Firefox 31 has arrived
 Firefox 31 is out.
Firefox 31 is out.
So is its updated conservative older brother, the Extended Support Release, now at 24.7.
And Firefox’s email-oriented cousin Thunderbird gets updated, too.
Thunderbird also goes to versions 31 and 24.7.
The elevator pitch from a security point of view is:
- 11 security bulletins
- 3 critical
- 5 high
- 2 moderate
- 1 low
Low-rated vulnerabilities, which don’t even get a colour code, are fairly rare in the Mozilla stable, and involve “minor security vulnerabilities such as Denial of Service attacks, minor data leaks, or spoofs.”
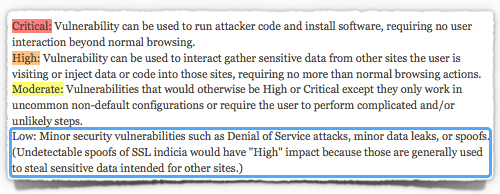
Loosely speaking, you can think of them as security holes that a crook is very unlikely to be able to turn to your financial disadvantage.
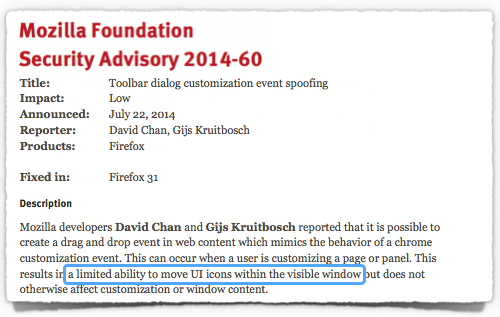
Nevertheless, this month’s low-security patch, MFSA2014-60, gives an interesting insight into the esoteric nature of bug hunting.
MSFA2104-60 also reminds us that bugs that might have been identified as little more than display-related annoyances a few years ago are today considered security holes in the their own right.
The bug doesn’t sound like much – as Mozilla’s bulletin puts it, an attacker has “a limited ability to move UI icons within the visible window.”
But Mozilla has recognised that even just messing around with the workflow of a website – for example one that involves financial transactions, changing privacy settings, or publishing content – can have security implications by tricking you into taking an action that you later realise wasn’t what you intended.
It’s easy to blame the user for that sort of mistake, on a sort of caveat emptor basis, but here’s an experiment that might convince you otherwise, assuming you are a left-to-right language user:
- Start a sequence of dialogs that you are entirely familiar with and will recognise even if you can’t read the text they contain.
- Switch to Hebrew, Arabic or any other right-to-left language.
- See how tricky it is, even concentrating hard, just to get from dialog to dialog now that the buttons are reversed.
High and critical bugs
This update also has a number of high-rated vulnerabilities, such as buffer overflows and use-after-free flaws, that are documented as “potentially exploitable.”
We’d usually expect that sort of bug to get a Critical rating from Mozilla; the developers aren’t saying why they consider them only High this time round.
The critical bugs are of a similar type; presumably the Mozilla experts consider that, if attackers had discovered the bugs, they’d be more easily able to weaponise.
That’s where you work out how to trigger a vulnerability that causes a crash in such a way that the crash doesn’t simply pop up a “this program has done something bad and terminated” error, but actually drops executable control into your lap.
Of course, any vulnerability that can reliably trigger a crash can be used to cause a Denial of Service (DoS), so it’s bad by definition.
But going from DoS to RCE (remote code execution) is often much harder than it sounds.
It’s a bit like the difference between using explosives to demolish an old building, and blowing up the building so that a predetermined brick drops cleanly and unbroken into a bucket placed at a predetermined spot.
As usual, although the bugs are shared between Firefox and Thunderbird, the risks posed by many of the vulnerabilities rely on JavaScript shenanigans, so they are less likely to be exploited via email, because scripting is off by default when Thunderbird displays messages.
What more can we say?
We’ve updated, and everything (including our plugins) still seems to be working just fine, with no visual surprises like we had in Firefox 29.
Indeed, for what it’s worth, this article was published using FF 31.0.
So we suggest that you update, too.
Oh, and whether you are a Firefox user or not, why not vote in our Which Browser Do You Trust The Most poll?
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/aKSaM2fQCco/