Forbes Hack password shootout: Gmail vs Yahoo vs Hotmail vs AOL – whose users are the smartest?
Note. Please don’t take the results below too seriously. We’re just trying to put a bit of fun into the serious business of choosing passwords, and we’re ending with a touch of optimism about our changing attitudes to security.
Yesterday, we wrote about the breach of Forbes’s 1,000,000-strong user database by the Syrian Electronic Army.
The purpose of that article was threefold:
- To report the news of the breach (sadly, one of many recently), as a reminder that security is important.
- To quantify the risk of what was stolen, because Forbes failed to do so in its own notification.
- To end with a spot of praise for the beleaguered Forbes for storing its passwords satisfactorily, if not actually quite as well-hashed as we’d have liked.
After many public password disclosures, there’s often a good-humoured race amongst security professionals to see who can crack the most passwords the fastest, or who can find the most obscure and amusing passwords from the database.
But, as we explained in yesterday’s article, Forbes was using PHPass Portable hashes, which means that there is a loop of 8193 MD5 hash calculations for each password check.
That’s still quick enough to test a single password against the database efficiently – for example, when a user tries to login – but not so quick that an attacker can try millions, or perhaps even billions, of passwords per second.
The hash-cracking race
So, if you’re wondering why you haven’t seen an extensive password list computed from the Forbes Hack yet: it’s because of the iterations in the hashing process.
What would take you an hour against password data hashed once with MD5 will take you over 8000 hours, or roughly from New Year to Thanksgiving, using Forbes’s approach.
Sadly though, that doesn’t mean that everyone is safe.
If you’ve chosen unwisely, your password may nevertheless quickly be guessable by hackers.
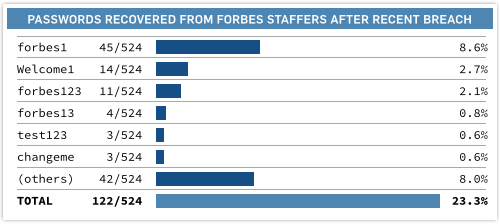
Yesterday, for instance, we extracted data for just over 500 forbes.com staffers from the 1,000,000 records leaked by the SEA.
Then we had a go at their passwords, and within an hour we had recovered close to a quarter of them:
What else can we tell from the data?
A comprehensive crack of all 1,000,000 passwords is out of the question, thanks to the 8193-iteration MD5 loop.
So we decided instead to concentrate on users with known-bad passwords.
Looking through the password data shows that each record has a timestamp, with the first record stamped in 2009, and the last record stamped in February 2014, just before the breach.
Since the earliert records all have forbes.com addresses, and start with an account called “admin”, it’s reasonable to assume those timestamps show the time the each account was created, rather than the time it was most recently used.
That suggests the question, “Is there a difference in password quality from 2009 to 2014?“
Put another way, “Have we learned anything about passwords in the past five years?“
Another possible question is whether there is a difference in password quality between users of different email services.
A count of the email accounts seen in the database shows that the Big Four email domains are pretty much as you would expect:
gmail.com 413,978 (39%) yahoo.com 184,665 (17%) hotmail.com 88,059 (8%) aol.com 25,633 (2%)
That suggests a second question, “Which service had the most passwords exposed?“
Put another way, “Which email users are the smartest about passwords?“
What we measured
We extracted eight files of password hashes to crack, as follows:
FG10K: First 10K Forbes accounts for Gmail users FY10K: First 10K Forbes accounts for Yahoo users FH10K: First 10K Forbes accounts for Hotmail users FA10K: First 10K Forbes accounts for AOL users LG10K: Last 10K Forbes accounts for Gmail users LY10K: Last 10K Forbes accounts for Yahoo users LH10K: Last 10K Forbes accounts for Hotmail users LA10K: Last 10K Forbes accounts for AOL users
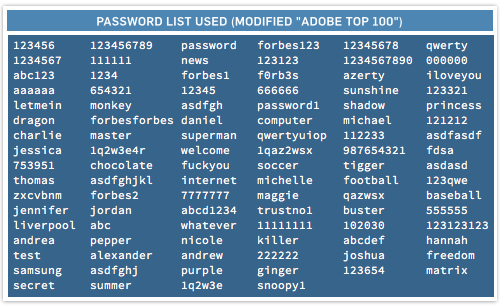
For a representative list of commonly-used bad passwords, we used the Top Hundred list from the recent Adobe breach, with six Adobe specific passwords (e.g. adobe1, adobeadobe) altered to suit Forbes (e.g. forbes1, forbesforbes):
Then we cracked each of the sets of 10,000 hashes against our Top Hundred list, which took only a few minutes with multiple processors on the job, despite the PHPass-based hash-stretching.
It was hot work for a summer’s day, as the following htop graph of CPU usage shows:
Which email service has the smartest users?
Before you read any further, why not give way to your own prejudices about users of the various webmail services?
Close your eyes and guess what order they finished in.
Then take a look and see if you were correct.
• For the first 10,000 Forbes users listed in the database for each email service, dating roughly from 2009-2012:
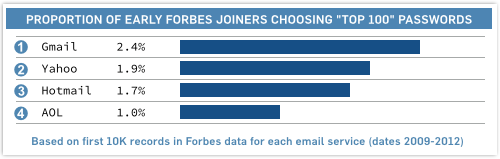
AOL users chose most wisely, and Gmail users were the most reckless! (Admit it: you didn’t expect that, did you?)
• For the last 10,000 Forbes users listed in the database for each email service, dating roughly from 2013-2014:
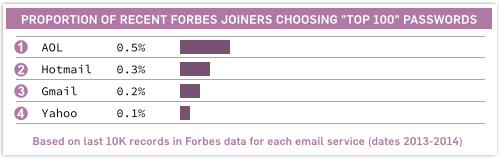
Yahoo users are now the safest. (You didn’t expect that either, did you?)
How well have we aged?
The great news from the figures above is this: Forbes users who signed up more recently seem to have chosen their passwords more wisely.
Here’s the approximate likelihood that more recent Forbes joiners will choose a Top Hundred password, compared to those who joined in 2012 or earlier:
Yahoo users: 11x less likely Gmail users: 9x less likely Hotmail users: 5x less likely AOL users: 2x less likely
Of course, we shouldn’t really say that recent joiners have chosen more wisely, since the hashing slowdown enforced by Forbes means that we’ve only had time to crack obvious passwords.
But we can say that they seem to have chosen less badly.
That’s not quite the same thing, but it’s jolly good news nevertheless.
It strongly suggests that you can change people’s security attitudes for the better! (Admit it: you didn’t expect that, did you?)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5pXiUVIV-U4/