"Followup phish" targets possible victims of last month’s JP Morgan Chase card breach
 Here’s a brief reminder of how cybercriminals use real security disasters to cause follow-up disasters of their own.
Here’s a brief reminder of how cybercriminals use real security disasters to cause follow-up disasters of their own.
You’ll probably remember that we wrote, almost exactly a month ago, about a data breach at JP Morgan Chase.
About 450,000 of the 25,000,000 users of Chase’s UCARD debit card product had their card data stolen.
That put just under 2% of cardholders in the hot seat, which was bad enough, but left the other 98% in a sort of data security limbo.
Was there a problem or not?
Would Chase’s investigations lead to further action or not?
Would they get a warning some time down the track, like many users did in the wake of Adobe’s giant breach last year?
With this in mind, we weren’t surprised, here at Naked Security, to receive what you might call a “Chase Followup Phish,” looking like this:
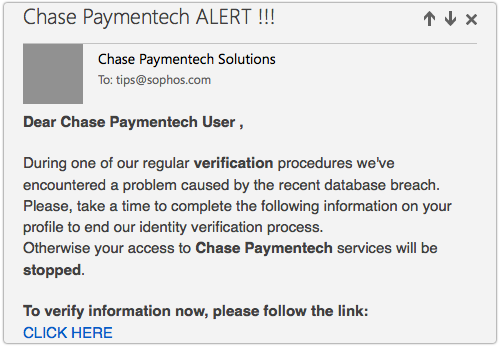
Dear Chase Paymentech User,
During one of our regular verification procedures we’ve encountered a problem caused by the recent database breach. Please, take a time to complete the following information on your profile to end our identity verification process. Otherwise your access to Chase Paymentech services will be stopped.
To verify information now, please follow the link:
[CLICK HERE]
The phish isn’t terribly sophisticated, as it dumps you at a merchant page, not at a UCARD page.
(Merchants are Chase customers who process payments; UCARD customers are Chase product users who hold a benefit payments card to make purchases.)
Nevertheless, the phish passes casual visual muster, because the HTML, stylesheet and imagery are all ripped off from Chase’s own servers:
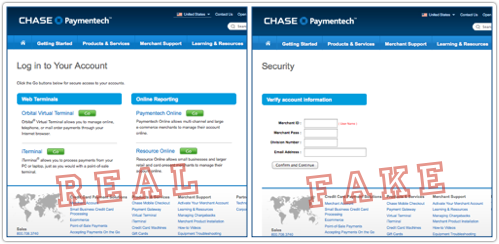
Actual merchants shouldn’t be fooled, because Chase’s official merchant login pages look quite different to the phish.
JP Morgan Chase’s actual page asks for different information, and uses HTTPS with a certificate officially issued to Chase Paymentech:
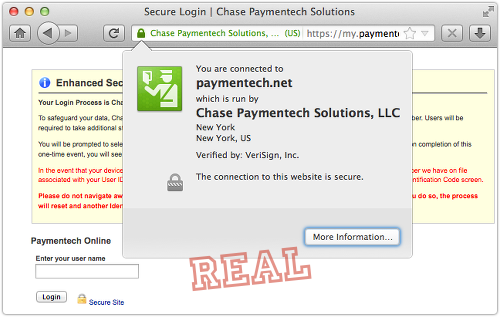
Bear in mind that even – perhaps especially! – a bank that has suffered a security lapse won’t email you with a clickable link that takes you to a login page.
That’s to force you to login under your own steam, where the link you use is not controlled by some outsider who just sent you an email.
So whenever you receive an email link that does go to a login page, like this one, you can immediately be certain is it bogus.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/OsSv3VfSJCM/