Firefox 25.0.1
Firefox just pushed out a minor browser update, bumping its version number from 25.0 to 25.0.1.
I don’t allow Firefox full autonomy over my updates, preferring to use the Check but let me choose option, so I was presented with a now-familiar popup to let me know what was on offer:
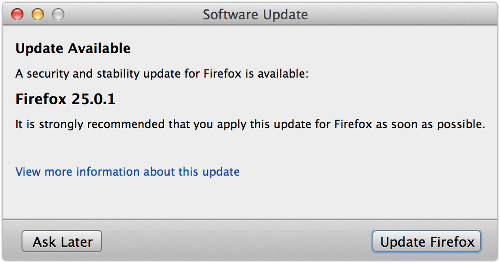
A security and stability update for Firefox is available: Firefox 25.0.1. It is strongly recommended that you apply this update for Firefox as soon as possible.
“There’s not much point,” I thought, “in using Let me choose if I don’t do some reading first, even though I almost always decided to board the update train at once.”
The Release Notes reiterated the security-related importance of the update:
FIXED – 25.0.1: New security fixes can be found here [link]
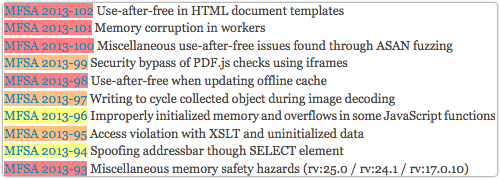
And the Known Vulnerabilities page listed five critical, three high and two moderate security advisories:
Eagle-eyed readers, however, will notice that these look very much like the bugs that were fixed in 25.0.
In fact, they are the security fixes from 25.0, all of them listed as patched on 29 October 2013.
A small mystery, to be sure, but not an encouraging one for users who like to read, learn and understand more about security patches before applying them.
What happened?
Perhaps there weren’t actually any security fixes, but Mozilla’s release boilerplate just assumed that there probably would be, and warned you anyway?
Or perhaps there were security fixes, but Mozilla released the update and published all the boilerplate pages before updating the pages to which they link?
→ Apple takes the latter course most of the time: you get a link to a generic security page (Apple’s well-known landing page HT1222) that usually only gets updated later with the link you really want. Let’s hope Mozilla hasn’t copied Apple’s often laboured and sluggish disclosure strategy.
What to do?
As you can probably guess, I just shrugged and boarded the train.
The update was only 236KB, so there wasn’t a lot to it, and everything seemed to work.
Is this the way of the future?
In a recent Chet Chat podcast, fellow Naked Security writer Chester Wisniewski asked that very same question, albeit in a slightly different way.
Chet coined the term local cloud as a light-hearted way of describing applications that you install and run locally, but which might as well not have a version number because they just update automatically over the internet, on a schedule to suit themselves.
In other words, local cloud applications are like cloud apps in the sense that “you get what you get,” even though they load and run offline, and you don’t need to run them in a browser.
Google’s Chrome is as good as there already; Apple’s iOS and Mozilla’s Firefox are getting pretty close.
Android is as good as there, too, with the added confusion that different Google partners and providers push out their updates at wildly varying times. (Some Android devices never get the latest updates at all, sometimes leaving them vulnerable indefinitely, perhaps to enormous security holes).
Is this a good thing?
Take a listen to the discussion in the podcast, and let us know what you think.
(We start talking about Android at 6’01” and about the local cloud concept at 9’48”.)
![]()
Audio player above not working for you? Download to listen offline, or listen on Soundcloud.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/p0we9nh-iXE/