Google reports new shenanigans in ongoing Turkish internet blockade
 Turkey goes to the polls today amongst an ongoing brouhaha over internet access.
Turkey goes to the polls today amongst an ongoing brouhaha over internet access.
A week ago, the government blocked access to Twitter.
Apparently, the microblogging site had failed to comply with local court orders for content takedown.
The block certainly seemed to backfire, with numerous stories reporting that Twitter usage in Turkey more than doubled after the ban.
Just how accurate were the “surge in Twitter” stories about Turkey?
As an interesting aside, the surge in twittering in Turkey probably wasn’t anywhere near as big as the claims you have seen.
Many stories mention the figure 138%, claiming something along the lines of “an increase in volume of over 138 percent in tweets posted from Turkey before the ban and just after.”
That claim, however, and all of those reports, seem to come from a single source, these figures from social media company Brandwatch:
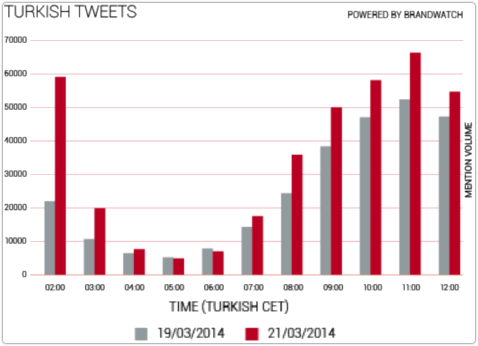
Brandwatch didn’t provide the raw data used to draw its graph, but by reading off the numbers as accurately as I could, I came up with this:
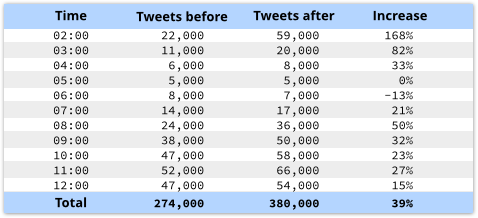
I couldn’t find an increase of 138% in any of the comparable before-and-after readings in that chart.
The overall increase, however, was 39%, suggesting that Brandwatch has confused an increase by a factor of 138% (i.e. new = 1.38 x old) with an increase of 138% (i.e. new = old + 1.38 x old).
At any rate, Brandwatch’s numbers don’t show an increase of 138% (well over double), but rather an increase of 38%, or perhaps 39% (just over a third more).
But, doubling in tweets or not, Twitter lovers in Turkey did take to the streets, literally and figuratively.
Graffiti in Istanbul openly promoted the use of Google’s free DNS servers, located at the IPv4 addresses 8.8.8.8 and 8.8.4.4:
That’s because the easiest way for a country to get its ISPs to block access to a site like twitter.com is to tell them to stop resolving the name of the site in their DNS servers.
Most home users rely on their ISP for access to DNS, the Domain Name System that turns human-style internet names to computer-style numbers.
For example, when you ask your ISP how to find twitter.com, this is what happens.
Your ISP asks the so-called root servers (there are only 13, so a DNS server can easily keep a local list) where to go for authoritative answers for .com; then it asks one of those .com servers to tell it where twitter.com lives; then your ISP tells you the answer.
But the ISP can cheat: when you ask for twitter.com, it can simply pretend it doesn’t exist by sending the answer NXDOMAIN, short for “non-existent domain.”
That’s where bypassing your usual DNS server and using one of Google’s free Public DNS servers comes in: Google prides itself on providing unmodified, unfiltered DNS results,
The next step, of course, was for Turkish ISPs to start blocking traffic to Google’s servers, giving users one less public source by which to find out where twitter.com lives.
Then, late last week, Turkey started blocking YouTube as well, apparently in an effort to restrict access to a leaked audio recording about possible military intervention in Syria.
And the next move in the block-circumvent-block-circumvent race, claims Google, was yet another layer of active intervention by Turkish ISPs:
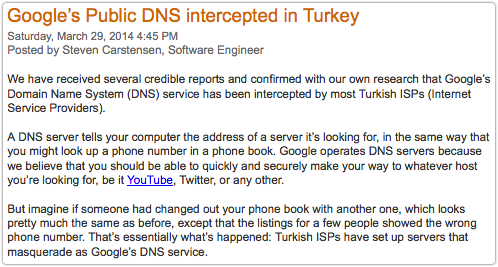
We have received several credible reports and confirmed with our own research that Google’s Domain Name System (DNS) service has been intercepted by most Turkish ISPs (Internet Service Providers)…
…But imagine if someone had changed out your phone book with another one, which looks pretty much the same as before, except that the listings for a few people showed the wrong phone number. That’s essentially what’s happened: Turkish ISPs have set up servers that masquerade as Google’s DNS service.
Just blocking traffic to 8.8.8.8 and 8.8.4.4 is rather a giveway to anyone who sets their computer to use Google’s DNS servers, because DNS simply stops working.
That means that very little will function properly: no websites will be accessible, software updates will probably fail, email and chat won’t work, and although you’d technically be “on” the internet, you’d immediately realise you were also as good as cut off from it.
Redirecting DNS traffic to imposter servers is much sneakier.
As far as you can tell, your traffic to 8.8.8.8 is getting there; DNS replies are coming back; and (as suggested by Google above) almost everything seems to be normal.
This is exactly the approach taken by the infamous DNSChanger malware that dominated security news two years ago.
The malware changed your DNS settings and then mostly told the truth, but occasionally stepped in to misdirect your web traffic to fraudulent sites.
→ This video was geared at a particular DNSChanger-related cutoff time, now well past, so its advice is somewhat dated. But it is still an excellent reminder of why DNS is especially important, and how you can be uninfected yet still affected even after you remove malware from your computer.
What to do?
Dealing with DNS subterfuge is surprisingly hard.
Imagine a DNS server that told the truth 999 times out of 1000, but misdirected you to a carefully constructed imposter site once in every 1000 requests.
Would you back yourself to notice?
That’s one of the reasons the DNSChanger crooks made millions of dollars out of DNS trickery, though happily for the rest of us, at least some of them were caught.
There are a few things you can to help you avoid trickery:
• Use HTTPS (secure HTTP) connections whenever you can, and double-check the certifcates that come back.
This makes forgery harder.
• If your browser supports certificate pinning, you might want to learn more about it.
A rotten ISP might be able to arrange to have fake certificates issued in other websites’ names.
“Pinning” lets websites provide additional information about their certificates, such as who’s allowed to sign them, which makes forgery harder yet again.
• Consider learning how to use Tor, an open source anonymising system.
A large number of volunteers around the world allow their computers and bandwidth to be used to bounce around other users’ traffic randomly so it emerges onto the internet in some unpredictable spot.
But before you start using Tor, remember that it isn’t a panacea.
Firstly, you might be breaking the law in your jurisdiction.
Secondly, what you do with Tor is largely anonymous and therefore confidential (though not entirely so), but the fact that you are using Tor is hard to disguise.
In other words, by taking steps to keep a low profile online, and to avoid surveillance, censorship, or geographical web blocking…
…you may ironically end up drawing attention to yourself.
Image of Turkey flag courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/o0Q-ZciqSXc/
