Have we seen the end of the ZeroAccess botnet?
 Since Microsoft took positive action against the ZeroAccess botnet at the beginning of December, SophosLabs has been paying close attention to see how the owners would attempt to revitalise the botnet and return it to profitability.
Since Microsoft took positive action against the ZeroAccess botnet at the beginning of December, SophosLabs has been paying close attention to see how the owners would attempt to revitalise the botnet and return it to profitability.
Microsoft has now declared that the authors have effectively “decided to surrender control of the botnet.”
So, based on our own statistics do we at SophosLabs agree with that claim?
The takedown efforts of early December centered around the servers used by the various plugins that ZeroAccess downloads from its P2P network.
These server addresses are also retrieved from files downloaded through the network, so the obvious way to make the botnet do something useful again is to seed new server addresses into the network.
However, Microsoft’s team knew this and were monitoring the botnet for new plugins. As soon as new server addresses appeared Microsoft acted very quickly in conjunction with law enforcement to make the servers inoperable.
The last version of each plugin seeded into the network contains the surrender message “White flag”, suggesting that the authors have given up on this course of action. The plugin files either contain a resource that just holds the text “WHITE FLAG” or only contain code to write the message to the kernel debugger:
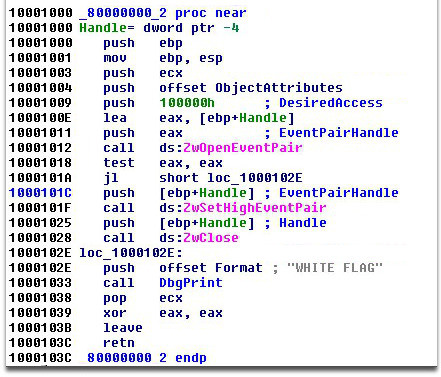
We can see from the time stamp on each of these plugins that once the decision was made to give up trying to reawaken the botnet, new versions were signed and pushed out in very close range of each other:
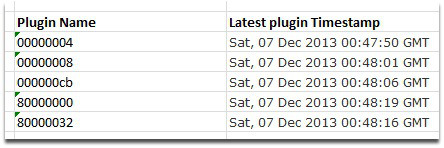
The ZeroAccess botnet has always managed to maintain a very large size by ensuring that huge amounts of new droppers are pushed onto the internet every day.
Our measurements show that the ZeroAccess authors are no longer growing or even maintaining the size of the botnet as the numbers of new droppers have all but dried up over the last few weeks.
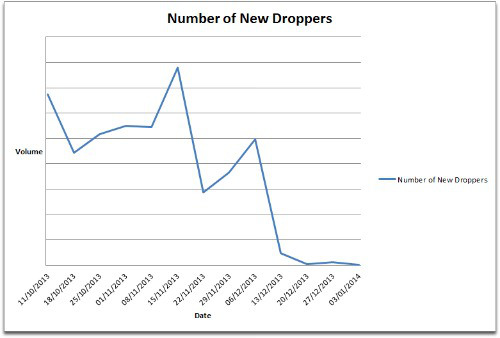
This is also reflected in the number of detections we are seeing on customer machines, as existing ZeroAccess infections are cleaned up and no longer replaced with new infections.
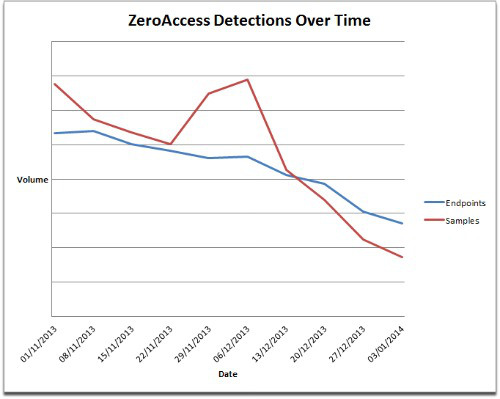
The ZeroAccess botnet has undoubtedly received the most devastating blow it has ever experienced during its lifetime.
It seems that, for now at least, the botnet owners have given up, with no new plugins being pushed into the P2P network and no new droppers released onto the internet.
The owners still have the capability to try to make the botnet work again as they can seed new files into the network, but with no new droppers being pushed the size of the botnet is rapidly decreasing.
It seems Microsoft’s strategy has been very successful against ZeroAccess, indeed, it was one of the actions we suggested in our paper of 2012 – The ZeroAccess Botnet: Mining and Fraud for Massive Financial Gain.
I am hopeful that we will also see arrests, but if those responsible manage to evade capture then it seems likely that the next step in ZeroAccess’ evolution will be a new version of the P2P protocol and perhaps a new plugin architecture that is less reliant on fixed server addresses for its operation.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/29avvlVZrbo/
