with many of them: prompt patching, anti-virus scanners with regular updates, spam blockers, web filters, firewalls, and so on.
But you’ll also have heard us urging you not to use technology as a replacement for your own caution, intuition, perspicacity, street smarts, call it what you will.
In particular, if the computer fails to say, “Don’t do it,” that’s not an automatic invitation for you to say, “She’ll be right.”
Sometimes, she won’t be right, and the crooks will have enticed you into a final step you come to regret.
Keeping street smart online
That’s why we urge you to think before you click on links in unsolicited emails, especially if they are urging you to use the link to sign in to an online service.
That’s to protect you from phishing, where cybercriminals take to you a login screen that looks like the real deal but isn’t, causing you to give away your username and password to an imposter website.
We also urge you to be cautious of email attachments, especially if you weren’t expecting them.
That’s to protect you from booby-traps, where cybercriminals feed you a crafty file such as a document or image that is deliberately rigged up to crash your browser (or PDF reader, or multimedia player, or whatever) and sneakily infect you with malware.
So far, so good.
But what if you do open an innocent-sounding attachment, and everything seems OK – no exploit, no booby-trap, no drive-by malware install?
You didn’t click on any links in the original email, so perhaps you think that you’re past the stage of being phished, and are ready to let your guard down?
Don’t do that, not least because documents such as PDF files can contain clickable links, just like the HTML in an email or on a web page.
And if the email contains the attachment, and the attachment contains the link, then the rules of transitivity apply.
You may remember that from school – it sounds fancy but it isn’t: for example, if A is bigger than B, and B is bigger than C, then A is bigger than C.
In other words, if you click on a link in an attachment, and the attachment came in an email, you are effectively clicking a link in the email.
It’s easy to lose track of that fact, not least because when you launch an attachment, it usually opens in an application like Adobe Reader or Microsoft Word, not in your browser – giving you the feeling that you have left email and its related risks behind.
Link-free phishing emails
The crooks are aware of this cognitive disconnect, and here’s a perfect example that Savio Lau and his fellow threat researchers in SophosLabs Vancouver just spotted.
You receive an unsolicited email that’s supposed to be from a real estate company:
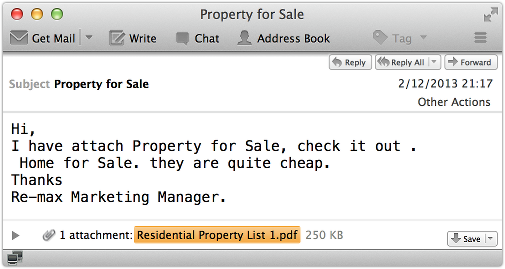
It’s not exactly the most believable invitation in the world.
(Reputable real estate agents wouldn’t make so many errors of grammar and formatting in such a short message. They probably wouldn’t say, “Hi.” And if they worked for RE/MAX in a managerial role, they’d know how to write the company’s name properly.)
But it contains no links, which seems like a good sign – if phishing needs links, then surely no links means no phishing?
Also, the attachment isn’t booby-trapped, and it contains real data, plus the ripped-off logo of a genuine real estate company:

Again, it’s not the most believable document, not least because you just vaulted from one realtor to another.
But by simple cutting and pasting from a genuine web page into a Word document, followed by printing out that document as a PDF, the crooks have moved their clickable links out of the original email, and into a file that opens neither in your browser, nor in your email client.
Better yet for the crooks, it all works equally well on Windows, Mac, Linux and even mobile devices.
If you click on one of the links in the PDF, you supposedly return to the real estate website, but you are asked to login first:
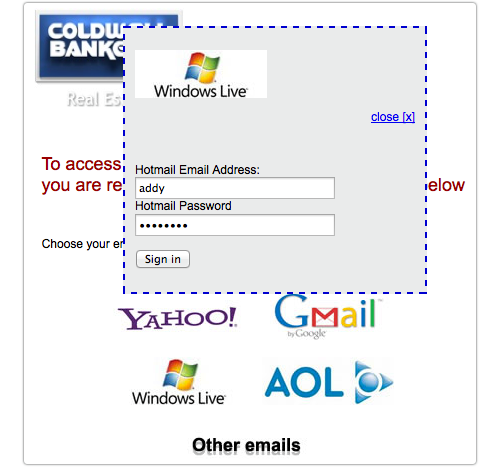
You really shouldn’t fall for this, not least because Windows Live and the Hotmail brand were consigned to the scrapheap of history nearly nine months ago – you won’t have seen them anywhere official recently.
On the other hand, the idea of a site such as a real estate company piggy-backing its login process on an existing service provider – Facebook and Twitter are very popular for this – is surprisingly common these days.
And some PDF readers (Preview on OS X, for example), don’t make it easy to see where a clickable link is going to take you, a precaution you are probably used to in your browser.
Of course, if you do fall for the login dialog, you’re not just giving away your credentials to the crooks.
You’re revealing them to anyone sniffing the network between your PC and the server, because the crooks aren’t using HTTPS:
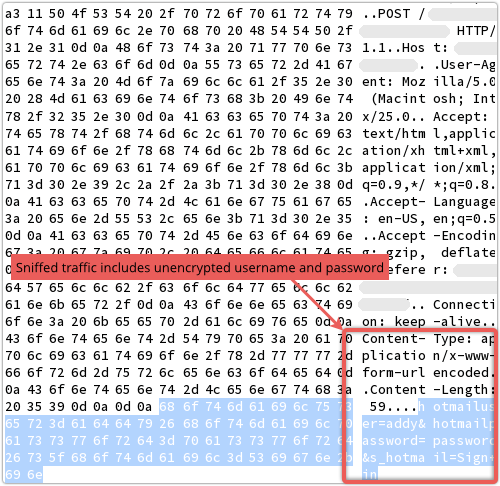
(Incidentally, in the fake login window above, clicking [Close] and [Sign in] have exactly the same effect: whatever is in the input boxes is sent unencrypted to the crooks.)
What to do
Technology would probably have saved you up front: a decent email filter or endpoint anti-virus would block the email or its attachment before you opened it, and a decent web filter would stop you clicking through from the PDF itself.
But the street smart advice we mentioned at the start would save you too:
- Think before you click on links in unsolicited emails.
- Be cautious of email attachments, especially if you weren’t expecting them.
And if you’re the go-to guy for IT amongst your friends and family, keep on reminding them this holiday season, won’t you?
Note. Sophos products detect and block the bogus attachment shown above as Troj/Phish-DC.
Image of topiary chain courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/ZdIiOYKySJM/