Forum software vendor vBulletin breached – apparently by vBulletin hack
 According to its own website, vBulletin is “the world’s leading community software,” and many forums, message boards and social networking sites use it.
According to its own website, vBulletin is “the world’s leading community software,” and many forums, message boards and social networking sites use it.
From time to time, vulnerabilities in vBulletin make the headlines because they catch out vBulletin customers who haven’t patched in time (or who are unlucky enough to be the first victims of a new security hole).
For example, the Ubuntu Forums website was taken over back in July 2013, and popular Apple-related site Macrumors was breached just last week.
Both of those sites, it seems, were vBulletin users.
Another high-profile vBulletin user, of course, is vBulletin itself…
…and you can probably guess where this is going.
You wouldn’t know anything was amiss from vBulletin’s main page, but a visit to vBulletin’s own forum reveals the sort of message that every forum operator hopes never to have to write:
Important Message Regarding Your Account
Often, what comes up when you click through to the message itself is the sort of platitude that call centres use when they claim “your call is important.” (So important that it has just been placed in a lengthy queue rather than actually answered.)
And vBulletin fell into that verbiage trap:
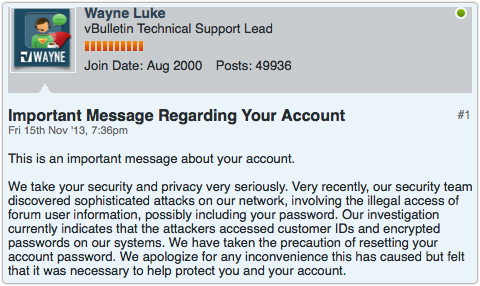
We take your security and privacy very seriously.
A touch of customer-facing advice, if I may.
If you are about to apologise to your customers for having been bad at security, don’t start off by praising yourself for being good at it.
Start off by apologising for having been bad at it.
Very recently, our security team discovered sophisticated attacks on our network, involving the illegal access of forum user information, possibly including your password.
You don’t need to use the word sophisticated.
It’s cold comfort to your customers, and all it really means is that you were less sophisticated than the crooks.
That doesn’t bode well for any claims you may make about defending successfully the next time there’s an attack.
Just say that you detected a breach, though sadly only after it had taken place.
Our investigation currently indicates that the attackers accessed customer IDs and encrypted passwords on our systems.
Avoid saying the passwords were encrypted if they were hashed.
The last company that admitted its stolen passwords were “encrypted” was Adobe, and that didn’t end well. (The passwords were encrypted, rather than hashed, all with the same key, and in such as way that repeated passwords produced repeated ciphertext.)
Also, tell your customers how you hashed their passwords so they can form their own opinion about how likely it is that a cracker might recover those passwords by trial and error.
For example, the Ubuntu Forums hacker claimed that the stolen passwords in that breach were “encrypted [sic] with the default vBulletin hashing algorithm (md5(md5($pass).$salt)”, which means just two single-block MD5 calculations for every password trial.
Modern password crackers costing no more than $20,000 can compute hundreds of billions of MD5s per second.
The breach notification ends like this:
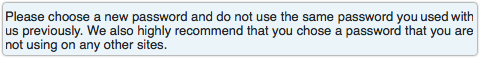
Please choose a new password and do not use the same password you used with us previously. We also highly recommend that you chose [sic] a password that you are not using on any other sites.
That’s good advice, and given that vBulletin has just apologised for poor security of its own, I can fully understand why the company wasn’t more forceful here.
However, I’ll be more forceful on vBulletin’s behalf:
Do not chose a password that you are using on any other site. ONE ACCOUNT, ONE PASSWORD.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/nyHl7aUDsGc/