Has the PlayStation Network really been hacked? Should you change your password?
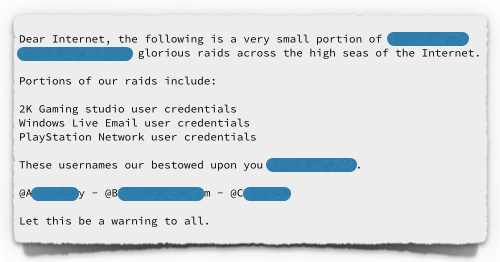
A smallish sample of usernames and passwords allegedly stolen from services listed as PlayStation Network (PSN), Windows Live and 2K Gaming has been leaked by a trio of crackers calling themselves…
…naaaah, we’re not going to repeat their names.
We’ll just say, three crackers have dumped a text file of about 5500 lines that they say are credentials from the above services.
Usually, when crooks leak some of their haul, they’re assuming that you’ll go any try some of the accounts yourself (which would be a criminal offence in most countries, even if your motivation was honourable, so for your own sake don’t do it).
The idea is that once a few people have tried a few randomly-chosen accounts and found that they work, the story that the crooks have “plenty more where those came from” suddenly sounds more plausible.
The dump
The dumped data is in a variety of formats, but many of the entries have at least an email address and what purports to be a password to go with it.
We’re not going to publish any of the dumped credentials, but where passwords are allegedly revealed, they are all somewhere between trivial and very easy to crack, such as:
password password123 metallover easy-hack girlfriendsname Initial.Lastname n00bn00b
This suggests that the passwords (if they are real) were not recovered in plaintext form but had been hashed somehow, and only the sort of hashes that could easily be cracked made the list.
Some of the entries have what looks like a password hash as well, with a mixture of formats like this:
61b7f3e2f4f4734b950a2614864c8ad4 1f7f27de490021893e89ccd9d15b49f5316791fe cc1e3cb903d0cf1c802f95c1ee045167$8G96aa56 $1$MWY2MDk2$ZTljNTdiMTNkZDkzYWQzYz
Judging by the lengths of each of the strings, you might guess these are meant to be:
32 hex chars - 16 binary bytes - unsalted MD5 hash 40 hex chars - 20 binary bytes - unsalted SHA1 hash 32 hex chars + $ + 8 alphas - salted MD5 hash $1$ + 8 b64s + $ + 22 b64s - passwd-style salted MD5 hash
Seems a bit of a strange mix to me.
Real or hoax?
Are the account credentials real?
If so, were they really hacked loose from the networks claimed?
Or were they begged, borrowed or stolen from some other crook who had acquired the data via other means?
→ The presence of hashes means nothing from a forensic point of view. By publishing a hash and a matching password, you are inviting readers to infer that you stole the hash from the service provider, and then cracked the password from it. But you might have acquired the password straight from a user’s computer, e.g using keylogging malware, and simply calculated the hash directly from it. Or made the whole thing up.
Should you change your password?
The answer, I suppose, is that just in case the crooks are telling the truth, then you might as well change your password, assuming that you use one of the three services they claim they cracked.
But what if the crooks are lying?
Well, even if all the passwords in the dumped list are made up, they are nevertheless of a sort that should make you think, “That could have been cracked, because it’s just too guessable.”
So, at the least, take this as a warning to learn How To Pick a Proper Password:
→ Can’t view the video on this page? Watch directly from YouTube. Can’t hear the audio? Click on the Captions icon for closed captions.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/gk8CQtLsnwc/