GinMaster, unwanted Android apps and legit apps gone bad
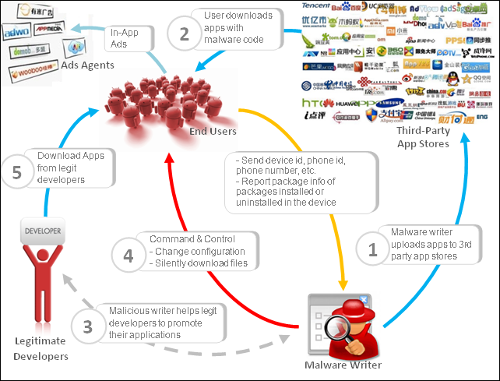
Thursday began with Rowland Yu of SophosLabs Australia presenting “GinMaster : a case study in Android malware”. GinMaster is so named because of its use of the GingerBreak jailbreaking exploit to gain root privileges on compromised Android devices.
GinMaster is primarily distributed in China, which Yu estimates has more than 5 million infected Android devices at any given time.
What is even more concerning is the escalation in evasive techniques used by the malware authors to avoid detection. The Android landscape is catching up to the sophistication of Windows malware, a very frightening revelation.
Yu provided an interesting visual depiction of the GinMaster ecosystem showing how the criminals behind this malware use multiple methods to maximize the profitability of adding you to their botnet.
Later in the morning it was Gabor Szappanos from SophosLabs Hungary who stepped up to the lectern to present “Hide and Seek – how targeted attacks hide behind clean applications”.
In the past we have written about the abuse of stolen or fraudlently obtained certificates to sign malware, but Gabor has been looking into something even more diifcult to detect.
Legitimate applications that are signed, but contain a bug known as the DLL search order flaw enabling attackers to inject malicious code into seemingly safe applications.
The most surprising thing in the presentation for me was the use of open source software as a vehicle for malicious code.
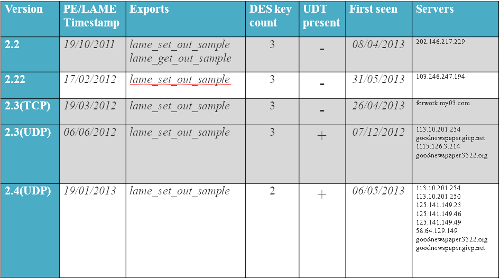
Szappanos showed how the LAME MP3 encoder was being used by attackers by simply adding two additional malicious exports that were designed to blend into real encoder commands.
Last up was Vanja Svajcer from SophosLabs Croatia. He presented “Classifying PUAs in the mobile environment”, a paper attempting to create a set of common criterea for detecting and determining the differences between malware and things that aren’t neccessarily malicious, but are clearly undesireable for some or all users.
Many applications may fall into the category of potentially unwanted. Some may require access to too much sensitive information, some may be pornographic and others may contain extremely agressive advertising components to sponsor their “freeness”.
It is difficult for vendors to be compared today due to varying ideas of what potentially unwanted might mean, so hopefully there will be some consensus as a result of this paper.
I also had the pleasure of producing a podcast with Paul Ducklin yesterday on the three things everyone must do to protect themselves and others for National Cyber Security Awareness Month.
Listen to our “Do These 3” tips now in this short, special-issue podcast
(03 October 2013, duration 8’58”, size 5.4MB)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/HFT3lxfOOrQ/