Flying Naked: Why Most Web Apps Leave You Defenseless
Imagine for a moment a major airline only checking 10 percent of its fleet for safety problems. Now imagine that when they do check an aircraft, they find 22 safety problems (some major, some minor). That would represent a crazy business risk for any airline. Roughly 90 percent of the fleet wouldn’t be checked for safety and mechanical problems. That would never fly. But yet, I am here to tell you that 90 percent of applications in most organizations are naked — since they have no application security defenses in place.
When I say “application security” I’m not talking about infrastructure, operating systems, firewalls, intrusion detection systems, etc. I’m talking about the custom code you wrote for your business, internal and external. The defenses we have for these custom applications don’t work. Not surprisingly, this is where 54 percent of the breaches come from. Here’s why they aren’t protecting us:
Network security products work because they know what’s behind them. They know that they’re defending Windows, MacOS, Internet Explorer, and Google Chrome so they know how to identify attacks on those products and stop them. Custom application code is different. Every custom application is a beautiful and unique snowflake; you can’t identify attacks on these snowflakes by looking at network traffic. Period. Only the application knows what defenses are in place and what input will allow an attack to succeed. The trick is knowing how to get this knowledge out.
The image below is an attack on one of those snowflakes that happens to process Morse code.
In fact, this is a Cross Site Scripting (XSS) attack encoded using Morse code. To state the obvious, there is no product on the planet that stops attacks in Morse code. I use this exaggerated example to make a very serious point. The attack could be a number, a short string of any characters, a null byte, anything… There is no way to know what an attack is unless you know the application itself.
Application security programs aren’t working
I’ve been in the application security field for a few decades now, and I’ve worked on AppSec programs at almost a hundred companies and federal agencies. What I see is that most organization have hundreds or thousands of web apps and web services. Yet even the best funded and “mature” programs are only really testing 10 percent of their applications. That leaves 90 percent naked, with no real security. And many of the breaches you read about are against the 90 percent. The 10 percent are in pretty bad shape, too, averaging 22.4 serious vulnerabilities per application.
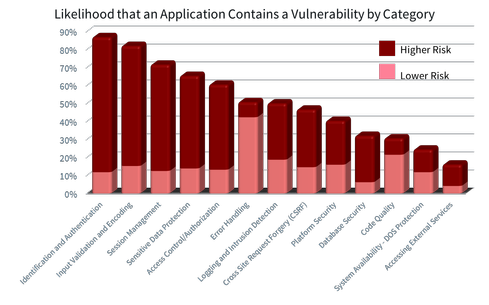
These stunning numbers come from Aspect Security’s “2013 Global Application Security Risk Report.” We used a combination of manual code review, manual penetration testing, and automated tools to analyze thousands of critical applications. The most prevalent vulnerabilities are: Identification and Authentication, Input Validation and Encoding, Session Management, Sensitive Data Protection, and Access Control. Compare these results with similar results from tool vendors, and you’ll see a striking difference — because tools alone can’t effectively test for at least three of the top five categories.
Jeff Williams has more than 20 years of experience in software development and security. He is a founder and CTO of Contrast Security, offering a revolutionary application security technology that accurately identifies vulnerabilities at portfolio scale without requiring … View Full Bio
Article source: http://www.darkreading.com/application-security/flying-naked-why-most-web-apps-leave-you-defenseless-/d/d-id/1127875?_mc=RSS_DR_EDT